Luring victims utilizing a realistic- and legitimate-looking pretend browser window to steal Steam accounts, this new sort of social engineering could also be an indication of issues to come back.
Luring victims utilizing a realistic- and legitimate-looking pretend browser window to steal Steam accounts, this new sort of social engineering could also be an indication of issues to come back.
I’ve lengthy written about impersonated manufacturers, pretend web sites, and spoofed logon pages in numerous phishing scams and assaults. However this one separates itself a level of sophistication larger than something you’ve seen to date, probably resetting the bar for future social engineering assaults.
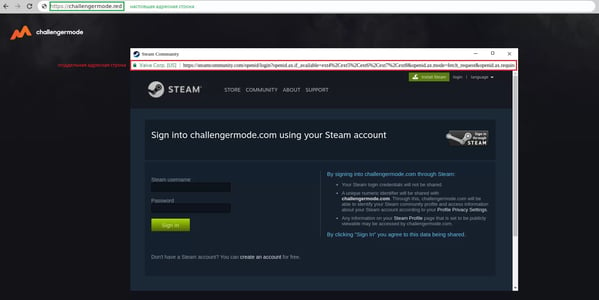
In response to safety researchers at GroupIB, the brand new method – dubbed “Browser-in-the-Browser” – pops up wanting like a brand new window used for authentication; solely it’s truly a part of the preliminary malicious web site. Within the instance beneath, customers of the gaming platform Steam are messaged with interesting Steam-related provides (comparable to collaborating in a event) that may doubtless require authenticating to Steam. As soon as on the web page with the supposed provide, a brand new window seems to pop-up asking the person to authenticate.
Supply: GroupIB
Take a look at the main points within the screenshot – what seems to be like a sound URL is place within the “window” together with a inexperienced lock, indicating a correct SSL cert. In the event you didn’t know higher (and now you do), you’d assume it was authentic. What’s truly occurring is there isn’t a new window; it’s only a very impressively-designed in-site web page that collects credentials and even extra “home windows” for two-factor authentication wants.
What makes this assault so very harmful is its’ potential. Take into consideration anytime you employ third-party authentication (comparable to Google, Fb, Microsoft 365, or any cloud-based listing service) – this identical method might be used to trick customers into offering enterprise credentials.
The reply right here isn’t to inform customers “all the time double-check it’s an actual window” – that’s not the problem; what is sweet recommendation (which is taught as a part of continuous Safety Consciousness Coaching) is to by no means interact with unsolicited messages (whether or not throughout electronic mail, social media, or in-platform messaging of any type), as cybercriminals are all the time on the lookout for new (and do I must say progressive after you’ve learn all this?) methods to idiot you out of your credentials.