Anjuna® and HashiCorp allow confidential computing on Purple Hat® OpenShift® utilizing Intel® Software program Guard Extensions (Intel® SGX). On this structure, containerized purposes isolate secrets and techniques equivalent to encryption keys and passwords in {hardware} protected reminiscence enclaves.
Defending information whereas in use—versus at relaxation or in transit—is difficult partially as a result of that information should typically be in an unencrypted state for software program to function on it. Isolating free-text information from different purposes and providers in the identical shared reminiscence house utilizing software program measures is restricted by definition, as a result of with adequate privileges, that isolation can at all times be overcome. Furthermore, such measures are poorly suited to safety in opposition to system software program compromise or insider threats.
Assaults on the software program provide chain are a crucial rising cybersecurity problem that primarily focuses on information in use by exploiting vulnerabilities in instruments and code. Analysis means that the variety of software program provide chain assaults tripled in 2021 in comparison with the 12 months earlier than,(1) and that organizations of fifty,000 seats or extra are focused almost each week on common.
Resisting these assaults is made more difficult as a result of doing so successfully requires coordinated joint effort between safety, growth, and operations (DevSecOps) organizations inside IT. The rise of DevSecOps in enterprise IT supplies that coordination, bringing collectively all three organizations right into a unified staff that helps guard in opposition to provide chain compromise. Confidential computing helps that effort with an vital mechanism to harden the DevSecOps pipeline.
Organizations that deal with delicate information equivalent to personally identifiable info (PII), monetary information, or well being info have to mitigate threats that concentrate on the confidentiality and integrity of both the appliance or the info in system reminiscence. – Confidential Computing Consortium (3)
Confidential computing isolates trusted code and trusted information from unauthorized software program and customers primarily based on a low-level {hardware} root of belief that extends upward by way of the answer stack. That root of belief permits a trusted execution setting (TEE), with a low-level {hardware} basis that eliminates software program dependencies and related vulnerabilities. The TEE protects the trusted information and code, in addition to the integrity of operations carried out on it. Not like softwarebased measures, the TEE is protected in opposition to unauthorized entry by customers or software program, no matter privilege stage.
This paper describes an ecosystem-driven answer for confidential computing primarily based on a {hardware} root of belief, as illustrated in Determine 1. Intel SGX implements confidential computing with hardware-enforced partitioning of system reminiscence to create enclaves of restricted trusted reminiscence house. Trusted code operates on unencrypted trusted information in enclaves, remoted from unauthorized entities. This silicon performance is applied in Intel® Xeon® Scalable processors utilizing a devoted instruction set, and modifications are usually required to utility binaries, designating trusted parts of code to function in enclaves.
Anjuna Confidential Computing software program abstracts away that complexity by enabling any present software program, with out modification, to make the most of Intel SGX enclaves. The work described on this paper implements secret and encryption administration primarily based on HashiCorp Vault, operating on Intel SGX-capable {hardware} utilizing the Anjuna platform. The answer runs in containers, utilizing a modified Dockerfile offered by HashiCorp to offer cloud-native operation on Purple Hat OpenShift. Following a use case description that describes their mixed implementation on the command stage and the way the answer structure can be utilized to harden the DevSecOps pipeline, every of those {hardware} and software program elements is described individually.
 Intel
IntelDetermine 1. {Hardware}-based root of belief for confidential computing.
1 Hardening the DevSecOps Pipeline
Operating HashiCorp Vault within Intel SGX enclaves supplies novel capabilities to harden the DevSecOps pipeline. Excessive-profile software program provide chain assaults such because the SolarWinds breach in 2021 reveal the frequent vulnerabilities presently uncovered in lots of DevSecOps pipelines and the doubtless damaging impacts they will have. The compromise within the SolarWinds hack injected a malicious Dynamic Hyperlink Library right into a late stage of the pipeline, which was then signed utilizing the legit codesigning certificates earlier than being pushed out in a consumer replace.
Guide safety and audit processes for DevSecOps pipelines are frequent, making a main threat vector for software program provide chain compromise. The sluggish tempo of those labor-intensive processes could make it tough to determine pipeline assaults in a well timed method. Utilizing the Anjuna and HashiCorp answer to run purposes inside Intel SGX enclaves supplies hardware-based proof of software program elements’ integrity, defending the software program provide chain extra broadly. This use case extends safety for information at relaxation all through the DevSecOps pipeline, as proven in Determine 2:
- Safe Improvement Setting. The native built-in growth setting (IDE) is linked to an enclave that helps defend the supply administration answer (e.g., Git repo) on a central server or cloud system. A safe ledger supplies code integrity by the use of attested code and binary checkins. This structure additionally supplies integrity safety by testifying code and binary check-out.
