ACM.80 Defending information and encryption keys in reminiscence and in use
It is a continuation of my sequence of posts on Automating Cybersecurity Metrics.
Enclaves, Trusted Execution Environments, and Trusted Platform Modules
"I can put no matter I need in that field and you will not even know."
One of many product managers at an organization I used to work for instructed me that the previous head of engineering stated one thing to that impact to him when he was asking for adjustments to a safety product. I wasn’t within the room when this assertion was apparently uttered, so I can’t communicate to the veracity of the matter.
Nonetheless, it does make you concentrate on the safety of software program inside a system with customized {hardware}, many software program elements, and complicated embedded programs programming. How have you learnt that somebody hasn’t inserted some rogue code or {hardware} adjustments into the working system or one of many elements included on the system? In reality, {hardware} vulnerability exploitation is on the rise. Who’s checking and even understands {hardware} vulnerabilities that will exist in programs on which you might be operating your code?
That individual particular person was not joyful that I used to be employed to assist them join their merchandise to the cloud. In my interview he stated to me, “Don’t screw it up.” Very comforting if you’re about to return in and work with an individual on a brand new challenge proper?
Properly, that particular person left the corporate earlier than I got here on board. Mockingly, regardless that he was not joyful about transferring that exact product to the cloud in response to individuals who employed me, he went to work for a cloud supplier after he left. He even instructed me in my interview {that a} totally different cloud present was higher than the one for whom he went to work so I used to be shocked by that transfer.
I don’t actually know that particular person and perhaps his phrases have been misconstrued. I primarily point out that remark to get you enthusiastic about what somebody may put right into a software program or perhaps a {hardware} system when individuals aren’t actually being attentive to all the main points or don’t even perceive the implication of sure implementations inside a system structure. The product supervisor in query definitely wasn’t going to be doing a code or {hardware} evaluate.
Now that particular person, who allegedly indicated that he may “put something within the field” and the product supervisor wouldn’t even know — is working for a serious cloud supplier, and certain on the {hardware} on which your programs function. Hopefully he was simply speaking and he wouldn’t really comply with by way of on that menace, or maybe it was a misunderstanding.
However let’s say there was somebody at a cloud supplier who had malicious intentions. Hopefully AWS has enough processes in place to forestall infiltration of rogue code and {hardware} vulnerabilities. Based mostly on many shows I’ve seen at AWS re:Invent, I believe they do a whole lot of code and structure critiques to forestall safety issues. However what in the event that they miss one thing? What are you able to do about that?
What if somebody slips some code into the working system that permits that particular person to remotely set off actions on an Web-connected VM? Once I began on the safety vendor I assumed — what if somebody tried to insert some code that accessed the AWS credentials on the gadget that have been used to speak with and run instructions AWS in our account? Additionally, the equipment product was examined in China, one thing I advisable towards. What if somebody in China discovered a vulnerability, which now needs to be reported to the Chinese language authorities earlier than telling anybody else in response to a brand new Chinese language legislation?
Or what if malware will get onto your VM after which can entry the info on it? Possibly it’s not a rogue consumer however some vulnerability that permits malware to trigger a system crash that dumps reminiscence — what number of attackers get entry to delicate information. Or maybe they will inject fileless malware right into a course of in reminiscence that may then entry something in reminiscence associated to that course of.
How can we defend towards such potential threats?
Possibly a safe enclave will help. That, after all, relies on the implementation particulars of the enclave.
Architecting a Safe IoT Resolution that leverages encryption keys
I used to be tasked at a safety vendor with architecting an answer to permit firewalls to connect with a cloud supplier. The firewall configurations for a lot of places could possibly be managed by prospects from the cloud and their logs can be saved within the cloud. The group I used to be managing had solely beforehand constructed merchandise with administration interfaces that exist solely in non-public, on-premises networks.
I used to be involved about lack of information of assaults on public dealing with net programs. Because it turned out, this concern was properly based once I discovered that the builders have been utilizing the session ID because the identify of information downloaded from the system. The group later arrange a CORS coverage with a (*) to beat points accessing micro-services from a reverse proxy. The group had a number of issues to study however there have been very succesful. It wasn’t a problem with their skills, simply that I needed to clarify a number of issues to them alongside the best way that that they had not handled earlier than.
