A pair of reviews from cybersecurity corporations SEKOIA and Development Micro sheds mild on a brand new marketing campaign undertaken by a Chinese language risk actor named Fortunate Mouse that includes leveraging a trojanized model of a cross-platform messaging app to backdoor programs.
An infection chains leverage a chat utility referred to as MiMi, with its installer information compromised to obtain and set up HyperBro samples for the Home windows working system and rshell artifacts for Linux and macOS.
As many as 13 totally different entities positioned in Taiwan and the Philippines have been on the receiving finish of the assaults, eight of whom have been hit with rshell. The primary sufferer of rshell was reported in mid-July 2021.
Fortunate Mouse, additionally referred to as APT27, Bronze Union, Emissary Panda, and Iron Tiger, is thought to be lively since 2013 and has a historical past of having access to focused networks in pursuit of its political and army intelligence-collection targets aligned with China.
The superior persistent risk actor (APT) can be adept at exfiltrating high-value info utilizing a variety of customized implants corresponding to SysUpdate, HyperBro, and PlugX.
The most recent improvement is critical, not least as a result of it marks the risk actor’s introductory try at concentrating on macOS alongside Home windows and Linux.
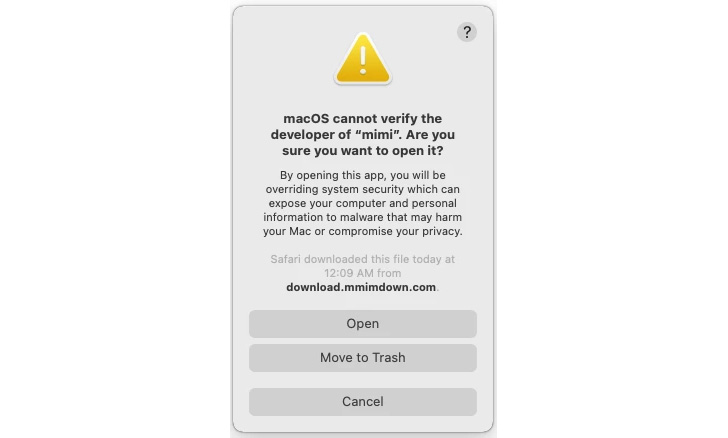
The marketing campaign has all of the hallmarks of a provide chain assault in that the backend servers internet hosting the app installers of MiMi are managed by Fortunate Mouse, thus making it potential to tweak the app to retrieve the backdoors from a distant server.
That is borne out by the truth that the app’s macOS model 2.3.0 was tampered to insert the malicious JavaScript code on Might 26, 2022. Whereas this may increasingly have been the primary compromised macOS variant, variations 2.2.0 and a couple of.2.1 constructed for Home windows have been discovered to include comparable additions as early as November 23, 2021.
rshell, for its half, is a normal backdoor that comes with all the standard bells-and-whistles, permitting for the execution of arbitrary instructions acquired from a command-and-control (C2) server and transmitting the outcomes of the execution again to the server.
It isn’t instantly clear if MiMi is a legit chat program, or if it was “designed or repurposed as a surveillance software,” though the app has been utilized by one other Chinese language-speaking actor dubbed Earth Berberoka (aka GamblingPuppet) aimed toward on-line playing websites – as soon as once more indicative of the prevalent software sharing amongst Chinese language APT teams.
The operation’s connections to Fortunate Mouse stems from hyperlinks to instructure beforehand recognized as utilized by the China-nexus intrusion set and the deployment of HyperBro, a backdoor completely put to make use of by the hacker group.
As SEKOIA factors out, this isn’t the primary time the adversary has resorted to using a messaging app as a jumping-off level in its assaults. In late 2020, ESET disclosed {that a} well-liked chat software program referred to as Ready Desktop was abused to ship HyperBro, PlugX, and a distant entry trojan referred to as Tmanger concentrating on Mongolia.