An Indian airline says that an “tried ransomware assault” towards its IT infrastructure prompted flights to be delayed or canceled, and left passengers stranded.
Flights with in style Indian price range airline SpiceJet have been disrupted by the cyber assault on Tuesday night time, however the agency initially downplayed the influence of the assault – claiming that it had merely “slowed down morning flight departures”.
In a tweet, SpiceJet claimed that it had now “rectified the state of affairs” and that each one flights have been “working usually”
Nevertheless, some passengers shared pictures and movies on social media demonstrating that they’d waited hours to be boarded, with none info being offered by SpiceJet, lengthy after the corporate claimed to have resolved the problem.
Others, pissed off by the disruption to their journeys, stated that they’d tried to contact the airline’s buyer care division by way of phone, WhatsApp, and its automated customer support agent “Ms Pepper,” with out success.
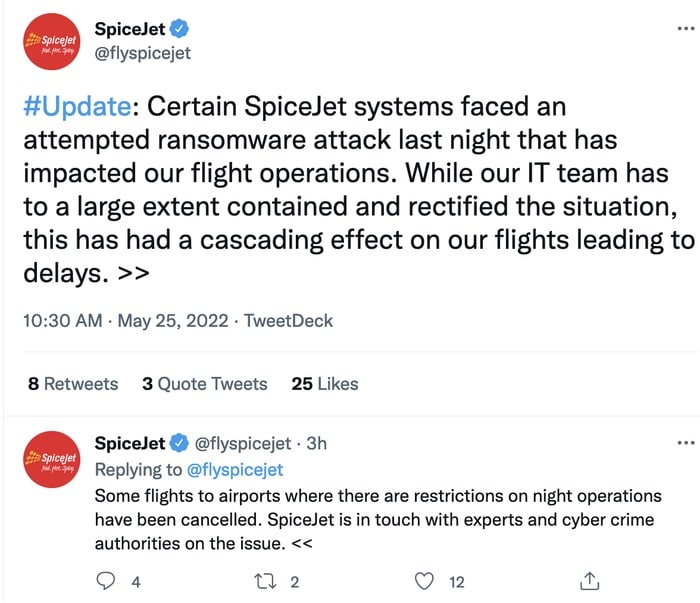
In its most up-to-date replace, SpiceJet says that though it believes its IT staff has “to a big extent contained and rectified the state of affairs,” there was a knock-on impact to flights which has resulted in delays.
One high-profile individual affected was Indian politician Dr. Satish Poonia, who expressed his disappointment each at his delayed journey, but additionally the shortage of a proof. Dr. Poonia described the corporate’s dealing with of the delay as “very shameful, gross negligence.”
On the time of writing, it’s unclear which ransomware operation could have attacked SpiceJet, and no particulars have been shared as to the extent of harm it could have prompted.
Nevertheless, all companies could be smart to undertake the tried-and-trusted greatest practices which may also help strengthen networks towards ransomware assaults.
These embrace, however aren’t restricted to, patching software program, utilizing distinctive and robust passwords, enabling multi-factor authentication, disabling unused distant entry ports and monitoring logs, auditing person accounts with admin privileges, and guaranteeing that essential knowledge is safely backed up.
As well as, staff must be educated in regards to the threats and educated to find out how ransomware assaults may be disguised.


