ACM.88 Deploy and occasion within the Developer VPC created Earlier and Check Distant Entry
It is a continuation of my sequence of posts on Automating Cybersecurity Metrics.
We already spent a couple of posts contemplating methods to authenticate and log into an EC2 occasion and for now, we are going to use an SSH key. You’ll be able to comply with together with how that key received created and saved in a Secrets and techniques Supervisor secret accessible to at least one consumer solely beginning right here (there are a number of posts on the subject):
CloudFormation for an EC2 occasion
I’m going to provide you a script that we are able to use that I offered to college students in school, with a couple of modifications.
Outputs referenced:
VPC, Subnet, and the SSH Safety Group ids from from the corresponding stack outputs. We created this networking within the posts that began right here:
Parameters:
Linux AMI ID: An Amazon Machine Picture (AMI) is a VM configuration that you need to use to create new VMs. It contains the Working System, set up software program, information, and settings.
Username: A username to tag the occasion and stack.
Key Identify: We’re going to create an SSH key for this consumer and the important thing identify may also be the username. The important thing identify shall be reference within the CloudFormation template.
Code: This may very well be something like a workforce, division, or mission. It’s added to the identify of the occasion. For instance, if each AMI associated to a specific mission began with the identical code or prefix it could be straightforward to question these situations by identify within the AWS console. I’m going to make use of the code ACM (Automating Cybersecurity Metrics or the identify of this weblog sequence).
Occasion Sort: The AWS occasion kind which is t4g.small by default however will be overridden.
Be aware that we aren’t including encryption to this AMI right here but — an AWS finest observe. Observe alongside to the subsequent put up for that.
About Occasion Varieties and Sizes
Be aware that on the time of this writing the default occasion dimension utilized by the template (which you’ll be able to override) is a T4g small occasion.
You’ll be able to evaluation the several types of digital machines accessible on AWS right here. As you might recall, for Linux you’ll be able to select from Arm or x86. Arm could also be cheaper however generally if you’re attempting to run software program that’s compiled for x86 you’re going to have challenges. You’ll must recompile the software program or change to x86.
You’ll be able to test data within the description that describes the processor to find out whether it is arm or x86, however AWS may make this a bit clearer by simply spelling our arm or x86 in a constant approach.
Permissions for the AppDeploy Function
For this framework I’m going to have the AppDeploy position deploy EC2 situations. You’ll be able to identify these roles no matter you need should you don’t like my names, however I’m utilizing AppDeploy to deploy compute sources within the account. By trial and error I discovered I would like these permissions to run our template. Be aware that we aren’t going to permit this consumer to assign a task to an EC2 occasion simply but. We don’t even have any roles that can be utilized with EC2 situations at the moment.
VM Features
I created two features in my VM features script.
get_lastest_ami: This perform will get the most recent AMI. With a view to get the most recent AMI we’d like the structure for the kind of AMI we need to retrieve. In my case I default to arm64 if not structure is about. This shall be for Linux kind situations and can pull the most recent arm64 AMI (till AWS adjustments their naming conventions).
deploy_vm: On this perform, we get the mandatory parameters and name the deploy_stack perform.
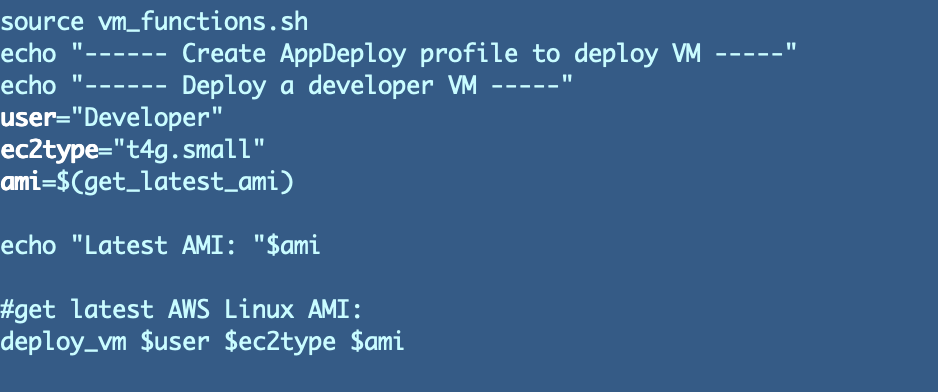
Deploy Script
The deploy script is fairly easy. Get the most recent AMI utilizing our get_latest_ami perform. Then name deploy_vm with the suitable parameters.
CloudFormation Template
We’re beginning to get a whole lot of sources in our account. That is the place our naming conference is useful. We are able to search on Community-VPC to seek out the VPCs we created. We need to use the Developer VPC. Click on on that stack.
We’re going to get the VPC ID from the outputs as we have now been doing all together with our frequent perform on this sequence.
Utilizing these outputs our template to deploy an EC2 occasion finally ends up wanting like this:
For now I’m simply naming the occasion with the identify of the consumer “Developer” and the AMI ID, the occasion kind, and AMI ID.
For the outputs I needed to miss InstanceType because it has invalid characters.
If we go take a look at the EC2 dashboard you’ll be able to see I had a couple of failed try to deploy my EC2 occasion whereas attempting to find out the mandatory permissions, however as soon as I figured these out I received my occasion working with the right identify.
Subsequent Steps…
In your individual group you’ll possible create your individual AMI that’s aligned along with your safety requirements. Out of the gate, AWS EC2 situations are usually not CIS Benchmarks compliant. If you wish to use an EC2 occasion that’s yow will discover some within the AWS Market. Ensure you get them from the right supply (The Heart for Web Safety) as a result of again within the day I do not forget that dangerous actors would attempt to create photos that regarded like they had been coming from Amazon however they weren’t.
You’ll be able to even modify the question above to get the most recent CIS benchmarks AMI however I’m not going to do this right here — I’ll go away that as an train for the reader. 🙂
As well as we need to encrypt our AMI with our personal developer KMS key. That approach solely our builders which have permission to make use of that key can entry our EC2 occasion.
Observe for updates.
Teri Radichel
Should you appreciated this story please clap and comply with:
Medium: Teri Radichel or E-mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts