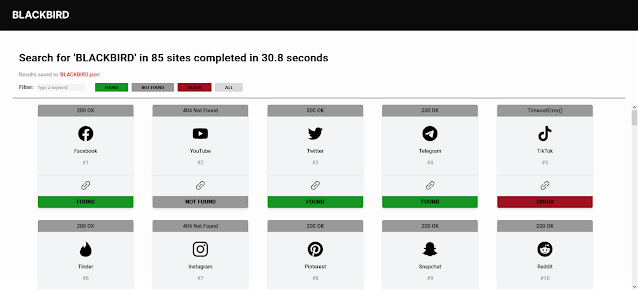
An OSINT instrument to look quick for accounts by username throughout 101 websites.
The Lockheed SR-71 “Blackbird” is a long-range, high-altitude, Mach 3+ strategic reconnaissance plane developed and manufactured by the American aerospace firm Lockheed Company.
Disclaimer
This or earlier program is for Academic objective ONLY. Don't use it with out permission.
The same old disclaimer applies, particularly thetruth that me (P1ngul1n0) is just not accountable for any
damages brought on by direct or oblique use of the data or performance offered by these
packages. The creator or any Web supplier bears NO duty for content material or misuse
of those packages or any derivatives thereof. By utilizing these packages you settle for the very fact
that any injury (dataloss, system crash, system compromise, and so on.) brought on by means of these
packages is just not P1ngul1n0's duty.
Setup
Clone the repository
git clone https://github.com/p1ngul1n0/blackbird
cd blackbirdSet up necessities
pip set up -r necessities.txtUtilization
Search by username
python blackbird.py -u usernameRun WebServer
python blackbird.py --webEntry http://127.0.0.1:5000 on the browser
Learn outcomes file
python blackbird.py -f username.jsonRecord supportted websites
python blackbird.py --list-sitesSupported Social Networks
- Fb
- YouTube
- Twitter
- Telegram
- TikTok
- Tinder
- Instagram
- Pinterest
- Snapchat
- Reddit
- Soundcloud
- Github
- Steam
- Linktree
- Xbox Gamertag
- Twitter Archived
- Xvideos
- PornHub
- Xhamster
- Periscope
- Ask FM
- Vimeo
- Twitch
- Pastebin
- WordPress Profile
- WordPress Website
- AllMyLinks
- Buzzfeed
- JsFiddle
- Sourceforge
- Kickstarter
- Smule
- Blogspot
- Tradingview
- Web Archive
- Alura
- Behance
- MySpace
- Disqus
- Slideshare
- Rumble
- Ebay
- RedBubble
- Kik
- Roblox
- Armor Video games
- Fortnite Tracker
- Duolingo
- Chess
- Shopify
- Untappd
- Final FM
- Money APP
- Imgur
- Trello
- MCUUID Minecraft
- Patreon
- DockerHub
- Kongregate
- Vine
- Gamespot
- Shutterstock
- Chaturbate
- ProtonMail
- TripAdvisor
- RapidAPI
- HackTheBox
- Wikipedia
- Buymeacoffe
- Arduino
- League of Legends Tracker
- Lego Concepts
- Fiverr
- Redtube
- Dribble
- Packet Storm Safety
- Ello
- Medium
- Hackaday
- Keybase
- HackerOne
- BugCrowd
- DevPost
- OneCompiler
- TryHackMe
- Lyrics Coaching
- Expo
- RAWG
- Coroflot
- Cloudflare
- Wattpad
- Mixlr
- ImageShack
- Freelancer
- Dev To
- BitBucket
- Ko Fi
- Flickr
- HackerEarth
- Spotify
- Snapchat Tales
Supersonic velocity
Blackbird sends async HTTP requests, permitting much more velocity when discovering person accounts.
JSON Template
Blackbird makes use of JSON as a template to retailer and skim knowledge.
The knowledge.json file retailer all websites that blackbird confirm.
Params
- app – Website identify
- url
- legitimate – Python expression that returns True when person exists
- id – Distinctive numeric ID
- technique – HTTP technique
- json – JSON physique POST (must be escaped, use this
https://codebeautify.org/json-escape-unescape) - {username} – Username place (URL or Physique)
- response.standing – HTTP response standing
- responseContent – Uncooked response physique
- soup – Beautifulsoup parsed response physique
- jsonData – JSON response physique
Examples
GET
{
"app": "ExampleAPP1",
"url": "https://www.instance.com/{username}",
"legitimate": "response.standing == 200",
"id": 1,
"technique": "GET"
}POST JSON
{
"app": "ExampleAPP2",
"url": "https://www.instance.com/person",
"legitimate": "jsonData['message']['found'] == True",
"json": "{{"kind": "username","enter": "{username}"}}",
"id": 2,
"technique": "POST"
}When you’ve got any suggestion of a web site to be included within the search, make a pull request following the template.
Contact
Be happy to contact me on Twitter