- Safe Construct Setting. The compiler (e.g., GCC) runs in a container inside an enclave. This topology supplies integrity safety by testifying each code enter and binary enter. A safe ledger provides code integrity by testifying to the binary output.
- Safe Check Setting. QA and regression testing are protected inside an enclave, with integrity safety offered by testifying the binary and a safe ledger including code integrity to the QA outcomes.
- Safe Launch Setting. The construct course of is protected inside an enclave, with integrity safety offered by attestation of the construct inputs and launch variations. A safe ledger provides code integrity.
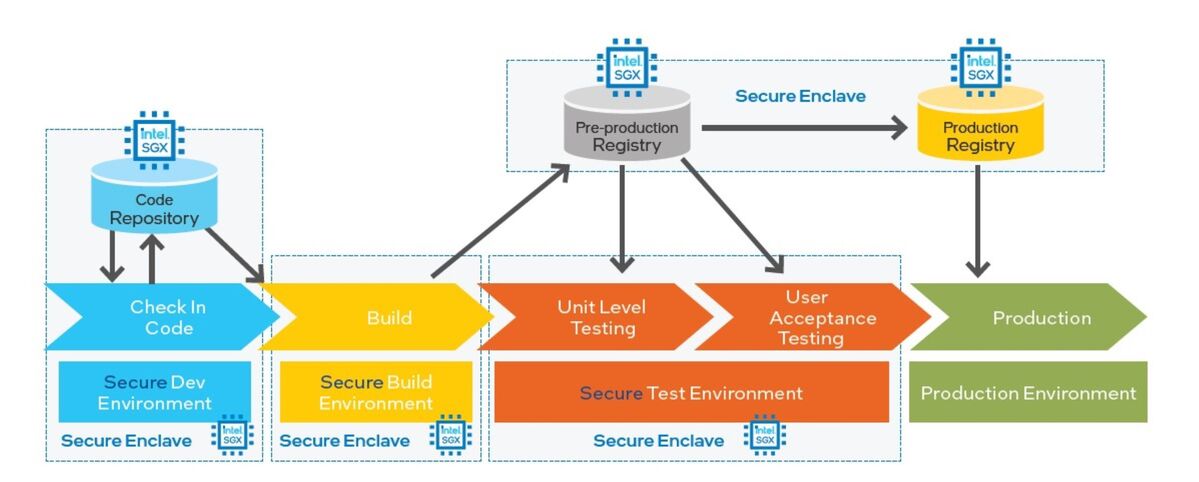 Intel
IntelDetermine 2. Runtime protections primarily based on Intel® SGX enclaves for hardened DevSecOps.
2 {Hardware} Enablement for Confidential Computing: Intel SGX
Software program-based protections for information are inherently susceptible to being circumvented by different lower-level or more-privileged software program. As a easy illustration, a typical utility is unable to defend its information from processes approved by the OS, hypervisor, pre-boot partition, or a person with root entry. From a cyber safety perspective, assaults on the OS can compromise all the things operating on it, successfully extending the assault floor for a person piece of delicate information to your entire OS. That state is proven within the “With out Intel SGX” pane of Determine 3.
 Intel
IntelDetermine 3. Decreased belief boundary and assault floor with Intel® SGX.
As proven within the “With Intel SGX” pane of Determine 3, Intel SGX reminiscence enclaves isolate information and executing code, utilizing a non-public reminiscence house that’s inaccessible from exterior the enclave and the one place the place the info is held in an unencrypted state. To entry the trusted information held inside an enclave, processes should due to this fact function inside the similar enclave as properly, which limits the info’s assault floor simply to the enclave, dramatically simplifying safety. The enclave itself is protected utilizing encryption primarily based on {hardware} resident keys which can be inaccessible by software program.
2.1 Software Structure: Trusted and Untrusted Parts
The first necessities for utility software program to utilize Intel SGX are to generate enclaves and designate trusted parts of code that may function within them. Every trusted element is granted entry to the trusted reminiscence area that corresponds to a particular enclave that homes trusted information that it consumes, as illustrated in Determine 4. An utility can embrace a number of trusted elements, with every granted entry to a distinct enclave (or set of enclaves).
 Intel
IntelDetermine 4. Intel® SGX interplay between trusted and untrusted utility elements.
