The menace actors behind the Black Basta ransomware household have been noticed utilizing the Qakbot trojan to deploy the Brute Ratel C4 framework as a second-stage payload in latest assaults.
The event marks the primary time the nascent adversary simulation software program is being delivered through a Qakbot an infection, cybersecurity agency Development Micro stated in a technical evaluation launched final week.
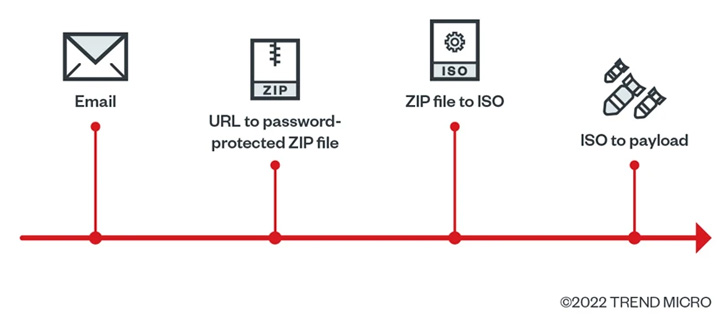
The intrusion, achieved utilizing a phishing e mail containing a weaponized hyperlink pointing to a ZIP archive, additional entailed using Cobalt Strike for lateral motion.
Whereas these professional utilities are designed for conducting penetration testing actions, their capability to supply distant entry has made them a profitable software within the palms of attackers seeking to stealthily probe the compromised surroundings with out attracting consideration for prolonged durations of time.
This has been compounded by the truth that a cracked model of Brute Ratel C4 started circulating final month throughout the cybercriminal underground, prompting its developer to replace the licensing algorithm to make it more durable to crack.
Qakbot, additionally referred to as QBot and QuackBot, is an data stealer and banking trojan that is identified to be energetic since 2007. However its modular design and its capability to behave as a downloader has turned it into a pretty candidate for dropping extra malware.
In response to Development Micro, the ZIP file within the e mail accommodates an ISO file, which, in flip, features a LNK file that fetches the Qakbot payload, illustrating makes an attempt on a part of menace actors to adapt to different ways within the aftermath of Microsoft’s choice to dam macros by default for paperwork downloaded from the net.
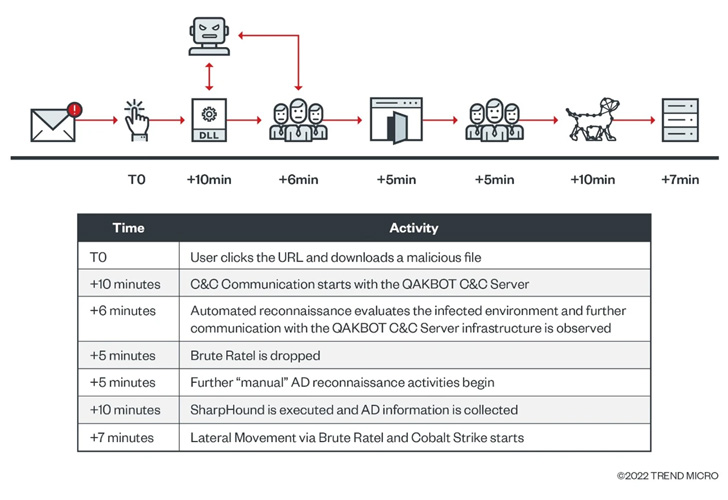
The Qakbot an infection is succeeded by the retrieval of Brute Ratel and Cobalt Strike, however not earlier than performing automated reconnaissance by way of built-in command line instruments similar to arp, ipconfig, nslookup, netstat, and whoami.
The assault, nevertheless, was stopped earlier than any malicious motion could possibly be taken by the menace actor, though it is suspected that the top objective might have been domain-wide ransomware deployment.
In one other Qakbot execution chain noticed by the cybersecurity firm, the ZIP file is delivered by way of an more and more common technique referred to as HTML smuggling, ensuing within the execution of Brute Ratel C4 because the second-stage.
“The Qakbot-to-Brute Ratel-to-Cobalt Strike kill chain is related to the group behind the Black Basta Ransomware,” the researchers stated. “That is primarily based on overlapping TTPs and infrastructure noticed in Black Basta assaults.”
The findings coincide with a resurgence of Qakbot assaults in latest months via a wide range of methods like HTML file attachments, DLL side-loading, and e mail thread hijacking, the final of which entailed harvesting emails in bulk from profitable ProxyLogon assaults aimed toward Microsoft Alternate servers.
IcedID Actors Diversify Supply Strategies
Qakbot is much from the one access-as-a-service malware that is being more and more distributed through ISO and different file codecs to get round macro restrictions, for Emotet, IcedID, and Bumblebee campaigns have all adopted related trajectories.
Palo Alto Networks Unit 42, in late September 2022, stated it found a malicious polyglot Microsoft Compiled HTML Assist (CHM) file getting used to ship the IcedID (aka BokBot) malware.
Different distinguished supply strategies and an infection pathways have concerned using password-protected ZIP information containing an ISO file, mirroring that of Qakbot, with the payload propagated by way of a pay-per-installer service often called PrivateLoader, in accordance with Workforce Cymru.
And, to high all of it, Emotet seems to be readying for a recent set of assaults after a brief three-month hiatus to transform its “systeminfo” module to “enhance focusing on of particular victims and distinguish monitoring bots from actual customers,” ESET disclosed in a collection of tweets.
“Now we have not seen new spam waves from Emotet since July,” Jean-Ian Boutin, director of menace analysis at ESET, informed The Hacker Information. “It’s not clear why that’s.”
“They did take some breaks prior to now, however by no means for that lengthy. Maybe this new module implies that they’re testing modules and will likely be energetic once more within the close to future, however this after all is concept.”