I discovered a doozie right here women and gents, with a bit of python script known as BruteDum. It makes use of Hydra, Medusa and Ncrack to bruteforce numerous community protocols corresponding to SSH, FTP, Telnet, PostgreSQL, RDP and VNC. Pair this instrument together with your favourite enumeration instrument and you’ve got your self a really highly effective penetration testing instrument, Or not.
I had alot of points with this instrument once I began researching it. Principally as a result of all the things on GitHub was deleted or incorrect and the dev simply ghosted. Not a giant deal if you already know what to search for and I used to be truly in a position to get this instrument up and working on my WSL set up of Kali linux
BruteDum Set up
Whereas this instrument seems like it will be nice so as to add to your hacking arsenal, have enjoyable attempting to get it to work. Al of the walkthroughs have been eliminated, the set up script has a typo so attempt to not comply with that. All attachments, hyperlinks and screenshots have been eliminated and the dev is unresponsive. So I took issues into my very own arms for the aim of this text.
git clone https://github.com/RockNRolla/BruteDum cd BruteDum python3 brutedum.pyAfter tweaking the brutedum script a bit of I used to be in a position to get the script put in on my machine. My recommendation is copy the code from GitHub and make the modifications wanted. You’ll be able to import a brand new module and have a proxy added if want be. After working the command I got here up with this:
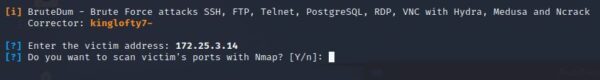
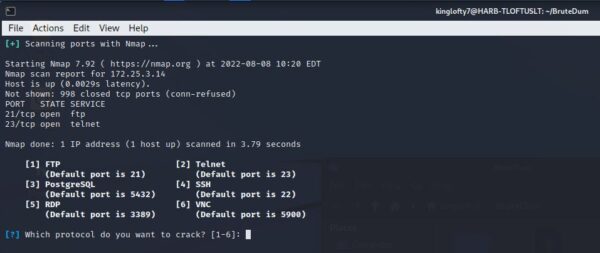
Then was in a position to run an nmap scan on the goal with not many results- one thing that will also be modified within the script if you understand how. After the nmap scan i used to be requested to decide on a protocol to assault. I created a wordlist and caught it in the identical listing, however this system couldn’t discover a path to execute. If you already know the username and have a password record your in luck.
Conclusion
This instrument is nice for some unfinished work. Positively a variety of modifications must be made however when you mess around with it for a number of days you may truly get a good working instrument, additionally you may add different nmap modules pretty straightforward in order that’s a plus. However the truth that I needed to do all that work drops this instrument ranking to a 1 out of 5 bunnies.

Wish to be taught extra about moral hacking?
Now we have a networking hacking course that’s of an identical degree to OSCP, get an unique low cost right here
Assist assist LHN by shopping for a T-shirt or a mug?
Take a look at our choice right here
Are you aware of one other GitHub associated hacking instrument?
Get in contact with us through the contact type if you need us to have a look at some other GitHub moral hacking instruments.