“Shifting (safety)” left method in Software program Improvement Life Cycle (SDLC) means beginning safety earlier within the course of. As organizations realized that software program by no means comes out completely and are riddled with many exploitable holes, bugs, and enterprise logic vulnerabilities that require going again to repair and patch, they understood that constructing safe software program requires incorporating and consolidating quite a few assets.
This conclusion led DevOps and R&D leaders to develop into proactive, buying expertise to search out and shut these gaps upfront, with the goal of lowering the associated fee and energy whereas enhancing the standard of their outcomes.
With rising complete steady safety validation expertise, the demonstrated advantages of ‘shifting left’ as a basic a part of SDLC can now be utilized to your cybersecurity program, with outcomes far exceeding the purely technical facets of safety posture administration.
On the growth stage, the conceptualization of SDLC is the results of the convergence of quite a few strains of thought to optimize the method. From a cybersecurity perspective, the identical thought convergence course of led to the idea of rolling out a steady safety assurance program by implementing the basics of Prolonged Safety Posture Administration (XSPM) expertise.
The Safety Posture Administration Lifecycle
Like SDLC, XSPM is born out of the necessity to consider your entire safety posture administration lifecycle, together with validation from an offensive perspective. Because the time period ‘shifting left’ was coined, a plethora of detect and response options integrable into the CI/CD course of has emerged. But, even postulating a superbly built-in and optimized superior detection and response software stack, it’ll nonetheless endure from a structural flaw. Detect and reply is a reactive method that leaves the initiative within the arms of the attacker and presupposes the flexibility to detect any and all assaults.
In actuality, the more and more dynamic nature of the cyber-threat panorama and the uneven nature of cyber protection – an attacker solely must succeed as soon as, whereas defenders want to dam each single assault – imply that focusing solely on the reactive detect and response method is akin to combating the final conflict. The time has come to modify to shifting additional left in direction of integrating a proactive steady safety validation course of.
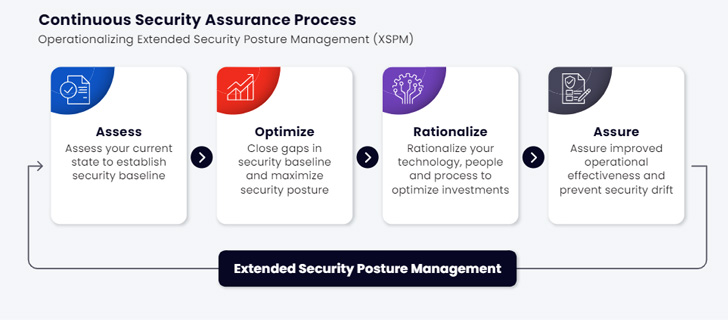
XSPM consists of all the continual safety validation components and organizes them in a safety posture 4 levels lifecycle – Assess, Optimize, Rationalize, Guarantee.
- The ‘Assessing’ step consists of launching a complete set of assaults protecting the assault kill chain from starting to finish.
- The ‘Optimizing’ step identifies misconfigured safety controls, enabling optimizing them to typically compensate for not but patched CVEs and scale back the IT group patching workload.
- The ‘Rationalizing’ step evaluates the efficacy of the detection and response software stack, supplies detailed info to enhance their configuration and identifies overlapping instruments and lacking capabilities.
- The final step, ‘Assuring’, features a dynamic analytic course of that may be custom-made as wanted and used to visualise the safety posture traits over time.
Productiveness tops safety, let’s make safety productive
The optimization of cybersecurity packages as facilitated by XSPM’s framework and expertise supplies for higher utilization of the funds and assets invested in cybersecurity. Decreasing overlap, minimizing patching window, prioritizing workload, setting KPIs, and different advantages immediately outcome from integrating safety early on reasonably than retrospectively.
To realize this mixed optimization of useful resource allocation and safety posture, each safety and threat administration leaders first want to determine a relatable, validated baseline. With information emanating solely from a detect and response array, the fact is an unoptimized sequential course of that pushes the proactive safety validation step in the back of the queue and leads to antagonizing siloed DevOps and SOC groups. Misaligned targets between groups result in a chaotic stream of contradictory info hampering the decision-making course of, slowing down operations and doubtlessly resulting in unsecured deployment.
Combining the 2 for safe software program – the advantages of baking XSPM in SDLC
When safety testing solely kicks in on the finish of the SDLC, the delays prompted in deployment as a result of uncovered essential safety gaps trigger rifts between DevOps and SOC groups. Safety typically will get pushed to the again of the road, and there is not a lot collaboration when introducing a brand new software, or technique, comparable to launching occasional simulated assaults towards the CI/CD pipeline.
Conversely, as soon as a complete steady safety validation method is baked within the SDLC, day by day invoking assault methods emulations via the automation built-in XSPM expertise establish misconfiguration early within the course of, incentivizing shut collaboration between DevSecOps and DevOps. With built-in inter-team collaboration throughout each safety and software program growth lifecycle, working with instant visibility on safety implications, the purpose alignment of each groups eliminates erstwhile strife and friction born of inside politics.
Creating exponential outcomes
Shifting excessive left with complete steady safety validation allows you to start mapping and to grasp the investments made in varied detection and response applied sciences and implementing findings to preempt assault methods throughout the kill chain and defend actual useful necessities.
The method equips IT groups with all they should establish alternatives that solidify and stabilize safety posture administration from the very begin, avoiding pricey delays in deployment and minimizing the danger of profitable breach makes an attempt, whereas SOC groups acquire exact information on which to construct a menace knowledgeable technique.
How are you going to be proactive right this moment about your organization’s safety posture?
Be aware — This text is written and contributed by Ben Zilberman – Product Advertising Director at Cymulate.