Builders are more and more below assault by means of the instruments that they use to collaborate and to provide code — corresponding to Docker, Kubernetes, and Slack — as cybercriminals and nation-state actors purpose to entry the precious software program that builders work on daily.
As an example, an attacker claimed on Sept. 18 to have used stolen Slack credentials to entry and replica greater than 90 movies representing the early growth of Grand Theft Auto 6, a well-liked sport from Take-Two Interactive’s Rockstar Video games. And per week earlier, safety agency Pattern Micro found that attackers had been systematically looking for and making an attempt to compromise misconfigured Docker containers.
Neither assault concerned vulnerabilities within the software program packages, however safety missteps or misconfiguration should not unusual on the a part of builders, who usually fail to take the care essential to safe their assault floor space, says Mark Loveless, a workers safety engineer at GitLab, a DevOps platform supplier.
“Loads of builders do not consider themselves as targets as a result of they’re pondering that the completed code, the top consequence, is what attackers are going after,” he says. “Builders usually take safety dangers — corresponding to organising take a look at environments at house or taking down all the safety controls — to allow them to check out new issues, with the intent of including safety later.”
He provides, “Sadly, these habits change into replicated and change into tradition.”
Assaults towards the software program provide chain — and the builders who produce and deploy software program — have grown shortly up to now two years. In 2021, for instance, assaults that aimed to compromise builders’ software program — and the open supply parts broadly utilized by builders — grew by 650%, in accordance with the “2021 State of the “Software program Provide Chain” report, printed by software program safety agency Sonatype.
Developer Pipelines & Collaboration within the Sights
General, safety specialists preserve that the quick tempo of steady integration and steady deployment environments (CI/CD) that type the foundations of DevOps-style approaches pose vital dangers, as a result of they’re usually ignored in relation to implementing hardened safety.
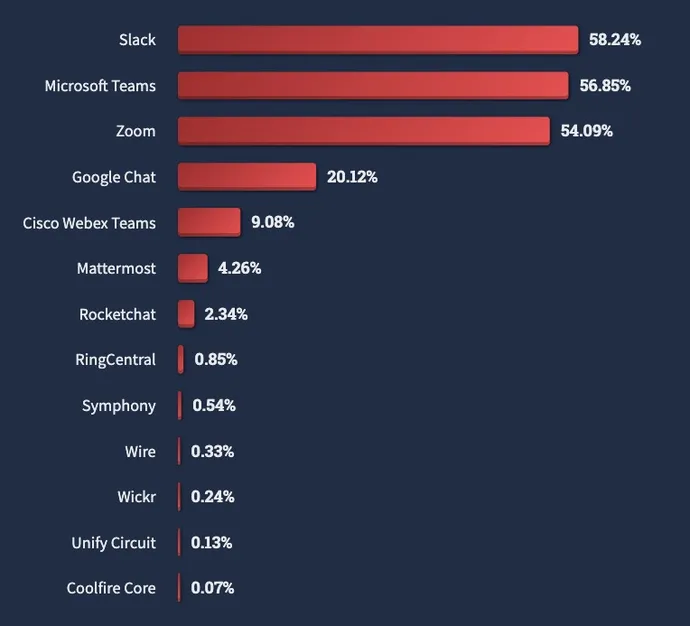
This impacts quite a lot of instruments utilized by builders of their efforts to create extra environment friendly pipelines. Slack, for instance, is the preferred synchronous collaboration instruments in use amongst skilled builders, with Microsoft Groups and Zoom coming in a detailed second and third, in accordance with the 2022 StackOverflow Developer Survey. As well as, greater than two-thirds of builders use Docker and one other quarter use Kubernetes throughout growth, the survey discovered.
Breaches of instruments like Slack may be “nasty,” as a result of such instruments usually carry out important capabilities and normally solely have perimeter defenses, Matthew Hodgson, CEO and cofounder of messaging-platform Component, mentioned in an announcement despatched to Darkish Studying.
“Slack just isn’t end-to-end encrypted, so it’s just like the attacker gaining access to the corporate’s complete physique of information,” he mentioned. “An actual fox-in-the-henhouse state of affairs.”
Past Misconfigs: Different Safety Woes for Builders
Cyberattackers, it ought to be famous, do not simply probe for misconfigurations or lax safety in relation to going after builders. In 2021, for instance, a menace group’s entry to Slack by means of the gray-market buy of a login token led to a breach of sport big Digital Arts, permitting the cybercriminals to repeat almost 800GB of supply code and information from the agency. And a 2020 investigation into Docker photographs discovered that greater than half of the newest builds have important vulnerabilities that put any software or service primarily based on the containers in danger.
Phishing and social engineering are additionally plagues within the sector. Simply this week, builders utilizing two DevOps companies — CircleCI and GitHub — had been focused with phishing assaults.
And, there is no such thing as a proof that the attackers concentrating on Rockstar Video games exploited a vulnerability in Slack — solely the claims of the purported attacker. As a substitute, social engineering was doubtless method to bypass safety measures, a Slack spokesperson mentioned in an announcement.
“Enterprise-grade safety throughout id and gadget administration, information safety, and data governance is constructed into each facet of how customers collaborate and get work accomplished in Slack,” the spokesperson mentioned, including: “These [social engineering] techniques have gotten more and more widespread and complex, and Slack recommends all prospects follow sturdy safety measures to protect their networks towards social engineering assaults, together with safety consciousness coaching.”
Sluggish Safety Enhancements, Extra Work to Do
Builders have solely slowly accepted safety as software safety professionals name for higher controls, nevertheless. Many builders proceed to leak “secrets and techniques” — together with passwords and API keys — in code pushed to repositories. Thus, growth groups ought to concentrate on not simply defending their code and stopping the importing of untrusted parts but in addition guaranteeing that the important capabilities of their pipelines should not compromised, GitLab’s Loveless says.
“The entire zero-trust half, which is often about figuring out folks and issues like that, there additionally ought to be the identical ideas that ought to apply to your code,” he says. “So do not belief the code; it must be checked. Having folks or processes in place that assumes the worst — I am not going to belief it routinely — notably when the code is doing one thing important, like construct a undertaking.”
As well as, many builders nonetheless don’t use primary measures to strengthen authentication, corresponding to utilizing multifactor authentication (MFA). There are modifications afoot, nevertheless. More and more, the varied open supply software program bundle ecosystems have all began requiring that main initiatives undertake multifactor authentication.
By way of instruments to concentrate on, Slack has gained consideration due to the newest main breaches, however builders ought to try for a baseline stage of safety management throughout all of their instruments, Loveless says.
“There are ebbs and flows, however it’s no matter works for the attackers,” he says. “Talking from my expertise of sporting every kind of hats of various colours, as an attacker, you search for the best means in, so if one other means turns into simpler, then you definately say, ‘I’ll attempt that first.'”
GitLab has seen this follow-the-leader conduct in its personal bug bounty packages, Loveless notes.
“We see when folks ship in bugs, all of the sudden one thing — a brand new method — will change into fashionable, and a complete slew of submissions ensuing from that method will are available,” he says. “They undoubtedly are available waves.”


