The speed at which builders leaked crucial software program secrets and techniques, similar to passwords and API keys, jumped by half to succeed in 5.5 out of each 1,000 commits to GitHub repositories.
That is in response to a report revealed by secrets-management agency GitGuardian this week. Although the share appears small, total, the agency detected not less than 10 million situations of secrets and techniques leaking to a public repository, accounting for greater than 3 million distinctive secrets and techniques in whole, the corporate acknowledged in its “2022 State of Secrets and techniques Sprawl” report.
Whereas generic passwords accounted for almost all (56%) of secrets and techniques, greater than a 3rd (38%) concerned a high-entropy secret that features API keys, random quantity generator seeds, and different delicate strings.
As extra firms transfer their utility infrastructure and operations to the cloud, API keys, credentials, and different software program secrets and techniques have turn into crucial to the safety of their enterprise. When these secrets and techniques leak, the outcomes may be devastating, or on the very least, costly.
“Secrets and techniques are the crown jewels of any enterprise or group — they actually can grant entry into all your methods and infrastructure,” says Mackenzie Jackson, safety and developer advocate at GitGuardian. “The danger may be something, from full system takeovers, to small knowledge exposures, or numerous different issues.”
“Hundreds of thousands of such keys accumulate yearly, not solely in public areas, similar to code-sharing platforms, however particularly in closed areas similar to personal repositories or company IT property,” GitGuardian acknowledged in its “2022 State of Secrets and techniques Sprawl” report.
And even these personal areas may be weak. In January, as an example, collaboration and messaging platform Slack warned customers {that a} “restricted variety of Slack worker tokens” had been stolen by a menace actor, who then downloaded personal code repositories. Final Could, cloud utility platform supplier Heroku, a subsidiary of Salesforce, acknowledged that an attacker had stolen a database of hashed and salted password after getting access to the OAuth tokens used to combine with GitHub.
Infrastructure — as … Whoops!
A part of the rationale for the rise in leaking secrets and techniques is as a result of infrastructure-as-code (IaC) has turn into rather more widespread. IaC is the managing and provisioning of infrastructure by means of code as a substitute of by means of handbook processes, and in 2022, the variety of IaC-related information and artifacts pushed to GitHub repositories elevated by 28%. The overwhelming majority (83%) of information consisting of configuration information for Docker, Kubernetes, or Terraform, in response to GitGuardian.
IaC permits builders to specify the configuration of the infrastructure utilized by their utility, together with servers, databases, and software-defined networking. To manage all these parts, secrets and techniques are sometimes crucial, Jackson says.
“The assault floor retains increasing,” he says. “Infrastructure-as-code has turn into this new factor and it is exploded with recognition, and infrastructure wants secrets and techniques, so infrastructure-as-code [files] typically incorporates secrets and techniques.”
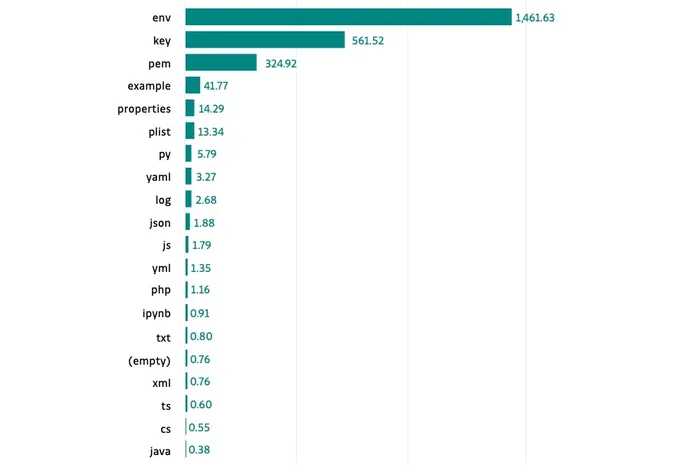
As well as, three filetypes generally used as caches for delicate utility data — .env, .key, and .pem — are thought-about probably the most delicate, outlined as having probably the most secrets and techniques per file. Builders ought to virtually all the time keep away from publishing these information to a public repository, Jackson says.
“If certainly one of these information is in your Git repository, then you realize you have got holes in your safety,” he says. “Even when the file would not include secrets and techniques, they only ought to by no means be there. It is best to have prevention in place to ensure that they are not there and alerting in place to know when they’re there.”
For that motive, firms ought to constantly scan methods and information for secrets and techniques, gaining visibility and skill to dam potential harmful information, Jackson provides.
“You need to scan all your infrastructure to ensure you have visibility” he says. “After which the subsequent steps embrace implementing instruments to test engineers and builders … to detect any secrets and techniques after they slip out.”