Due my issues a couple of distributed, Web-facing system for IOT sensor information and communications, I opted to make use of AWS IOT for gadget connections. By leveraging AWS IOT, builders who labored at AWS would architect one aspect of the answer. They need to have expertise with constructing a safe service within the cloud — greater than my group which had by no means achieved such a factor earlier than.
Though my group was very good and a few have been extra skilled than me in sure points of their product — it was simply riskier to have them construct this out as a result of the Web part and dealing in a shared digital atmosphere was new to them and the corporate was in a rush to make the transfer.
I had restricted time to clarify all the main points I’ve been writing about on this weblog sequence. As you may see I’ve printed posts for 80 days now and nowhere close to near deploying what I got down to deploy as a result of I’m taking the time to clarify all the safety implications, menace mannequin, assault vectors, safety ideas and gotchas alongside the best way. How may I discover the time to clarify all of this to my group and get the challenge achieved within the timeframe the executives wished? Leveraging AWS IOT helped cut back the time it might take to ship the answer and transferred among the safety threat to AWS.
Because it seems, my group needed to rewrite among the embedded programs shopper software program. That’s an space the place a few of them had years of expertise. In accordance with skilled architects on the group, the AWS IoT shopper was extra like a proof of idea {that a} piece of usable working code that could possibly be put into manufacturing. I’m certain it’s higher now, however be sure you have security-conscious, skilled embedded programs programmers if you happen to’re engaged on an IoT resolution.
Defending Non-public Keys with {Hardware}
With AWS IOT units can authenticate to AWS with a certificates.
I clarify uneven and symmetric authentication at a excessive degree within the e-book on the backside of my put up, however primarily for this implementation we used uneven encryption with a public, non-public key pair to authenticate the gadget to AWS and alternate a shared key for symmetric encryption and credentials used for information alternate after that preliminary key alternate.
The factor in regards to the non-public key used for the preliminary key alternate was that if anybody else may acquire the non-public key that belonged to that gadget, they may impersonate that gadget. They might then have the ability to hook up with the shopper’s cloud account, view buyer information, and alter firewall configurations. They could even have the ability to in some way acquire entry to our vendor AWS account by performing rogue actions with these credentials. It was crucial to maintain that key non-public and safe.
What if somebody on the safety vendor inserted code into the embedded programs on the gadget to entry the non-public key? What if malware acquired onto the firewall and executed instructions to acquire the important thing from disk or in reminiscence? What if an attacker obtained a developer’s credentials and wrote code to steal the non-public key from the gadget? What if a legitimate course of on the system was acquired infiltrated with rogue code that captured the important thing and unencrypted information from reminiscence? How would we even know?
For this reason I wished to make use of a particular {hardware} part built-in into the {hardware} known as a trusted platform module (TPM). That part was built-in into the gadget to guard the non-public key and the symmetric key exchanged with cloud programs. Microsoft Home windows makes use of a TPM to guard secrets and techniques when one exists on the {hardware} operating the Home windows working system.
Primarily the keys can be saved in {hardware} and processed by a separate bodily part. The opposite code on the gadget wouldn’t have any entry to the {hardware} part (reminiscence or storage) that dealt with the encryption keys and the encrypting and decrypting of the uneven key exchanged with AWS. The information would enter the part encrypted, be decrypted throughout the part and processed, after which re-encrypted earlier than it left the part. APIs existed to combine with this {hardware} part which allowed programmers to work together with it.
A TPM existed on these firewalls however on the time I labored on the firm they weren’t in use. There was a whole lot of dialogue about using the part however as much as that time the top of engineering that subsequently left the corporate had not prioritized its use. I not work for the corporate so I don’t know if the units use TPMs or not. As with something you will have to pay extra to get further safety for units which have and use that performance.
How is a TPM associated to an Enclave?
This idea of getting a separate {hardware} or generally software program part to segregate administration of encryption, decryption, and processing of extremely delicate information you don’t need in shared reminiscence on a system is the rationale enclaves exist. There are totally different names for for some of these elements.