The Intel SGX SDK supplies the instruments for growth groups to designate trusted and untrusted parts of purposes, present communication between these parts, and create enclaves for trusted execution utilizing Intel SGX directions. By default, code is untrusted, which means that it doesn’t have entry to any enclave; that designation consists of privileged system software program such because the OS, BIOS, firmware, and so on. That property permits Intel SGX to make use of its hardware-based encryption to implement information isolation in opposition to any person, utility, or course of, no matter privilege stage.
2.2 Attestation: Protected Interactions Amongst Enclaves
The Intel® Attestation Service permits communication and interplay between Intel SGX enclaves with cryptographic standing verification of the trusted execution setting, primarily based on the {hardware} root of belief. Key attributes of an enclave which can be verifiable utilizing attestation embrace the next:
- The code is operating as-built in a real enclave
- The {hardware} is an Intel SGX-capable platform with all wanted microcode updates utilized
- All crucial Intel SGX {hardware} and software program configurations are made accurately
Attestation could contain enclaves which can be hosted on the identical platform or on separate platforms. The previous case is known as “native attestation” and is frequent, for instance, in order that a number of elements of a single utility—every in its personal enclave—can work collectively on shared duties. Distant attestation, however, supplies confidentiality and integrity assurances for communications between enclaves on separate hosts equivalent to verification between a server utility and a distant information supply, even over untrusted channels.
Constructed-In Crypto Acceleration Enhances Intel® SGX
Intel® SGX is a part of the platform-level method to securing cloud-native networks that’s designed into the third Era Intel® Xeon® Scalable processor. Among the many vary of hardware-resident security measures that complement Intel® SGX, the platform’s built-in hardware-based cryptographic acceleration is of explicit word. To assist mitigate the efficiency impacts of pervasive encryption, the platform supplies as much as 4.2x larger TLS encrypted connections per second.(4) Learn extra
3 Streamlined Workload Isolation: Anjuna Confidential Computing software program
Defending information in use utilizing Intel SGX enclaves permits computations to be carried out on it with out exposing it within the clear. Benefiting from this functionality usually requires modifying purposes to designate trusted parts of code that function contained in the enclave. To cut back the related coaching and operational necessities on growth groups, Anjuna Confidential Computing software program supplies the flexibility to run any utility in an Intel SGX enclave with out requiring any modifications to utility binaries. That simplification helps speed up the time to profit from confidential computing tasks, in addition to permitting builders to deal with extra value-added work.
Anjuna Confidential Computing software program is constructed to function in any setting the place Intel SGX sources can be found, together with both on-premises or on infrastructure-as-a service equivalent to Microsoft Azure. It integrates simply with present instruments and workflows, together with modernization and transformation initiatives equivalent to DevOps and DevSecOps. The platform is deeply optimized and enabled for Intel structure, to guard workloads in Intel SGX enclaves augmented with hardware-accelerated encryption and {hardware} roots of belief, throughout in the present day’s distributed cloud perimeter. It maintains a zero-trust community infrastructure that successfully obscures the presence of secrets and techniques in addition to offering strong entry management. Flexibility advantages of Anjuna Confidential Computing software program embrace the next:
- Any utility. No code modifications or recompilation are wanted, extending help transparently to customized, packaged, and legacy purposes in addition to container platforms together with Purple Hat® OpenShift®.
- Any cloud. Anjuna Confidential Computing software program is constructed for the multi-cloud world, together with non-public and hybrid clouds together with public ones equivalent to Azure.
- Any scale. The platform handles any variety of nodes, with minimal efficiency impression and safety that traverses a number of clouds together with information and purposes.
Confidential computing capabilities primarily based on Anjuna
Confidential Computing software program simply combine into present infrastructure and operations.
Customary APIs combine out of the field with present administration programs equivalent to safety info and occasion administration (SIEM). The software program is deployed on every cloud occasion, and it mechanically isolates information and code utilizing Intel SGX, together with the deployment and operation of HashiCorp Vault in enclaves.
Constructed-In Crypto Acceleration Enhances Intel® SGX
4 Secret and Encryption Administration: HashiCorp Vault
Defending utility secrets and techniques equivalent to encryption keys, passwords, tokens, certificates, and different delicate information is the core purpose of confidential computing. HashiCorp Vault is a extensively adopted secrets and techniques administration instrument that runs encryption, authentication, and authorization providers to allow safe storage, administration, management, and auditability of secrets and techniques. Past defending entry, Vault additionally supplies monitoring and governance, making it attainable to grasp what events, purposes, and providers are accessing particular secrets and techniques, throughout platforms.
