Some current Steam account phishing assaults attempt to lure in unsuspecting customers with personal messages providing discounted esports occasion tickets, alternatives to affix esports tournaments, or the prospect to vote for a consumer’s favourite esports crew. Some menace actors arrange gaming livestreams much like the current cryptocurrency rip-off livestreams. Fairly than providing free cryptocurrency, these gaming livestreams promote free in-game character customization gadgets. All of those completely different presents embody hyperlinks to web sites managed by menace actors. These web sites are made to look respectable and direct customers to say a suggestion by logging into Steam. Nonetheless, the Steam login home windows that seem when customers comply with these prompts usually are not actual home windows.
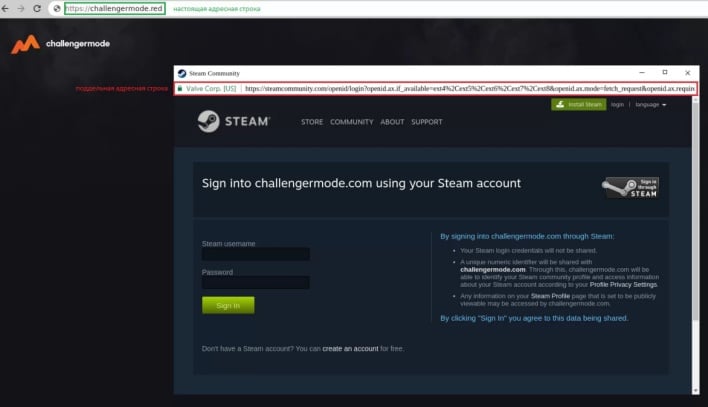
BITB assaults have now graduated from proof of idea to actuality, as menace actors are utilizing this system of their phishing assaults on Steam accounts. The picture above reveals an instance of an interactive faux Steam login window on a phishing webpage. Customers can transfer the window round contained in the confines of the net browser and alter the language of the login web page. The faux web page can detect if a consumer’s account has two-factor authentication (2FA) enabled. If that’s the case, the window will replace with a immediate asking for a 2FA code.
All login credentials entered into this faux window are despatched to the menace actor’s command-and-control (C2) server and relayed into Steam, giving the attacker entry to customers’ steam accounts. To be able to keep away from falling sufferer to a BITB assault, customers can carry out a number of checks to see whether or not login home windows are actual or animated. Actual login home windows will seem within the taskbar, have the identical window design because the mum or dad browser, and have a purposeful handle bar. Customers may strive minimizing the window to the duty bar or shifting the window outdoors of the browser. A faux browser window gained’t have the ability to carry out both of those actions. Disabling or blocking javascript is one other protection towards BITB assaults, although doing so will often hinder respectable login portals as properly.