Azure was really the primary cloud supplier to introduce this idea with their trusted execution atmosphere (TEE) which is a part of Azure confidential computing.
From the Microsoft web site:
Confidential computing is an trade time period outlined by the Confidential Computing Consortium (CCC) – a basis devoted to defining and accelerating the adoption of confidential computing. The CCC defines confidential computing as: The safety of knowledge in use by performing computations in a hardware-based Trusted Execution Surroundings (TEE).
GCP makes use of digital trusted platform modules of their shielded VMs (digital that means software program, not {hardware}):
AWS has introduce related performance with Nitro enclaves. Are enclaves {hardware} or software program? It appears like a mix of the 2 but it surely’s not precisely clear.
Nitro strikes some VM capabilities into {hardware}. If you wish to technical particulars explaining how AWS Nitro works that is one in every of my favourite movies on the subject:
AWS affords a Nitro TPM as properly. Extra on AWS Nitro Enclaves under.
The principle level of those elements is to make sure no different malware or code on the system can entry your encryption keys and really delicate information by maintaining it on fully separate {hardware} (sometimes). Software program implementations of some of these elements additionally exist however typically {hardware} is taken into account to be safer and more durable to tamper with.
That stated, increasingly more {hardware} vulnerabilities are coming into existence and turning into extra of a priority for organizations that course of extremely delicate information. So you may’t assume simply since you are utilizing {hardware} it’s safe. Firms like the most important cloud suppliers must be diligent in implementation and testing of {hardware} elements.
Through the use of an remoted part to course of delicate information, if correctly applied, even a rogue programmer or malware that will get entry to system reminiscence on an EC2 occasion shouldn’t be capable of get your encryption keys or information. It by no means exists anyplace that major EC2 system OS can entry it. A minimum of that’s the way it ought to work. I haven’t examined out AWS Nitro Enclaves but.
Ideally, in case you are creating a personal key, it’s generated on the gadget that it identifies (or the human that makes use of that gadget akin to a cellular phone) and by no means accessible to a human. An AWS Nitro Enclave does that.
Right here’s when an enclave, TEE, or TPM received’t enable you: I as soon as reviewed an identification system the place the seeding the system with consumer identities concerned e mail these preliminary values to the seller who then uploaded them to the system. For banking prospects. That’s not a safe method and I used to be instructed it might be mounted. Identities, Keys, and Certificates might be generated contained in the enclave fairly than have somebody create them externally after which add them in.
Provide chain assessments in relation to {hardware} and enclaves
The query in regards to the {hardware} for the gadget on the safety vendor that I had was how would the preliminary non-public key be generated that acquired saved within the TPM? If the gadget was manufactured in China would workers at that firm ever have entry to these non-public keys? May they acquire a public key and swap it out with their very own public key for a tool within the center assault of some sort? That is the extent of element you could go into in case you are fearful about provide chain points within the {hardware} you buy. Ask your vendor how they deal with these particulars.
Enclaves and community safety
I’ve seen a misunderstanding of the purpose of enclaves. Though they do block community entry to the info, you are able to do that at different layers in your structure for decrease price and complexity and earlier than an assault ever will get all the best way to your enclave. That may be a far safer alternative. You additionally most likely don’t wish to wait till you might be processing the info in an enclave to dam rogue community site visitors.
However in case one thing slips by way of, an enclave will assist by stopping information exfiltration if rogue code ought to in some way get into the enclave. That additionally shouldn’t occur if you happen to correctly develop, check, and signal your code. However as we all know, issues do occur.
An enclave can’t enable you view community site visitors to identify an assault that’s in any other case invisible as soon as attackers have management of your working system through a root package, {hardware}, or kernel degree exploit. I prefer to say that when your machine is compromised at that degree, it may possibly misinform you, however the community doesn’t lie. An attacker with low-level entry can change the output of your working system, instruments, and logs. They can not change community logs captured on separate units or in-line site visitors inspection units (except these are additionally compromised.)
