A Chinese language superior persistent risk (APT) often called Gallium has been noticed utilizing a beforehand undocumented distant entry trojan in its espionage assaults focusing on corporations working in Southeast Asia, Europe, and Africa.
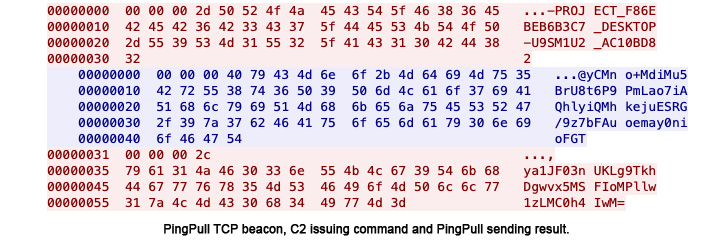
Known as PingPull, the “difficult-to-detect” backdoor is notable for its use of the Web Management Message Protocol (ICMP) for command-and-control (C2) communications, in keeping with new analysis printed by Palo Alto Networks Unit 42 in the present day.
Gallium is understood for its assaults primarily aimed toward telecom corporations relationship way back to 2012. Additionally tracked underneath the title Gentle Cell by Cybereason, the state-sponsored actor has been linked to a broader set of assaults focusing on 5 main telecom corporations situated in Southeast Asian nations since 2017.
Over the previous 12 months, nonetheless, the group is alleged to have expanded its victimology footprint to incorporate monetary establishments and authorities entities situated in Afghanistan, Australia, Belgium, Cambodia, Malaysia, Mozambique, the Philippines, Russia, and Vietnam.
PingPull, a Visible C++-based malware, offers a risk actor the power to entry a reverse shell and run arbitrary instructions on a compromised host. This encompasses finishing up file operations, enumerating storage volumes, and timestomping information.
“PingPull samples that use ICMP for C2 communications challenge ICMP Echo Request (ping) packets to the C2 server,” the researchers detailed. “The C2 server will reply to those Echo requests with an Echo Reply packet to challenge instructions to the system.”
Additionally recognized are PingPull variants that depend on HTTPS and TCP to speak with its C2 server as an alternative of ICMP and over 170 IP addresses related to the group since late 2020.
It is not instantly clear how the focused networks are breached, though the risk actor is understood to use internet-exposed purposes to realize an preliminary foothold and deploy a modified model of the China Chopper net shell to determine persistence.
“Gallium stays an lively risk to telecommunications, finance and authorities organizations throughout Southeast Asia, Europe and Africa,” the researchers famous.
“Whereas using ICMP tunneling will not be a brand new method, PingPull makes use of ICMP to make it tougher to detect its C2 communications, as few organizations implement inspection of ICMP site visitors on their networks.”