Key options of Vault embrace the next:
- Safe secret storage. Vault encrypts secret key/worth pairs earlier than writing them to storage, offering an added layer of safety past defending the storage itself.
- Dynamic secrets and techniques. Vault can generate short-lived secrets and techniques on demand, equivalent to credentials for a database or S3 storage quantity, and mechanically revoke them after use.
- Reside information encryption. Vault can encrypt and decrypt information with out storing it, enabling builders to retailer encrypted information in databases or different typical information shops with out defining encryption schemes.
- Leasing and renewal. Vault maintains leases for every secret, to control computerized revocation of the key at finish of-lease; built-in APIs present the mechanism for purchasers to resume secrets and techniques.
- Constructed-in secret revocation. Vault automates revoking units of secrets and techniques, equivalent to all secrets and techniques of a given sort or which were accessed by a given person, which is efficacious for each key rolling and intrusion response.
5 Cloud-Native Infrastructure: Purple Hat® OpenShift®
Purple Hat OpenShift Container Platform is a Kubernetesbased, enterprise-grade software program basis for cloudnative infrastructure, as illustrated in Determine 5. OpenShift permits growth groups to undertake utility topologies primarily based on containerized microservices, a key requirement for contemporary approaches equivalent to DevOps and DevSecOps. It automates deployment, administration, and upkeep features to optimize administrator effectivity, with added providers equivalent to networking, monitoring, registry, and authentication to additional streamline deployments.
 Intel
IntelDetermine 5. Purple Hat® OpenShift®.
Developed and distributed as open supply to foster innovation, OpenShift is hardened, examined, and authorized by Purple Hat engineers, bettering total safety posture. OpenShift additionally incorporates the hardened Purple Hat Enterprise Linux CoreOS, which is designed particularly for operating containerized purposes.
Multi-cloud-ready by design, OpenShift supplies a constant platform to implement and orchestrate containers throughout any mixture of on-premises, hosted, and public cloud compute nodes, to dynamically present enterprise providers when and the place they’re wanted.
6 Use Case: Anjuna Software program Operating HashiCorp Vault in an Intel SGX Enclave
This use case demonstrates the steps wanted to deploy HashiCorp Vault in an Intel SGX enclave utilizing Anjuna Confidential Computing software program in a Purple Hat OpenShift cloud-native container setting. It additionally briefly introduces the applicability of this implementation to hardening the DevSecOps pipeline and software program provide chain.
The Anjuna Confidential Computing software program simplifies the duty of operating HashiCorp Vault inside an Intel SGX enclave. Setup and configuration require minor modifications to the Dockerfile and docker-entrypoint.sh script offered by HashiCorp, as detailed beneath.
6.1 Modifying the Dockerfile
The method of operating HashiCorp Vault inside an enclave begins with modifications to the Dockerfile that HashiCorp supplies for making a Purple Hat Common Base Picture (UBI) container for OpenShift. The Dockerfile is accessible at https://bitbucket.org/anjunasec/partner-hashicorp/src/grasp/Dockerfile.
6.1.1 Including the Anjuna Confidential Computing software program and Dependencies to the Picture
RUN wget https://downloads.anjuna.io/anjunasecurity.
releases/release-1.34/0002/anjuna-with-deps-rhel-8.
tar.gz && tar -zxvf anjuna-with-deps-rhel-8.tar.gz
–directory /
RUN chown -R vault /anjuna &&
groupadd –gid 1001 sgx_prv &&
usermod -a -G sgx_prv vault
RUN mkdir /runtime && chown -R vault /runtime
6.1.2 Establishing Anjuna Confidential Computing software program Setting Variables
WORKDIR /runtime
ENV PATH=”/anjuna/bin:/anjuna/instruments:${PATH}”
ENV ANJUNA_DIR=/anjuna/
ENV ANJUNA_BIN_DIR=/anjuna/bin
ENV SGX_SIGNER_KEY=/anjuna/signing/enclave-key.pem
ENV AZDCAP_DEBUG_LOG_LEVEL=error
6.2 Modifying the docker-entrypoint.sh script
A minor change can be required to the docker-entrypoint.sh script offered by HashiCorp at https://github.com/hashicorp/docker-vault/blob/grasp/ubi/docker-entrypoint.sh.