An assault is barely helpful to an attacker if they will talk with the system remotely to hold out further instructions or exfiltrate information, and that exercise, although it may be hidden deep in community packet headers, should be seen in these packets. If it wasn’t, the info wouldn’t have the ability to get to it’s meant vacation spot or do what the attacker intends for it to do. Your community site visitors can reveal issues your system can’t in some case, probably except you dump and question the reminiscence. And the entire level of an enclave is which you can’t dump the reminiscence.
One of many main advantages of an enclave — defend information in reminiscence
The purpose of an remoted atmosphere isn’t merely to dam community entry (although it may possibly try this). It’s really to segregate out the info and keys from assaults that may entry delicate information in reminiscence (additionally known as in use). These sort of assaults are tough to defend towards as soon as rogue code has accessed a system.
You should still have the ability to defend information on disk with an encryption technique that protects an encryption key and by no means shops unencrypted information on disk. Nonetheless, defending information in reminiscence is considerably more difficult.
Encrypted information isn’t just ineffective to attackers — it’s ineffective to you and your software in and encrypted state. With the intention to develop into helpful, in some unspecified time in the future it’s important to decrypt it. You wish to defend it in its unencrypted state whereas being processed in reminiscence, however how will you try this?
It’s a must to be certain that no malware can ever infect that system or discover a option to crash the system and dump out reminiscence. It’s a must to be certain that there’s no software program operating on the system that may entry the reminiscence inappropriately utilizing instructions such because the one I demonstrated and described on this put up:
How are you going to try this? What if you happen to put your secrets and techniques and delicate unencrypted information in an enclave not accessible to instructions such because the one I simply talked about? There isn’t a command line on which to spit out information. Code within the enclave might be signed and no different rogue code or instructions can run aside from the software program that’s alleged to be operating in that atmosphere. That’s how we attempt to defend delicate information in reminiscence.
Enclaves within the context of the safety structure we’re creating
In the previous couple of posts we thought-about publicity of an SSH key created by a course of to assign to a consumer. We lined a variety of safety dangers and I defined that the most secure method to creating the important thing is likely to be to take action in an AWS Nitro Enclave.
What precisely is an AWS Nitro Enclave?
From the AWS documentation:
An enclave is a digital machine with its personal kernel, reminiscence, and CPUs. It’s created by partitioning reminiscence and vCPUs from a Nitro-based father or mother occasion. An enclave has no exterior community connectivity, and no persistent storage. The enclave’s remoted vCPUs and reminiscence can’t be accessed by the processes, purposes, kernel, or customers of the father or mother occasion.
So an enclave is a particular sort of digital machine that has an remoted processing atmosphere which nothing else can get into:
- No community entry so the info can’t be exfiltrated the software program operating within the enclave.
- No persistent storage so we don’t have to fret about our key residing on disk after creation.
- CPUs and reminiscence are segregated in such a manner nothing else can entry the info.
A digital machine appears like software program, however if you happen to try the AWS Nitro documentation it references a Nitro TPM:
Does an AWS Enclave use a TPM? It doesn’t actually say.
This video from an occasion in DC in 2022 earlier this 12 months talks about TPMs but it surely doesn’t say if AWS Enclaves use one or not. Nonetheless, if you happen to want a TPM for an software that protects your encryption keys in a hardware-based resolution, you now have entry to 1. As talked about above, AWS Nitro additionally pushes extra of the VM structure into {hardware} as properly.
Okay so an Enclave may be very remoted. But when we now have no community entry, then how can we get our new SSH key into SSM Parameter retailer or Secrets and techniques Supervisor? A Vsock proxy exists that permits the enclave to speak with the father or mother host. That “safe native channel” as AWS describes it, is clearly a crucial side of safety for a Nitro enclave.
