Almost each firm does enterprise with — or makes use of the merchandise of — a 3rd social gathering that has suffered a compromise, thus rising their safety dangers.
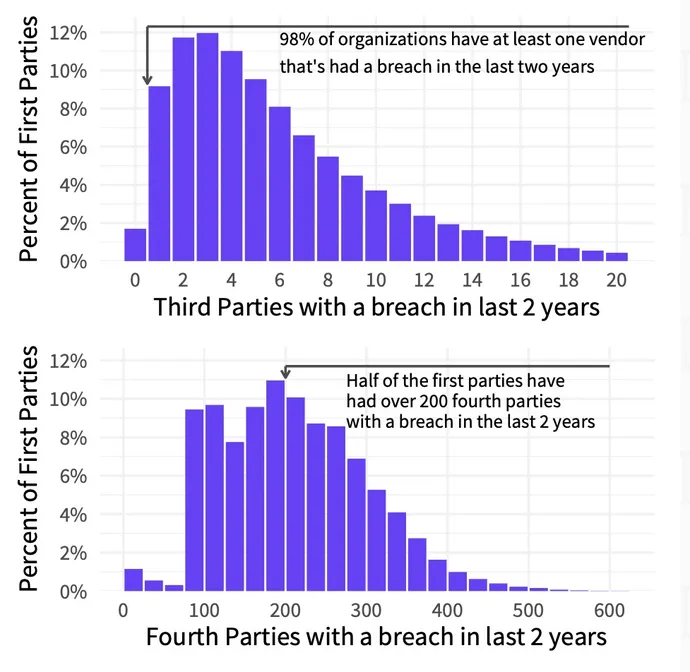
That is in line with knowledge science agency Cyentia Institute, which has issued an evaluation that features exterior measurements of safety from greater than 230,000 organizations supplied by cybersecurity risk-management agency SecurityScorecard. It discovered that the common agency had round 10 third-party relationships, and lots of of oblique fourth-party relationships, with the everyday agency having 60 to 90 instances extra fourth events than third events. Almost all companies (98%) had not less than one third-party companion who had suffered a breach, the report acknowledged.
The IT sector has probably the most third events, with a median of 25, whereas the finance sector had the fewest, at 6.5. These numbers shortly balloon when fourth-party relationships are included, as did their threat. The common agency has an oblique relationship with 200 fourth events which have had a breach, the evaluation discovered.
The analysis underscores the sprawling nature of third- and fourth-party relationships for firms, and the dramatic enhance in threat that they’ll trigger, says Wade Baker, founder and companion on the Cyentia Institute.
“Threat goes downhill,” he says. “The primary events usually tend to have good safety [risk] scores than their third events, and with fourth events, the numbers actually explode. It’s worthwhile to count on [these firms and products] to not be as much as your requirements for safety.”
That is as a result of whereas many organizations have develop into extra mature relating to their very own cyber dangers, few are cognizant of the prolonged dangers, Cyentia and SecurityScorecard acknowledged within the evaluation.
“Many organizations are nonetheless unaware of the dependencies and exposures inherent to third-party relationships, and easily deal with managing their very own safety posture,” the report acknowledged. “Others are conscious of these points, however do not make vendor choices primarily based on safety and/or require distributors to satisfy sure requirements. Even companies that do set up third-party safety necessities can battle to repeatedly monitor compliance and progress.”
Third-party and supply-chain threat have develop into vital points in recent times. And CISOs have develop into rising cautious of their third-party suppliers, ever because the compromise of an HVAC provider led to the breach of retail big Goal.
Whereas the evaluation seems at third-party threat, the definition of what a 3rd social gathering is extends not simply to distributors and companions, however software program suppliers and open supply initiatives. Now-infamous assaults on software program suppliers similar to SolarWinds, and vulnerabilities in extensively used software program elements similar to Log4J, have raised the visibility of the chance that this enviornment poses.
The highest 5 applied sciences included in third-party relationships throughout the knowledge are Google Analytics, Google Tag Supervisor, Amazon Internet Internet hosting, PHP, and Fb merchandise — all of which have been concerned in two-thirds (68%) of third-party relationships, the report acknowledged.
“Loads of these third and fourth social gathering relationships [involve us] each agreeing to stick to sure insurance policies simply by advantage of utilizing a product, and now I am opening up myself to a sure diploma of threat,” Baker says.
Threat Rises With Every Hop
The evaluation additionally discovered that third events sometimes have a weaker safety posture than the businesses they served. Total, there’s a a lot increased probability that third events may have safety issues, which means that firms cannot assume that each one of their third events are as diligent about safety.
“I view it in the identical manner as all of us realizing we now have too many privileges — generally, folks have entry to extra knowledge than they should do their job,” Baker says. “It might be good to scale back the variety of third events, particularly if they don’t seem to be wanted, and in addition be slightly bit extra picky.”
The info, nevertheless, doesn’t counsel a transparent path ahead, beside changing into extra conscious of the issue. Baker doesn’t essentially suggest, for instance, that organizations minimize the underside 25% of their third events from their enterprise. Nonetheless, evaluating them extra carefully or extra regularly may be extra life like, he says.
“If we actually need to shield our provide chains, we have got to we have got to make the weakest hyperlink stronger,” Baker says. “And I believe the evaluation is displaying that there is a whole lot of weak hyperlinks throughout third events and fourth events, and that’s the place the problem lies.”