To run HashiCorp Vault inside an Intel SGX enclave utilizing the Anjuna Confidential Computing software program, the second-to-thelast line within the script have to be modified from
exec “$@”
to
exec anjuna-sgxrun $@
6.3 HashiCorp Vault Use Case Implementation
To offer an end-to-end confidential computing platform, the Anjuna Confidential Computing software program supplies the Anjuna Coverage Supervisor. The Anjuna Coverage Supervisor makes use of the HashiCorp plug-in structure to offer entry to secrets and techniques in HashiCorp Vault, primarily based on attestation from the Intel SGX enclave utilizing the Anjuna Confidential Computing software program. Anjuna Coverage Supervisor itself runs inside an Intel SGX enclave, additionally utilizing the Anjuna Confidential Computing software program. The answer creates a coverage in Anjuna Coverage Supervisor to offer a secret solely to a consumer operating inside an Intel SGX enclave that may present an attestation quote with a particular MRSIGNER (signing id) worth, and if wanted, a particular MRENCLAVE (enclave id) worth.
Within the instance proven in Determine 6, a signing element runs inside a protected enclave and supplies an attestation quote to acquire the signing key. Thus, solely a binary that’s trusted primarily based on its measurements and signature can entry the signing key and use it contained in the enclave.
 Intel
IntelDetermine 6. Signing element operating inside an Intel® SGX enclave.
7 Conclusion
Confidential computing is a crucial enabler for delicate workloads, defending information in use with a hardware-based root of belief. Intel SGX supplies the silicon-resident foundations for confidential computing, with enclaves of protected reminiscence that home utility secrets and techniques and the code that acts on them. Anjuna Confidential Computing software program streamlines deployment of HashiCorp Vault utilizing Intel SGX enclaves, striving to offer an built-in {hardware} and software program answer to optimize management over utility secrets and techniques. Cloud-native implementation on Purple Hat OpenShift supplies a sturdy automation layer that drives effectivity good points into future-focused initiatives equivalent to DevOps and DevSecOps.
The answer stack described on this paper supplies a comparatively easy method to deploying confidential computing providers in a multi-cloud setting. This mannequin helps defend consumption of delicate information, even throughout distributed networks, and contributes to a way forward for privateness protected data-rich computing.
Extra Info
Intel® SGX: intel.com/content material/www/us/en/architecture-andtechnology/
software-guard-extensions.html
Anjuna® Confidential Computing software program: anjuna.io/product
HashiCorp Vault: https://www.hashicorp.com/merchandise/vault
Purple Hat® OpenShift®: redhat.com/en/applied sciences/cloudcomputing/
Contributors/Writers:
Anjuna: Ofir Azoulay-Rozanes – ofir@anjuna.io
HashiCorp: Alex Cahn – acahn@hashicorp.com
Intel: Darren Pulsipher darren.w.pulsipher@intel.com;
Raghu Moorthy raghu.ok.moorthy@intel.com
1 Safety Week, January 20, 2022. “Software program Provide Chain Assaults Tripled in 2021: Examine.” https://www.securityweek.com/software-supply-chain-attacks-tripled-2021-study.
2 Irregular Safety, April 13, 2022. “New Analysis Reveals 67% Likelihood of Provide Chain Compromise Assault.”
https://abnormalsecurity.com/weblog/new-research-supply-chain-compromise-attack.
3 Confidential Computing Consortium. https://confidentialcomputing.io/.
4 See [70], [90], [71], and [69] at third Era Intel® Xeon® Scalable Processors – 1 – ID:615781 |Efficiency Index. Testing by Intel as of August 4, 2020. Efficiency comparisons relative to 2nd Gen Intel® Xeon® Scalable processors utilizing a single buffer algorithm versus multi-buffer algorithms for third Gen Intel Xeon Scalable processors. Outcomes have been estimated primarily based on pre-production checks at iso core depend and frequency as of August 2020. Efficiency good points are proven for particular person cryptographic algorithms.
Copyright © 2022 Purple Hat, Inc. Purple Hat, the Purple Hat brand, and OpenShift are emblems or registered emblems of Purple Hat, Inc. or its subsidiaries in the USA and different international locations.
Linux® is the registered trademark of Linus Torvalds within the U.S. and different international locations.
Efficiency varies by use, configuration and different elements. Study extra at www.intel.com/PerformanceIndex.
Efficiency outcomes are primarily based on testing as of dates proven in configurations and will not mirror all publicly out there updates. See configuration disclosure for configuration particulars. No product or element will be completely safe.
Intel doesn’t management or audit third-party information. You need to seek the advice of different sources to guage accuracy.
Your prices and outcomes could differ.
Intel applied sciences could require enabled {hardware}, software program or service activation.
Copyright © 2022 IDG Communications, Inc.


