Microleaves, a ten-year-old proxy service that lets clients route their net site visitors via tens of millions of Microsoft Home windows computer systems, just lately mounted a vulnerability of their web site that uncovered their total person database. Microleaves claims its proxy software program is put in with person consent, however information uncovered within the breach exhibits the service has a prolonged historical past of being provided with new proxies by associates incentivized to distribute the software program any which manner they’ll — corresponding to by secretly bundling it with different titles.

The Microleaves proxy service, which is within the strategy of being rebranded to Shifter[.[io.
Launched in 2013, Microleaves is a service that allows customers to route their Internet traffic through PCs in virtually any country or city around the globe. Microleaves works by changing each customer’s Internet Protocol (IP) address every five to ten minutes.
The service, which accepts PayPal, Bitcoin and all major credit cards, is aimed primarily at enterprises engaged in repetitive, automated activity that often results in an IP address being temporarily blocked — such as data scraping, or mass-creating new accounts at some service online.
In response to a report about the data exposure from KrebsOnSecurity, Microleaves said it was grateful for being notified about a “very serious issue regarding our customer information.”
Abhishek Gupta is the PR and marketing manager for Microleaves, which he said in the process of being rebranded to “Shifter.io.” Gupta said the report qualified as a “medium” severity security issue in Shifter’s brand new bug bounty program (the site makes no mention of a bug bounty), which he said offers up to $2,000 for reporting data exposure issues like the one they just fixed. KrebsOnSecurity declined the offer and requested that Shifter donate the amount to the Electronic Frontier Foundation (EFF), a digital rights group.
From its inception nearly a decade ago, Microleaves has claimed to lease between 20-30 million IPs via its service at any time. Riley Kilmer, co-founder of the proxy-tracking service Spur.us, said that 20-30 million number might be accurate for Shifter if measured across a six-month time frame. Currently, Spur is tracking roughly a quarter-million proxies associated with Microleaves/Shifter each day, with a high rate of churn in IPs.
Early on, this rather large volume of IP addresses led many to speculate that Microleaves was just a botnet which was being resold as a commercial proxy service.
The very first discussion thread started by the new user Microleaves on the forum BlackHatWorld in 2013 sought forum members who could help test and grow the proxy network. At the time, the Microleaves user said their proxy network had 150,000 IPs globally, and was growing quickly.
One of BlackHatWorld’s moderators asked the administrator of the forum to review the Microleaves post.
“User states has 150k proxies,” the forum skeptic wrote. “No seller on BHW has 150k working daily proxies none of us do. Which hints at a possible BOTNET. That’s the only way you will get 150k.”
Microleaves has long been classified by antivirus companies as adware or as a “potentially unwanted program” (PUP), the euphemism that antivirus companies use to describe executable files that get installed with ambiguous consent at best, and are often part of a bundle of software tied to some “free” download. Security vendor Kaspersky flags the Microleaves family of software as a trojan horse program that commandeers the user’s Internet connection as a proxy without notifying the user.
“While working, these Trojans pose as Microsoft Windows Update,” Kaspersky wrote.
In a February 2014 post to BlackHatWorld, Microleaves announced that its sister service — reverseproxies[.]com — was now providing an “Auto CAPTCHA Fixing Service,” which automates the fixing of these squiggly and generally irritating puzzles that many web sites use to tell apart bots from actual guests. The CAPTCHA service was provided as an add-on to the Microleaves proxy service, and ranged in value from $20 for a 2-day trial to $320 for fixing as much as 80 captchas concurrently.
“We break regular Recaptcha with 60-90% success fee, recaptcha with blobs 30% success, and 500+ different captcha,” Microleaves wrote. “As all success fee on recaptcha relies upon very a lot on good proxies which can be contemporary and never spammed!”
WHO IS ACIDUT?
The uncovered Microleaves person database exhibits that the primary person created on the service — username “admin” — used the e-mail tackle alex.iulian@aol.com. A search on that e mail tackle in Constella Intelligence, a service that tracks breached information, reveals it was used to create an account on the hyperlink shortening service bit.ly beneath the title Alexandru Florea, and the username “Acidut.” [Full disclosure: Constella is currently an advertiser on this website].
