Introduction
Counterfeiting of merchandise is a serious international downside that goes past simply the income loss for the producers – it can lead to the lack of the model popularity as a consequence of poor high quality of counterfeits. Historically, holograms have been used for guaranteeing the authenticity of the merchandise. Nevertheless, they will present solely restricted data. A QR code is a extra versatile device, however it could possibly simply be tampered, eliminated, or changed. A way more versatile mechanism for product verification is NFC tag, which is digital element that may retailer a small quantity of knowledge that may be learn wirelessly over brief distance. These tags comprise a tiny NFC chip and a versatile antenna. NFC tags might be straight built-in into the product for instance inside the layers of cloth or contained in the packaging of the product, thus making it tough to tamper. Product data might be securely programmed wirelessly, after the ultimate product is prepared. To determine product authenticity in a retail retailer, the product data might be learn utilizing a devoted verification terminal. This text describes intimately how the product verification utilizing the NFC expertise works in observe. It’s an try and curtail practically half a trillion {dollars} a yr value of worldwide commerce in pretend items [1].
NFC Expertise
NFC is a wi-fi communication expertise working at 13.56 MHz that permits safe communication between two NFC-enabled gadgets over a short-range. NFC is a robust expertise which allows safe advert hoc communication between digital gadgets with out requiring ceremony like passwords and pins. NFC expertise is extensively used for including interactivity to inanimate objects thus making them sensible. Ticketing, funds, and entry management and so forth. are among the major areas the place the NFC expertise is extensively deployed.
An NFC-enabled system has two components – NFC Tag and NFC Reader. NFC Reader is the energetic element that initiates learn & write operation on the NFC tag whereas additionally offering energy to the NFC tag by way of electromagnetic induction. An NFC tag is usually passively powered machine i.e., it receives its energy from the NFC reader. The NFC Tag has an antenna coil which is used to speak with the NFC reader and harvesting vitality from the electromagnetic discipline of the NFC reader. The reader sends the information to the tag by modulating the RF discipline sign and the tag sends the information to the reader by modulating the load. When an NFC tag comes within the neighborhood of the NFC reader, the NFC reader reads the tag attributes adopted by an trade of knowledge. Every NFC tag is addressed uniquely utilizing a novel identifier referred to as UID.
NFC employs totally different “applied sciences” and makes use of the identical RF service, however every expertise makes use of its personal modulation scheme, bit-level coding, and body format. There are primarily 4 varieties of NFC applied sciences (NFC-A, NFC-B, NFC-F, NFC-V). An NFC Tag could assist a number of of the above-mentioned applied sciences.
The NFC tags are additional categorized into tag varieties relying on numerous reminiscence, throughput, collision mechanism and ISO requirements assist.
Product verification at a retail retailer
On this part, we talk about the working of the verification system intimately. Through the manufacturing of the product NFC tag is embedded within the product in order that it’s hid and never detachable by the person. If it isn’t potential to embed the tag into the product itself, the NFC tag may also be embedded contained in the product packaging. Product particulars like serial quantity/mannequin and so forth. are programmed into the tag utilizing an NFC transceiver together with a product verification URL which factors to a safe verification server.
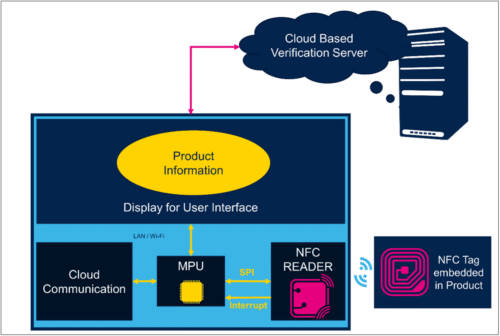
The verification system makes use of a devoted verification terminal put in within the retail retailer. When the product to be verified is taken close to the NFC reader of the verification terminal, it reads the distinctive id of the NFC tag together with the saved product data and the verification URL. The terminal which is related to the web then sends a verification request to the cloud-based verification server to fetch the verification standing and detailed product data. The verification outcomes together with the product particulars like date of manufacture, dimensions, coloration, guarantee particulars, and so forth. are proven on the show unit. The image of the product can be proven on the show, which permits the person to bodily confirm the product description. If the web connectivity shouldn’t be obtainable, the product information saved on the NFC tag is displayed on a NFC enabled Smartphone. This mechanism allows the customer to readily verify the genuineness of the product within the retail retailer and resolve the issue of faux product gross sales out there. A block diagram illustration of the whole system is proven in Determine 1.
