Dp you keep in mind a number of years in the past when everybody panicked over a few safety flaws referred to as Meltdown and Spectre? These had been a brand new kind of safety gap altogether, referred to as speculative execution flaws as a result of they exploit the so-named functionality of contemporary processors. That was again in 2018, and since then, each tech firm below the solar has issued patches, firmware updates, and different steering to mitigate the hazard of those assaults.
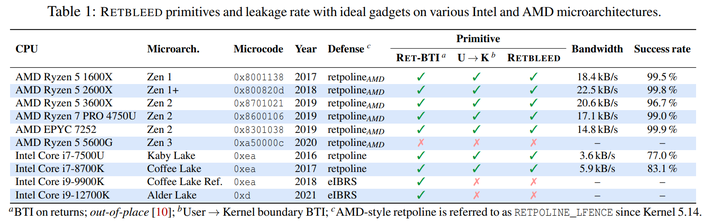
With out moving into the technical weeds, the place earlier Spectre assaults focused oblique calls and jumps, retbleed as a substitute targets returns. It really works on each Intel and AMD machines, though it is drastically more practical on the latter. Like earlier Spectre assaults, as soon as executed, it may possibly enable any utility executing on the goal CPU to learn any reminiscence, no matter whether or not it has the authority to take action.
Everybody studying this could flip out and rush to patch their techniques, proper? No, in all probability not. Whereas retbleed is a really critical vulnerability, it solely impacts sure {hardware}: Intel machines from the sixth via eighth era Core households, and AMD Zen, Zen+, and Zen 2 techniques. Intel says that it is also robotically mitigated by current variations of Home windows, which have Oblique Department Restricted Hypothesis (IBRS) enabled by default. IBRS is an efficient mitigation towards retbleed, so Home windows techniques are basically inoculated already.
Linux customers on affected machines do have trigger for concern, although, and that significantly extends to internet hosting suppliers and people that enable distant customers to login to their techniques with out supervision. Each AMD and Intel say that they don’t seem to be conscious of anybody making use of those vulnerabilities within the wild, however patches aren’t obtainable but. After they do turn into obtainable, they might include a efficiency hit of as a lot as 28%. Hopefully some intelligent coders will give you a technique to mitigate that efficiency loss.