Based on the cyber intelligence firm Intel 471, a person named Acidut with the e-mail tackle iulyan87_4u@gmail.com had an lively presence on virtually a dozen shadowy money-making and cybercrime boards from 2010 to 2017, together with BlackHatWorld, Carder[.]professional, Hackforums, OpenSC, and CPAElites.
The person Microleaves (later “Shifter.io”) marketed on BlackHatWorld the sale of 31 million residential IPs to be used as proxies, in late 2013. The identical account continues to promote subscriptions to Shifter.io.
In a 2011 publish on Hackforums, Acidut mentioned they have been constructing a botnet utilizing an “exploit package,” a set of browser exploits made to be stitched into hacked web sites and foist malware on guests. Acidut claimed their exploit package was producing 3,000 to five,000 new bots every day. OpenSC was hacked at one level, and its non-public messages present Acidut bought a license from Exmanoize, the deal with utilized by the creator of the Eleonore Exploit Package.
By November 2013, Acidut was promoting the sale of “26 million SOCKS residential proxies.” In a March 2016 publish to CPAElites, Acidut mentioned they’d a worthwhile supply for folks concerned in pay-per-install or “PPI” schemes, which match felony gangs who pay for malware installs with enterprising hackers trying to promote entry to compromised PCs and web sites.
As a result of pay-per-install affiliate schemes hardly ever impose restrictions on how the software program might be put in, such packages might be interesting for cybercriminals who already management massive collections of hacked machines and/or compromised web sites. Certainly, Acidut went a step additional, including that their program could possibly be quietly and invisibly nested inside different packages.
“For these of you who’re doing PPI I’ve a worldwide supply that you would be able to bundle to your installer,” Acidut wrote. “I’m in search of many installs for an app that can generate web site visits. The installer has a silence model which you need to use inside your installer. I’m trying to purchase as many day by day installs as attainable worldwide, besides China.”
Requested in regards to the supply of their proxies in 2014, the Microleaves person responded that it was “one thing associated to a PPI community. I can’t say extra and I received’t get into particulars.”
Acidut authored an identical message on the discussion board BlackHatWorld in 2013, the place they inspired customers to contact them on Skype on the username “nevo.julian.” That very same Skype contact tackle was listed prominently on the Microleaves homepage up till a few week in the past when KrebsOnSecurity first reached out to the corporate.
ONLINE[.]IO (NOW MERCIFULLY OFFLINE)
There’s a Fb profile for an Alexandru Iulian Florea from Constanta, Romania, whose username on the social media community is Acidut. Previous to KrebsOnSecurity alerting Shifter of its information breach, the Acidut profile web page related Florea with the web sites microleaves.com, shrooms.io, leftclick[.]io, and on-line[.]io. Mr. Florea didn’t reply to a number of requests for remark, and his Fb web page not mentions these domains.
Leftclick and on-line[.]io emerged as subsidiaries of Microleaves between 2017 and 2018. Based on a assist wished advert posted in 2018 for a developer place at on-line[.]io, the corporate’s providers have been openly pitched to buyers as “a cybersecurity and privateness device package, providing intensive safety utilizing superior adblocking, anti-tracking methods, malware safety, and revolutionary VPN entry based mostly on residential IPs.”

A teaser from Irish Tech Information.
“On-line[.]io is creating the primary totally decentralized peer-to-peer networking expertise and revolutionizing the shopping expertise by making it quicker, advert free, extra dependable, safe and non-trackable, thus releasing the Web from annoying advertisements, malware, and trackers,” reads the remainder of that assist wished advert.
Microleaves CEO Alexandru Florea gave an “interview” to the web site Irishtechnews.ie in 2018, through which he defined how On-line[.]io (OIO) was going to upend the internet advertising and safety industries with its preliminary coin providing (ICO). The phrase interview is in air quotes as a result of the next statements by Florea deserved some severe pushback by the interviewer.
“On-line[.]io resolution, developed utilizing the Ethereum blockchain, goals at disrupting the digital promoting market valued at greater than $1 trillion USD,” Alexandru enthused. “By staking OIO tokens and implementing our resolution, the web site operators will be capable to entry a brand new non-invasive income stream, which capitalizes on time spent by customers on-line.”
