Microsoft on Monday attributed a China-based cyber espionage actor to a set of assaults concentrating on diplomatic entities in South America.
The tech big’s Safety Intelligence workforce is monitoring the cluster beneath the rising moniker DEV-0147, describing the exercise as an “growth of the group’s information exfiltration operations that historically focused authorities businesses and assume tanks in Asia and Europe.”
The menace actor is claimed to make use of established hacking instruments reminiscent of ShadowPad to infiltrate targets and preserve persistent entry.
ShadowPad, additionally known as PoisonPlug, is a successor to the PlugX distant entry trojan and has been extensively put to make use of by Chinese language adversarial collectives with hyperlinks to the Ministry of State Safety (MSS) and Folks’s Liberation Military (PLA), per Secureworks.
One of many different malicious instruments utilized by DEV-0147 is a webpack loader known as QuasarLoader, which permits for deploying extra payloads onto the compromised hosts.
Redmond didn’t disclose the tactic DEV-0147 could be utilizing to realize preliminary entry to a goal setting. That stated, phishing and opportunistic concentrating on of unpatched functions are the probably vectors.
“DEV-0147’s assaults in South America included post-exploitation exercise involving the abuse of on-premises identification infrastructure for recon and lateral motion, and using Cobalt Strike for command-and-control and information exfiltration,” Microsoft stated.
DEV-0147 is much from the one China-based superior persistent menace (APT) to leverage ShadowPad in latest months.
In September 2022, NCC Group unearthed particulars of an assault aimed toward an unnamed group that abused a important flaw in WSO2 (CVE-2022-29464, CVSS rating: 9.8) to drop internet shells and activate an an infection chain that led to the supply of ShadowPad for intelligence gathering.
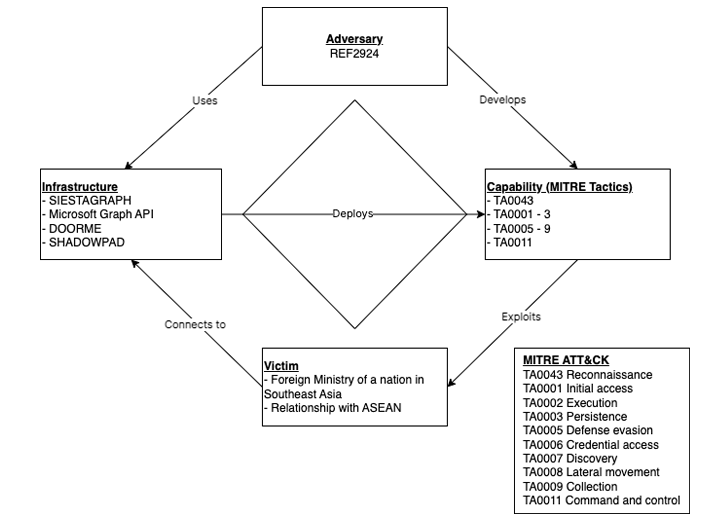
ShadowPad has additionally been employed by unidentified menace actors in an assault concentrating on an ASEAN member overseas ministry via the profitable exploitation of a weak, and Web-connected, Microsoft Change Server.
The exercise, dubbed REF2924 by Elastic Safety Labs, has been noticed to share tactical associations with these adopted by different nation-state teams reminiscent of Winnti (aka APT41) and ChamelGang.
“The REF2924 intrusion set […] represents an assault group that seems centered on priorities that, when noticed throughout campaigns, align with a sponsored nationwide strategic curiosity,” the corporate famous.
The truth that Chinese language hacking teams proceed to make use of ShadowPad regardless of it being well-documented through the years suggests the method is yielding some success.