The answer may also be seen as a buyer engagement platform. Prospects change into extra assured about product veracity if the terminal is supplied as a self-service kiosk the place clients can run the verification themselves. The system may also be used to show promotional details about the scanned product and likewise in regards to the associated merchandise to assist cross promoting of the gadgets. At any time when a product is verified on the terminal, the transaction is recorded by the verification server. This data can be utilized to run additional analytics and uncover buyer preferences about numerous merchandise.
Software program Structure of NFC-based Verification Terminal
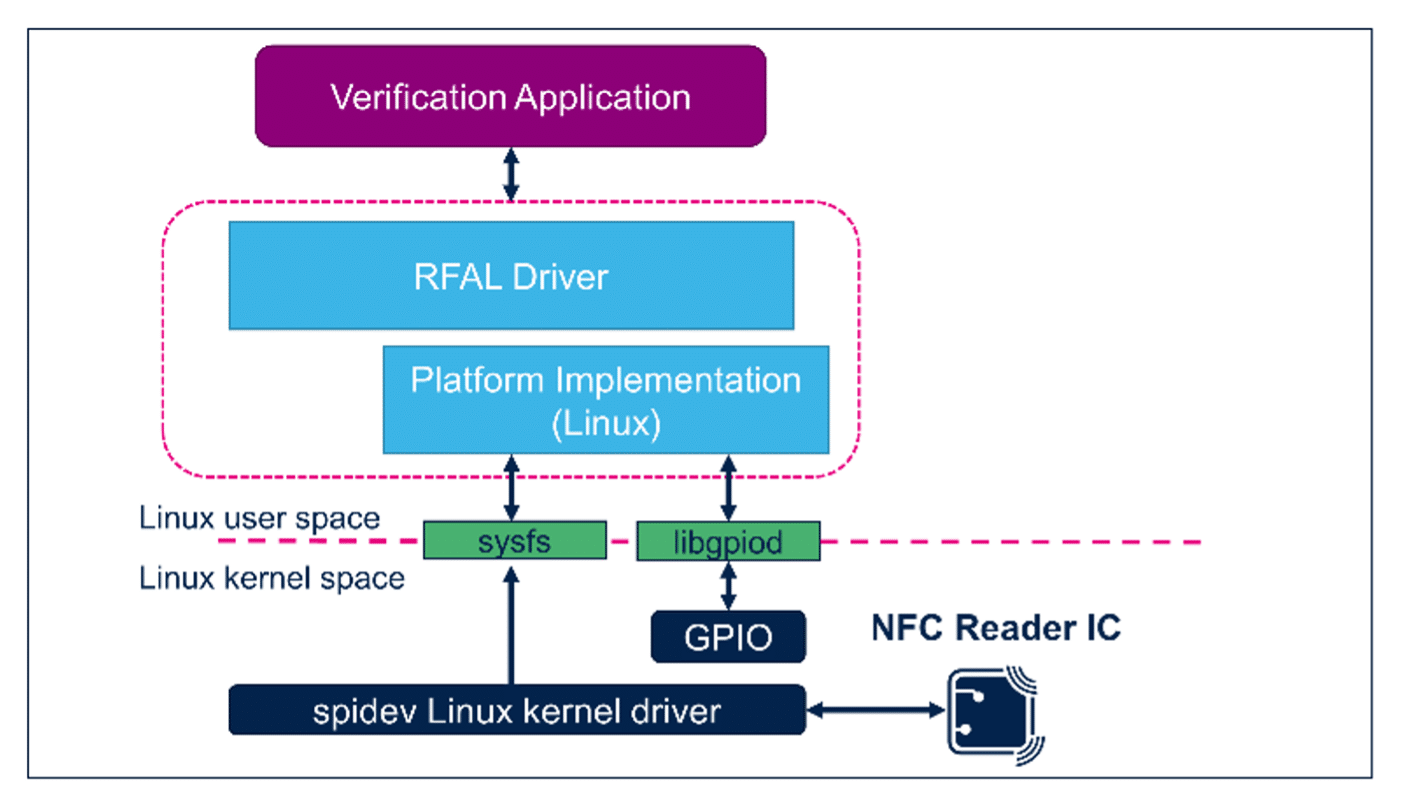
This part describes the software program structure of the Linux-based verification terminal. Linux is the popular host OS for this software as a result of it’s confirmed, free and permits builders to leverage present high-quality libraries.
The core performance is supplied by a “Verification Utility” which communicates with the RFAL (Radio Frequency Abstraction Layer) driver to entry information on the NFC tag. ‘RFAL Driver protocols’ is the set of features that assist the appliance to translate the communication with the NFC reader over SPI. ‘spidev’[4] is the driving force module within the Linux kernel area which is accountable for dealing with all communication to and from the appliance over SPI bus. Determine 2 beneath, exhibits the general software program structure of the verification terminal.
