An app which presupposed to launch distributed denial-of-service (DDoS) assaults in opposition to the web infrastructure of Russia, was in actuality secretly putting in malware on to the gadgets of pro-Ukrainian activists.
As researchers at Google’s Risk Evaluation Group (TAG) describe, the Moscow-backed Turla hacking group created an internet site purporting to belong to Ukraine’s Azov regiment.
On the bogus web site, customers had been inspired to obtain a device that may allegedly swamp Russian web sites with undesirable visitors.
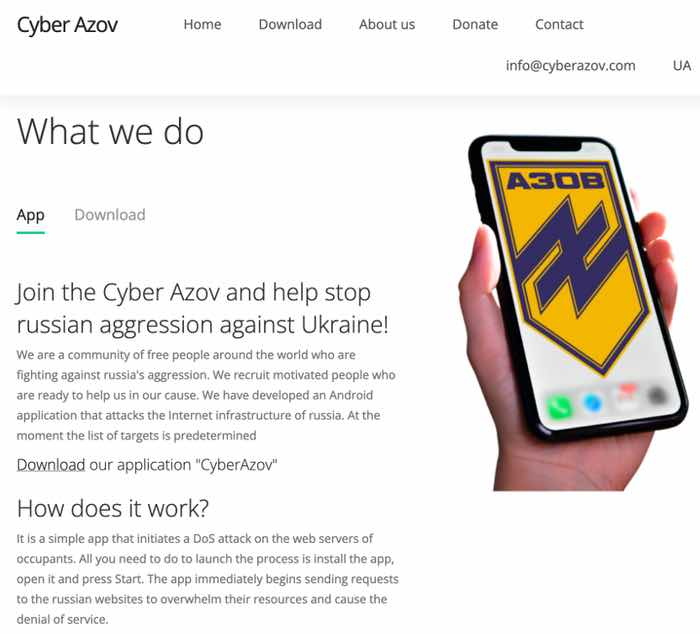
The web site claimed to clarify how the app, which was not obtainable on the official Google Play retailer, would assist in the struggle in opposition to Russia’s invading forces:
It’s a easy app that initiates a DoS assault on the internet servers of occupants. All it is advisable do to launch the method is set up the app, open it and press Begin. The app instantly begins sending requests to the russian web sites to overwhelm their sources and trigger the denial of service.
To anybody who did not look carefully, the app’s web site would possibly seem not dissimilar to that belonging to the StopWar Android app, that bombards Russian websites with visitors.
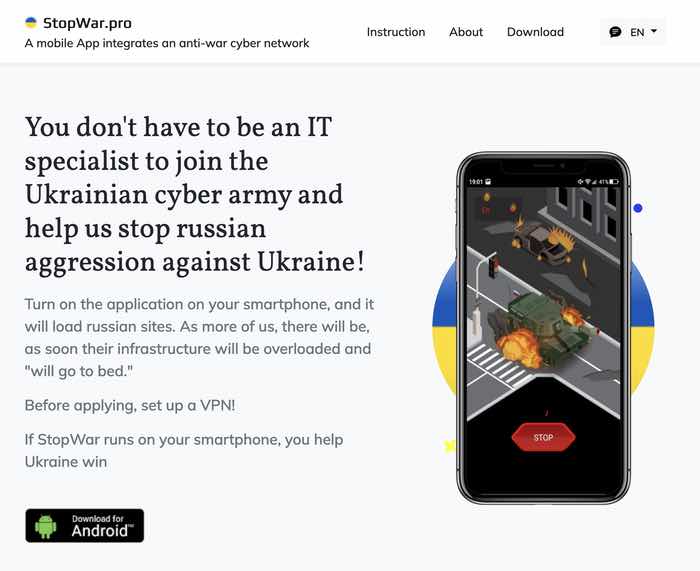
Would you be capable of simply inform one app from the opposite based mostly on these web sites?
As a result of there is a elementary distinction between StopWar and the so-called “Cyber Azov” app.
In response to Google’s researchers, the Cyber Azov app solely visits the Russian web sites it claims to be attacking as soon as, in an obvious try to collect details about these pro-Ukraine activists who can be tempted to make use of such a device.
The excellent news is that the researchers don’t consider that many individuals had been duped into downloading the bogus Cyber Azov device, although hyperlinks to it had been disseminated by way of messaging providers in an try and seed the app amongst activists preventing the Russian invasion.
The warfare in Ukraine has seen either side of the battle mobilising hackers.
The FSB-backed Turla group (also called Waterbug or Venomous Bear), as an example, has been concerned in a variety of actions together with focused APT assaults in opposition to authorities organisations, spear phishing, and cyberespionage.
Turla’s bogus DDoS device could not have amounted to a lot of a severe menace, however it’s clear that different assaults launched by the group up to now have been profitable… and little doubt they are going to be once more.


