The Amadey malware is getting used to deploy LockBit 3.0 ransomware on compromised methods, researchers have warned.
“Amadey bot, the malware that’s used to put in LockBit, is being distributed via two strategies: one utilizing a malicious Phrase doc file, and the opposite utilizing an executable that takes the disguise of the Phrase file icon,” AhnLab Safety Emergency Response Heart (ASEC) stated in a brand new report printed right this moment.
Amadey, first found in 2018, is a “criminal-to-criminal (C2C) botnet infostealer mission,” as described by the BlackBerry Analysis and Intelligence Workforce, and is obtainable for buy on the legal underground for as a lot as $600.
Whereas its major operate is to reap delicate data from the contaminated hosts, it additional doubles up as a channel to ship next-stage artifacts. Earlier this July, it was unfold utilizing SmokeLoader, a malware with not-so-different options like itself.
Simply final month, ASEC additionally discovered the malware distributed underneath the disguise of KakaoTalk, an instantaneous messaging service standard in South Korea, as a part of a phishing marketing campaign.
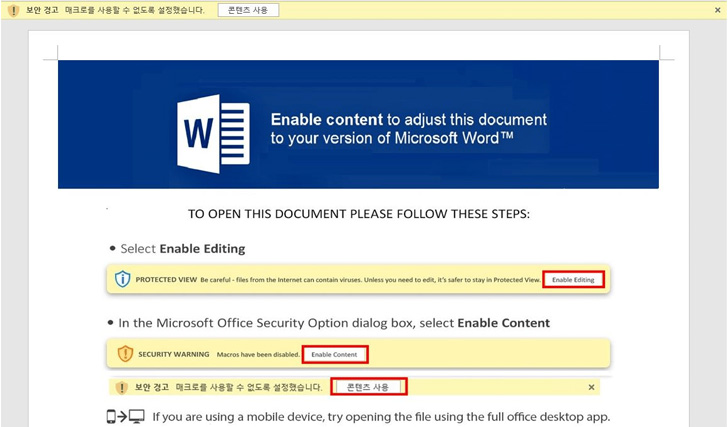
The cybersecurity agency’s newest evaluation relies on a Microsoft Phrase file (“심시아.docx“) that was uploaded to VirusTotal on October 28, 2022. The doc comprises a malicious VBA macro that, when enabled by the sufferer, runs a PowerShell command to obtain and run Amadey.
In an alternate assault chain, Amadey is disguised as a seemingly innocent file bearing a Phrase icon however is definitely an executable (“Resume.exe”) that is propagated by way of a phishing message. ASEC stated it was not capable of determine the e-mail used as a lure.
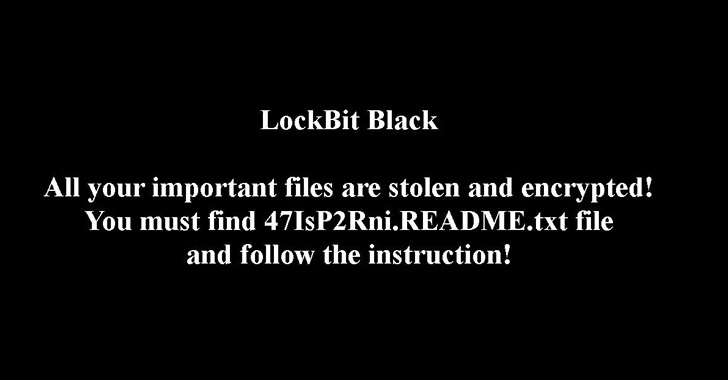
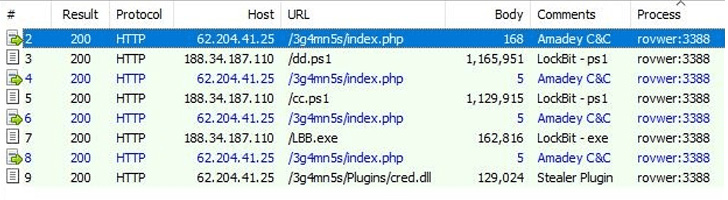
Succeeding within the execution of Amadey, the malware fetches and launches extra instructions from a distant server, which incorporates the LockBit ransomware both in PowerShell (.ps1) or binary (.exe) codecs.
LockBit 3.0, also called LockBit Black, launched in June 2022, alongside a brand new darkish internet portal and the very first bug bounty program for a ransomware operation, promising rewards of as much as $1 million for locating bugs in its web site and software program.
“As LockBit ransomware is being distributed via varied strategies, person warning is suggested,” the researchers concluded.