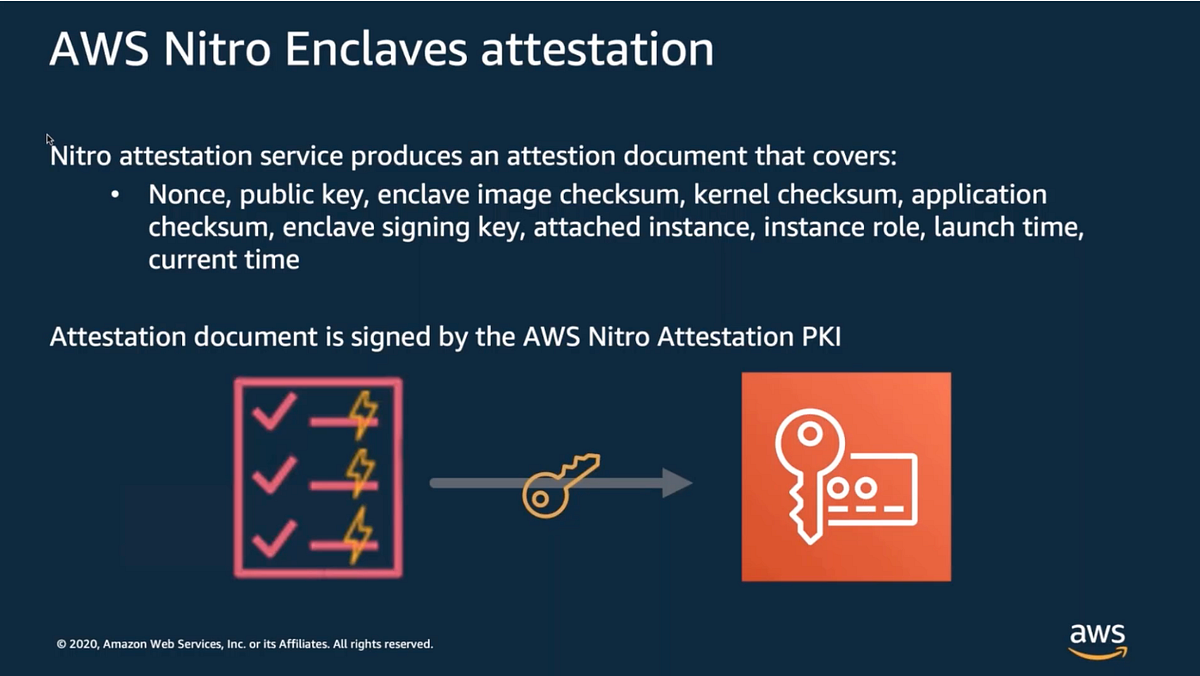
We are able to additionally leverage cryptographic attestations for Nitro enclaves when working with third-parties. The attestation doc might be verified earlier than initiating processes within the enclave. We aren’t working with a third-party however can evaluate that course of to see if it advantages us in any manner.
How an enclave helps with encrypted information and secrets and techniques
The aim of an enclave is to guard delicate information in reminiscence and in use on the host additionally preserve it out of persistent storage that will probably be accessible to malware or unauthorized customers. Enclaves and TPMs additionally defend non-public keys that establish a the enclave. The non-public secret’s generated within the enclave and by no means leaves the enclave. That non-public key can be utilized to decrypt information encrypted with the related public key.
Encryption keys can be in reminiscence through the encryption and decryption course of. As well as, in case you are processing delicate information, in some unspecified time in the future that information should be decrypted as a way to be processed. Malware may attempt to snatch that information out of reminiscence on the level of decryption in reminiscence as defined within the final put up.
Decrypting and processing the info in an enclave considerably reduces the probabilities that malware can get on the information or the encryption key. AWS Nitro Enclaves have a proxy to KMS. You may put encrypted information within the enclave, decrypt it, course of it, after which re-encrypt all of it within the enclave. The KMS encryption key and the info you could defend usually are not uncovered in such a manner that one other course of can seize them in reminiscence. The information is rarely saved to a persistent disk the best way we did with our SSH key once we created it.
A revised structure for creation of SSH keys for customers
Our downside with the SSH secret’s solved if we will create a KMS key that builders can use to decrypt information, however not our IAM directors. Then, we will grant every consumer entry to solely his or her secret in secrets and techniques supervisor to acquire an SSH key.
Will we hit a restrict on AWS Secrets and techniques Supervisor if we now have a whole lot of customers? The restrict per area for secrets and techniques is 500,000. For many organizations, no. Even massive organizations seemingly would not have all their customers in a single AWS account.