“On the similar time, web customers who stake OIO tokens can have the chance to monetize on the time spent on-line by themselves and their friends on the World Broad Internet,” he continued. “The time spent by customers on-line will result in ICE tokens being mined, which in flip can be utilized within the devoted service provider system or traded on exchanges and consequently modified to fiat.”
Translation: In the event you set up our proxy bot/CAPTCHA-solver/advert software program in your pc — or as an exploit package in your web site — we’ll make tens of millions hijacking advertisements and you may be rewarded with heaps of soon-to-be-worthless shitcoin. Oh, and all of your safety woes will disappear, too.
It’s unclear what number of Web customers and web sites willingly agreed to get bombarded with On-line[.]io’s annoying advertisements and search hijackers — and to have their PC became a proxy or CAPTCHA-solving zombie for others. However that’s precisely what a number of safety corporations mentioned occurred when customers encountered on-line[.]io, which operated utilizing the Microsoft Home windows course of title of “online-guardian.exe.”
Extremely, Crunchbase says On-line[.]io raised $6 million in funding for an preliminary coin providing in 2018, based mostly on the plainly ludicrous claims made above. Since then, nonetheless, on-line[.]io appears to have gone…offline, for good.
SUPER TECH VENTURES?
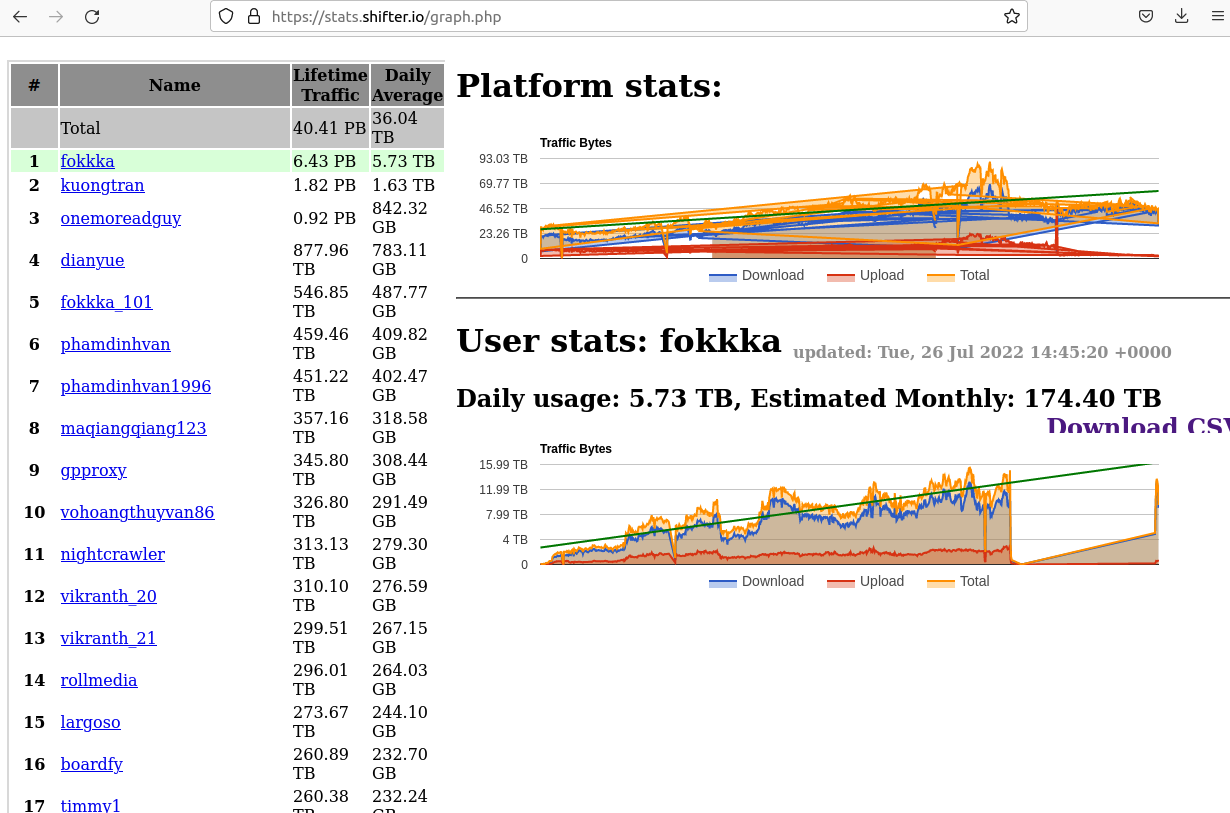
Till this week, Shifter.io’s web site additionally uncovered details about its buyer base and most lively customers, in addition to how a lot cash every consumer has paid over the lifetime of their subscription. The information signifies Shifter has earned greater than $11.7 million in direct funds, though it’s unclear how far again in time these fee data go, or how full they’re.
