The operators behind BRATA have as soon as once more added extra capabilities to the Android cellular malware in an try to make their assaults towards monetary apps extra stealthy.
“In truth, the modus operandi now suits into an Superior Persistent Menace (APT) exercise sample,” Italian cybersecurity agency Cleafy stated in a report final week. “This time period is used to explain an assault marketing campaign by which criminals set up a long-term presence on a focused community to steal delicate info.”
An acronym for “Brazilian Distant Entry Instrument Android,” BRATA was first detected within the wild in Brazil in late 2018, earlier than making its first look in Europe final April, whereas masquerading as antivirus software program and different frequent productiveness instruments to trick customers into downloading them.
The change within the assault sample, which scaled new highs in early April 2022, includes tailoring the malware to strike a particular monetary establishment at a time, switching to a special financial institution solely after the sufferer begins implementing countermeasures towards the menace.
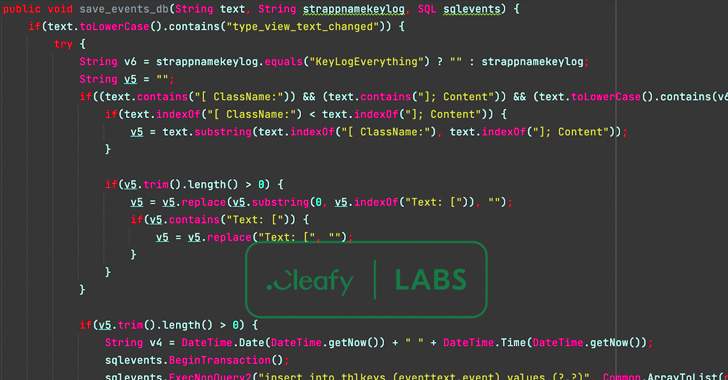
Additionally included within the rogue apps are new options that allow it to impersonate the login web page of the monetary establishment to reap credentials, entry SMS messages, and sideload a second-stage payload (“unrar.jar”) from a distant server to log occasions on the compromised system.
“The mixture of the phishing web page with the chance to obtain and browse the sufferer’s sms might be used to carry out an entire Account Takeover (ATO) assault,” the researchers stated.
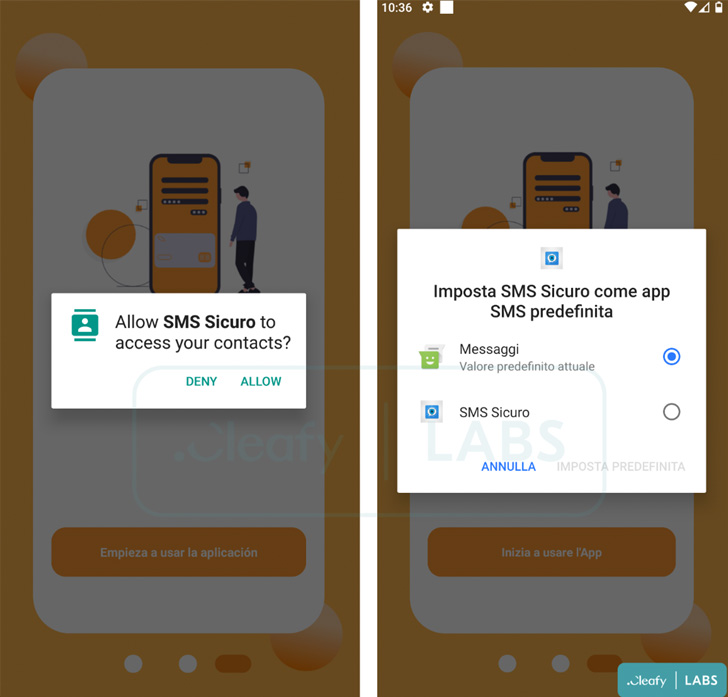
Moreover, Cleafy stated it discovered a separate Android app package deal pattern (“SMSAppSicura.apk”) that used the identical command-and-control (C2) infrastructure as BRATA to siphon SMS messages, indicating that the menace actors are testing out completely different strategies to develop their attain.
The SMS stealer app is claimed to be particularly singling out customers within the U.Okay., Italy, and Spain, its aim with the ability to intercept and exfiltrate all incoming messages associated to one-time passwords despatched by banks.
“The primary campaigns of malware had been distributed by faux antivirus or different frequent apps, whereas in the course of the campaigns the malware is taking the flip of an APT assault towards the shopper of a particular Italian financial institution,” the researchers stated.
“They often concentrate on delivering malicious purposes focused to a particular financial institution for a few months, after which transferring to a different goal.”