I already lined price comparability between Secrets and techniques Supervisor and AWS SSM Parameter Retailer in a previous put up. This looks as if our greatest choice.
Implementing our AWS Nitro Enclave Resolution
We are able to comply with this tutorial to create our enclave:
The very first thing to notice is that once we begin an ec2-instance on which we wish to run an enclave, we have to allow enclaves to start with:
aws ec2 run-instances --image-id ami_id --count 1 --instance-type supported_instance_type --key-name your_key_pair --enclave-options 'Enabled=true'
We are able to additionally allow the enclave utilizing CloudFormation:
Nonetheless, it seems like we now have to make use of the AWS Nitro Enclave CLI fairly than AWS CloudFormation to deploy the enclave.
The occasion must be a Nitro-based occasion. From the documentation on the time of this writing these are Nitro-based situations:
We can’t use one in every of these sorts, per the necessities:
besides t3, t3a, t4g, a1, c6g, c6gd, m6g, m6gd, r6g, r6gd, and u-*.
So it seems like these are our choices:
We’d like a minimum of 4 vCPUs. We are able to evaluate the checklist of EC2 situations to search out an sort that meets our wants:
Now I can cross-reference the checklist above with on-demand EC2 costs to get the bottom price choice. I can filter the checklist on Linux situations with 4 vCPUs. I kind by On-Demand hourly price descending, lowest to highest. I begin taking place the checklist until I discover an out there occasion sort.
Though the enclave is free, it’s important to use a dearer occasion sort to make use of one. The bottom price occasion sort that works on the time of this writing is a c5a.xlarge.
So if there are roughly 730 hours in a month it might price about $115 per thirty days to run this occasion. Nonetheless, I don’t have to run it always. I solely have to run it once I want the enclave to create my SSH keys or deal with different delicate operations.
Another issues:
OK so we create an occasion that permits us to create an enclave. The enclaved is carved out from the host individually from the principle EC2 VM and is actually one other VM that may solely talk with the picture from which it’s created. AWS helps just one enclave per picture however could help extra sooner or later.
How does an AWS KMS Enclave work with KMS?
Once you use an enclave with KMS you may create a KMS coverage that solely permits that particular enclave to make use of the encryption key to decrypt information. However how does KMS validate that it’s permitting the right enclave to make use of the encryption key?
Amazon KMS depends on the digital signature for the enclave’s attestation doc to show that the general public key within the request got here from a legitimate enclave.
Once you construct that picture you will get the next to validate the integrity of the picture:
- A checksum
- You may signal the picture as properly
KMS coverage says solely the picture with matching checksum or signature can use that key.
A checksum will be certain that solely a really particular picture can decrypt information, nevertheless each time you rebuild the picture it would have an up to date checksum. Meaning you could replace your KMS coverage each time the picture adjustments. If you’d like segregation of duties and to know every time a picture adjustments that’s an excellent factor.
Nonetheless, generally a company will use a signature as an alternative and say, “Solely pictures which might be signed with our signature can use this decryption key.” The danger on this case is that an attacker obtains the signing key after which can use that to create a picture that may decryption the info — and that sort of assault has occurred in a variety of excessive profile safety incidents with massive and well-known software program distributors.
Think about the chance when selecting one choice or the opposite in your key insurance policies.
Attestations
A Nitro Enclave also can present an attestation to show that it’s the enclave you propose to make use of. Earlier than sending delicate information to the enclave you need to validate the attestation doc offered by the enclave.
Here’s a useful video that gives a deep dive on Nitro and the way attestations work, although it appears to nonetheless be lacking a number of particulars.
A Nitro Enclave generates a neighborhood public-private key pair. The non-public key by no means leaves the enclave. When the enclave is terminated the keys are gone.
I defined the ideas of uneven encryption utilizing private and non-private keys in my e-book on the backside of the put up. The non-public/public key pair helps establish a person enclave. For the reason that enclave is the one place the place that personal key exists, solely that enclave will have the ability to decrypt paperwork encrypted with its public key.
