Now Microsoft has printed particulars concerning a classy phishing marketing campaign with the flexibility to bypass multi-factor authentication (MFA). Many phishing assaults ship unsuspecting victims to a login web page that mimics a legit and reliable web site, however that truly has no connection to the legit website and as a substitute merely steals person credentials. The attacker can later use these credentials to login to the victims’ accounts. MFA strategies like time-based one-time passwords (TOTP) might help stop these kinds of phishing assaults from succeeding by requiring that customers should enter a time-sensitive code to be able to full the login course of. Within the case of TOTP, the required code is legitimate inside solely a thirty second window, rendering phishing assaults that harvest person credentials for later use ineffective.
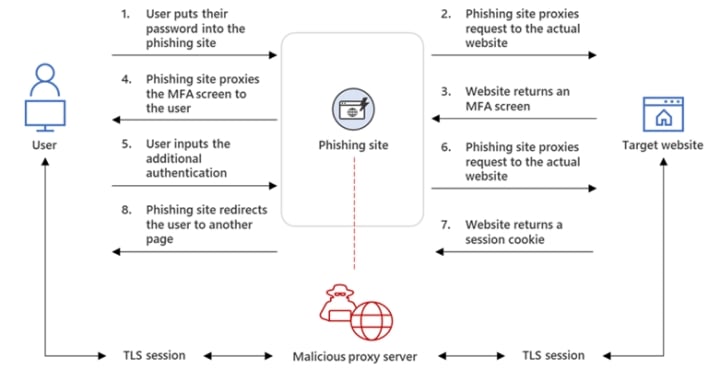
If the person credentials are legitimate and MFA is enabled, then the legit web site returns an MFA immediate, which the malicious server proxies again to the person. Upon finishing the required MFA step, the phishing website passes the authentication data on to the legit web site, which points a session cookie that may usually confirm the person’s ongoing authenticated session. Nevertheless, for the reason that cookie was issued to the malicious server, the attacker good points an authenticated session, quite than the sufferer.
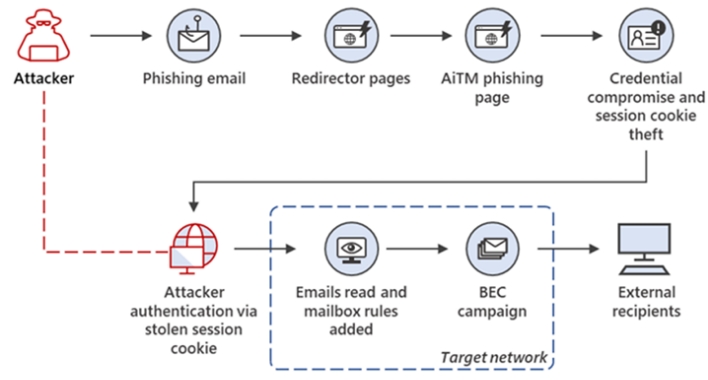
The phishing marketing campaign targets Outlook electronic mail accounts, enabling the attacker to entry victims’ monetary emails with the aim of discovering ongoing electronic mail threads. If such a thread is current, the attacker tries to persuade the sufferer’s correspondents to ship funds to accounts managed by the attacker. Microsoft additionally discovered that the attacker deletes the unique phishing electronic mail to take away an indication of compromise and units up inbox guidelines that conceal the attacker’s correspondence with monetary fraud targets.
This phishing marketing campaign’s potential to bypass MFA measures is alarming, however Microsoft emphasizes that the marketing campaign isn’t leveraging any type of vulnerability in MFA itself. “[S]ince AiTM phishing steals the session cookie, the attacker will get authenticated to a session on the person’s behalf, whatever the sign-in methodology the latter makes use of.” MFA nonetheless will increase safety; it merely doesn’t shield in opposition to this specific type of assault.