The majority of Shifter clients who spent greater than $100,000 on the proxy service look like digital promoting corporations, together with some situated in the USA. Not one of the a number of Shifter clients approached by KrebsOnSecurity agreed to be interviewed.
Shifter’s Gupta mentioned he’d been with the corporate for 3 years, because the new proprietor took over the corporate and made the rebrand to Shifter.
“The corporate has been available on the market for a very long time, however operated beneath a unique model referred to as Microleaves, till new possession and administration took over the corporate began a reorganization course of that’s nonetheless on-going,” Gupta mentioned. “We’re totally clear. Principally [our customers] work within the information scraping area of interest, for this reason we really developed extra merchandise on this zone and made a giant shift in the direction of APIs and built-in options previously 12 months.”
Ah sure, the identical APIs and built-in options that have been discovered uncovered to the Web and leaking all of Shifter’s buyer data.
Gupta mentioned the unique founding father of Microleaves was a person from India, who later offered the enterprise to Florea. Based on Gupta, the Romanian entrepreneur had a number of points in making an attempt to run the corporate, after which offered it three years in the past to the present proprietor — Tremendous Tech Ventures, a non-public fairness firm based mostly in Taiwan.
“Our CEO is Wang Wei, he has been with the corporate since 3 years in the past,” Gupta mentioned. “Mr. Florea left the corporate two years in the past after ending this transition interval.”
Google and different search engines like google and yahoo appear to know nothing a few Tremendous Tech Ventures based mostly in Taiwan. Extremely, Shifter’s personal PR individual claimed that he, too, was at midnight on this topic.
“I’d love to assist, however I actually don’t know a lot in regards to the mom firm,” Gupta mentioned, basically strolling again his “totally clear” assertion. “I do know they’re a department of the larger group of asian funding companies centered on non-public fairness in a number of industries.”
Adware and proxy software program are sometimes bundled along with “free” software program utilities on-line, or with well-liked software program titles which were pirated and quietly fused with installers tied to numerous PPI affiliate schemes.
However simply as usually, these intrusive packages will embody some sort of discover — even when put in as a part of a software program bundle — that many customers merely don’t learn and click on “Subsequent” to get on with putting in no matter software program they’re looking for to make use of. In these circumstances, choosing the “fundamental” or “default” settings whereas putting in often hides any per-program set up prompts, and assumes you conform to the entire bundled packages being put in. It’s at all times greatest to go for the “customized” set up mode, which can provide you a greater concept of what’s really being put in, and might allow you to management sure features of the set up.
Both manner, it’s greatest to start out with the belief that if a software program or service on-line is “free,” that there’s possible some part concerned that enables the supplier of that service to monetize your exercise. As KrebsOnSecurity famous on the conclusion of final week’s story on a China-based proxy service referred to as 911, the rule of thumb for transacting on-line is that if you happen to’re not the paying buyer, then you definately and/or your units are in all probability the product that’s being offered to others.
Additional studying on proxy providers:
July 18, 2022: A Deep Dive Into the Residential Proxy Service ‘911’
June 28, 2022: The Hyperlink Between AWM Proxy & the Glupteba Botnet
June 22, 2022: Meet the Directors of the RSOCKS Proxy Botnet
Sept. 1, 2021: 15-12 months-Previous Malware Proxy Community VIP72 Goes Darkish
Aug. 19, 2019: The Rise of “Bulletproof” Residential Networks