An enclave requests an attestation doc from the AWS Nitro attestation service. It sends the general public key and a nonce with the request. The attestation service sends again an attestation doc with particulars in regards to the Nitro enclave. An enclave can present that attestation doc to somebody who requests it who ought to then confirm that the attestation doc matches the anticipated enclave earlier than offering any information to it. Solely the enclave will have the ability to decrypt and supply the attestation doc.
Right here’s the one query I’ve, nevertheless. What’s stopping that enclave from offering the attestation doc from one other enclave after requesting the attestation doc? I didn’t see that within the video. What if somebody requested an attestation doc from an enclave, then handed it to a different enclave, and in some way that enclave then handed out an incorrect attestation for a distinct enclave? The doc would nonetheless be signed by the Nitro attestation service.
The one that obtained the attestation doc may take further steps probably akin to verifying the checksum of the enclave an if they’ve the general public key for that enclave, decrypt the contents of the attestation with it. That doc may solely be encrypted with the right non-public key. How does the particular person decrypting the doc know that they’ve the right public key?.
This can be within the documentation someplace however I can solely spend a lot time in a day on every put up. This one is getting fairly lengthy and I’m not going to make use of an Enclave simply but for causes talked about on the backside of the put up.
A query that got here to thoughts was that I questioning if it might be higher to get the attestation from a separate service that tracks the attestation much like how TLS works? However maybe in some way the PKI structure solves this downside. I’ll must dig into it extra later.
For our functions, I don’t assume we’d like an attestation as a result of we is not going to be sharing information with third events or utilizing third-party enclaves. I imagine we’ll know which enclave we’re utilizing primarily based on different elements, however that might be confirmed upon implementation and additional testing.
Again to our tutorial — what else would we have to do to make use of an AWS Nitro Enclave?
- Construct our code right into a docker picture
- Use the Nitro CLI to transform the picture to a Nitro picture
- Run the enclave utilizing the picture file
- If operating in debug mode, you may view the read-only console output (which shouldn’t comprise any delicate information in manufacturing!)
Do we’d like an enclave?
An enclave would definitely be safer than the tactic I used within the final put up to create an SSH key, presuming I can get the encrypted information into SSM and/or Secrets and techniques supervisor from the enclave. I’d want to take a look at how that works since you’d get again encrypted information from the enclave, and then you definitely’d transport that to KMS or SSM. The explanation you seemingly can’t use the method we did in prior posts is that Secrets and techniques Supervisor and SSM would require community entry.
This provides complexity and price to our design and proper at this second. I wish to get by way of another parts of the structure first. I really feel that the steps we’re taking are moderately safe for a POC but when I used to be accessing extremely delicate information, I’d decide to implement the enclave earlier than continuing. We may additionally have the ability to leverage different controls to forestall entry to the host that generates the SSH key which is created and instantly shred. In reality, I’m going to alter the code to by no means retailer the important thing to disk, for one factor.
Alternatively, what if we wish to use AWS Batch to run our code? I don’t see any manner to make use of AWS Batch with a Nitro enclave and confirmed with somebody at AWS through Twitter that AWS Batch doesn’t leverage enclaves. How information is remoted and guarded relies on your chosen compute atmosphere — a subject we’ll discover extra later.
What if we run our automation scripts in a locked down batch course of that nobody can alter or entry and due to this fact they can not entry the important thing? Maybe that’s one other option to create credentials in a fashion that gives our desired non-repudiation.
Another choice can be to create a course of for customers to create their very own SSH key. We may create a coverage that permits a consumer to create an SSH key themselves however that solely matches their very own consumer identify. That manner solely the required consumer would ever have their very own SSH key. Then they may use an automatic course of to deploy an accredited EC2 occasion utilizing that key.
Though I would love to implement a Nitro Enclave as a result of it might be tremendous attention-grabbing, I’m going to complete another issues first. Earlier than we will even deploy the enclave we’d like an EC2 occasion and that’s why we’re creating this SSH key within the first place — so we will use it with an EC2 occasion and log into it. A lot of catch-22’s in safety. (22, SSH, pun not meant.)
Keep tuned for extra and probably I’ll revisit this subject sooner or later.
Teri Radichel
In the event you appreciated this story please clap and comply with:
Medium: Teri Radichel or E mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts