A financially motivated risk actor tracked as Blind Eagle has resurfaced with a refined toolset and an elaborate an infection chain as a part of its assaults focusing on organizations in Colombia and Ecuador.
Examine Level’s newest analysis affords new insights into the Spanish-speaking group’s techniques and methods, together with using subtle instruments and government-themed lures to activate the killchain.
Additionally tracked beneath the identify APT-C-36, Blind Eagle is notable for its slender geographical focus and launching indiscriminate assaults in opposition to South American nations since no less than 2018.
Blind Eagle’s operations have been documented by Pattern Micro in September 2021, uncovering a spear-phishing marketing campaign primarily aimed toward Colombian entities designed to ship a commodity malware referred to as BitRAT, with a lesser focus in direction of targets in Ecuador, Spain, and Panama.
Assaults chains start with phishing emails containing a booby-trapped hyperlink that, when clicked, results in the deployment of an open supply trojan named Quasar RAT with the final word aim of getting access to the sufferer’s financial institution accounts.
A few of focused banks consists of Banco AV Villas, Banco Caja Social, Banco de Bogotá, Banco Standard, Bancoomeva, BBVA, Colpatria, Davivienda, and TransUnion.
Ought to the e-mail recipient be positioned exterior of Colombia, the assault sequence is aborted and the sufferer is redirected to the official web site of the Colombian border management company, Migración Colombia.
A associated marketing campaign singling out each Colombia and Ecuador masquerades because the latter’s Inside Income Service (SRI) and makes use of an identical geo-blocking know-how to filter out requests originating from different international locations.
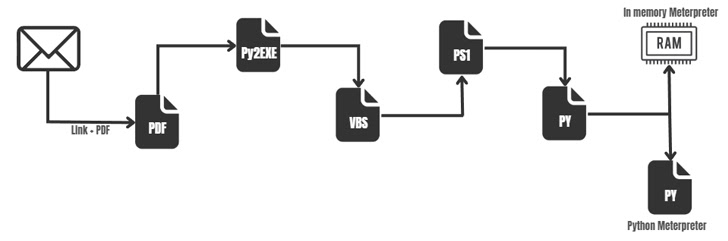
This assault, slightly than dropping a RAT malware, employs a extra advanced multi-stage course of that abuses the professional mshta.exe binary to execute VBScript embedded inside an HTML file to in the end obtain two Python scripts.
The primary of the 2, ByAV2.py, is an in-memory loader engineered to run a Meterpreter payload in DLL format. mp.py can also be a Meterpreter artifact, solely it is programmed in Python, indicating that the risk actor might be utilizing one in every of them as a redundant methodology to retain backdoor entry to the host.
“Blind Eagle is a wierd chicken amongst APT teams,” the researchers concluded. “Judging by its toolset and normal operations, it’s clearly extra fascinated by cybercrime and financial acquire than in espionage.”
The event comes days after Qualys disclosed that an unknown adversary is leveraging private data stolen from a Colombian cooperative financial institution to craft phishing emails that end result within the deployment of BitRAT.