When an NFC tag is introduced close to the reader antenna, the NFC chip detects the presence of a brand new tag. An interrupt is triggered which is detected by the appliance software program by way of libgpiod[5] mechanism of the Linux OS. The appliance software program on the reception of interrupt begins speaking with the NFC chip to learn the Distinctive Identifier (UID) and different information saved within the Tag. The answer makes use of fantastic Linux networking libraries to speak with the cloud and fetch the verification standing in addition to the product particulars. The outcomes are proven on the show. Native UI Framework like GTK or Qt can be utilized to show the data in a wealthy GUI surroundings.
{Hardware}
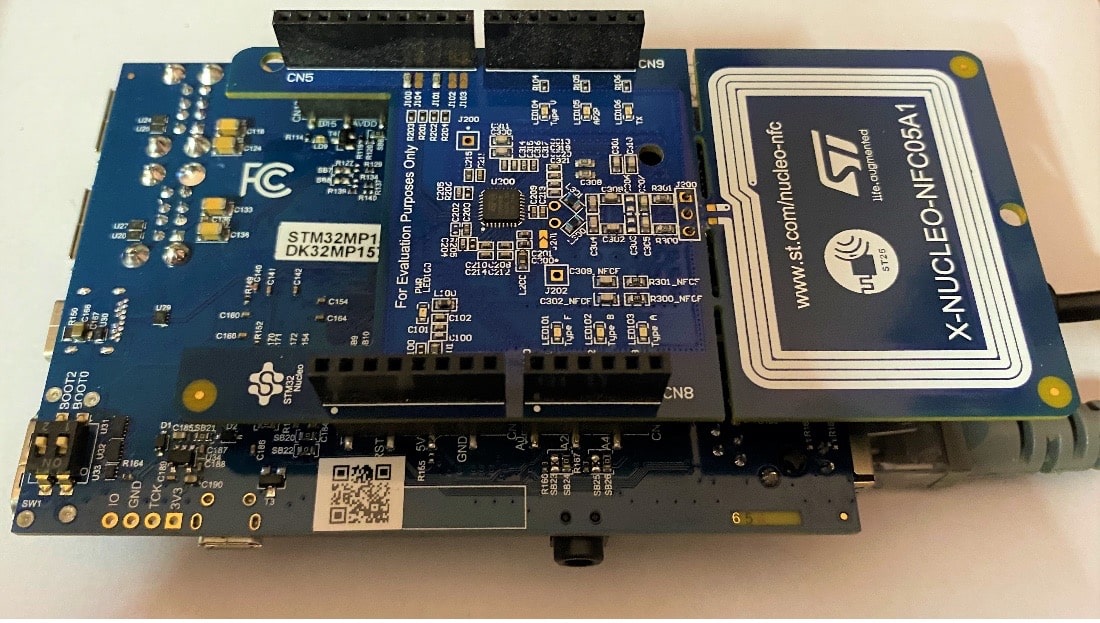
The idea has been confirmed utilizing a system resolution constructed across the STMicroelectronics STM32MP1 discovery equipment (STM32MP157F-DK2) which hosts a STM32MP1 collection industrial microprocessor to permit customers to simply develop functions utilizing OpenSTLinux distribution software program. The NFC performance is supplied by the NFC reader (ST25R3911B) enlargement board (X-NUCLEO-NFC05A1) which docks on the connector obtainable on the invention equipment (Determine 3) and numerous NFC tags primarily based on the ST25DV04K NFC Kind V tag IC. The implementation might be enhanced additional by utilizing NFC Reader (ST25R3916) primarily based enlargement board (X-NUCLEO-NFC06A1). ST25R3916 helps card emulation mode and is totally compliant with EMVCo 3.0. NFC front-end IC is interfaced with a microprocessor by way of appropriate communication protocol for instance SPI (Serial Peripheral Interface) or I2C (Inter-integrated circuits).

Conclusion
This text discusses the usage of NFC expertise for establishing the authenticity of shopper items utilizing NFC tag. Contemplating many reviews of spurious medicines being offered through the COVID-19 pandemic, such options may even assist in saving lives. For top worth merchandise like gem stones or lifesaving medicine, the safety of the answer might be additional enhanced by utilizing digital certificates saved in NFC tags. The answer may also be tailored to provide chains by using blockchain to confirm authenticity of the elements at every stage within the provide chain thus guaranteeing that the ultimate product is manufactured utilizing real components solely. The answer may also be prolonged to incorporate e-commerce eventualities, the place the buyer can simply confirm the product at residence utilizing a cell software and an NFC-enabled Smartphone.