135. Simplifying cybersecurity insurance policies and code to restrict danger and cut back overhead
It is a continuation of my sequence on Automating Cybersecurity Metrics and can be relevant to my sequence on Safe Code By Design.
Within the final submit, I wrote about privilege escalation in a cloud account (AWS particularly, however it applies to any cloud setting.)
Now we wish to attempt to write the insurance policies utilizing the approaches I discussed in these weblog posts. Earlier than we do this I wish to make clear one thing I wrote about beforehand as it’s relevant to writing IAM insurance policies with as few strains of code as doable and nonetheless obtain an accurate consequence.
I’ve referenced the time period abstraction in a number of weblog posts. I speak about abstraction when it comes to taking your insurance policies and decreasing them all the way down to the issues which might be frequent into the next stage coverage.
I just lately noticed the phrase abstraction utilized in a unique method, and utilized to cybersecurity. I suppose that definition works however it’s not what I imply after I speak about abstraction, so it prompted me to put in writing this weblog submit.
The place did I get this idea of abstraction? From the identical place I got here up with the idea of immutable infrastructure — years of Java programming. Ideas used to cut back code and write reusable parts in Java and different object oriented programming languages can be utilized to put in writing higher cybersecurity insurance policies.
Summary Class
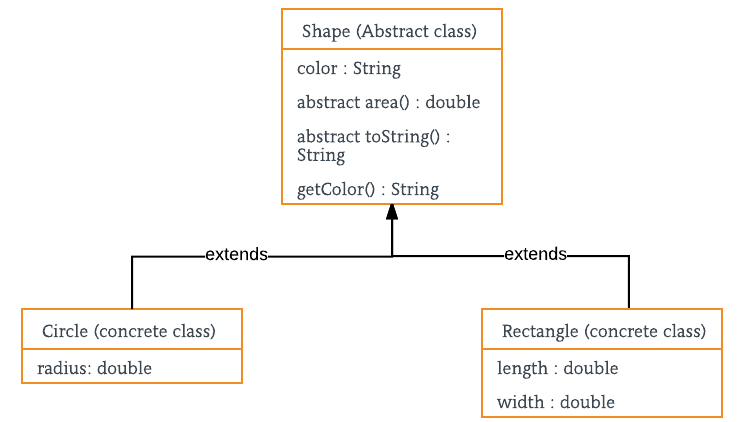
In Java you possibly can create an summary class. You can not instantiate an summary class. As a substitute you employ an summary class as the premise for creating different courses with frequent properties however completely different implementations. For instance, a form has some frequent properties, no matter whether or not it’s a circle, a sq. or a triangle. For the sake of time and to not reinvent the wheel I’ll reference this class diagram from geeksforgeeks.com (and I may draw up my very own picture if wanted utilizing vehicles, fruit, animals, or no matter.)
Within the instance above, a form at all times has sure properties. On this instance, all shapes have a colour, an space, and a “toString()” perform which may return no matter string a developer desires to return for that individual form.
The frequent properties have been extracted or in different phrases the small print are abstracted to create greater stage class with all of the frequent properties for a selected kind of objects.
The courses that stretch that summary class are of the identical kind because the summary class however will fill of their specific implementation. In different phrases, the implementation of calculating the realm for a circle will differ from that of a rectangle or a triangle.
Abstraction in cloud code and cloud safety insurance policies
Whenever you create a CloudFormation template you possibly can take away the small print that modify and extract the frequent properties into parameters. These parameters that get populated when the template will get executed.
Every specific execution of the template could have a unique implementation leading to a unique useful resource by passing in numerous parameter values. Nonetheless, all of the stacks can use a single template for his or her underlying definition.
That’s what I’m referring to after I speak about abstraction.
Once I lookup the phrases abstraction and Java abstraction I discover many ranging definitions. The explanation I used the time period “abstraction” is as a result of an summary class is an idea in Java much like the idea I’m attempting to elucidate. The summary class comprises the properties and strategies which might be frequent to all of the courses that stretch that summary class.
Different courses can lengthen and construct on the category as proven within the following instance, however they need to embody and implement the properties and strategies within the summary class.
On this instance beneath, courtesy of Oracle, the Circle extends a Graphic Object and fills within the particular implementation of the placeholder strategies offered by the summary class.
Within the instance above, the category that extends the summary class has to implement the strategies outlined by the summary class however it may additionally add its personal performance.
DRY — Don’t repeat your self
I discussed the DRY idea in my sequence on software program safety. The much less code you write, the much less potential bugs or typos will exist in your software.
I wrote about DRY — Don’t repeat your self — in these two weblog posts and a few others:
The summary class itself, not like an interface in Java, can embody implementation, or in different phrases performance. You may implement some code and every class that extends that summary class will embody that code.
If each “GraphicObject” in our instance above (or Form within the prior instance) goes to repeat the identical code time and again as a result of each implements the identical performance, it makes extra sense to maneuver that frequent performance into the summary class. That means every class that extends the summary class is not going to be repeating the identical code time and again. It’ll get that code when it extends the summary class.
The thought right here can be utilized when creating IAM insurance policies. You summary out the smallest doable coverage that’s frequent throughout a lot of sources and use that, let’s say, for all customers. Then you definately create extra particular insurance policies on prime of that solely the place required as an alternative of repeating the identical code time and again.
The identical idea applies in networking. You don’t wish to create a single safety group for each single software in the event you can summary out a lot of frequent guidelines that each software will want right into a single, reusable group. Then you possibly can apply that reusable group wherever doable, and add the distinctive guidelines in a separate group in the event you want them.
In a CloudFormation coverage, you possibly can “summary” or “extract” the values that change from template to template and go them in as parameters. Then you possibly can reuse all of the code in that template that’s the similar throughout all the identical sorts of sources. That’s what I did after I created a single template to create all of the KMS keys in your group from a single template.
That’s what I did when creating safety teams within the above framework for batch jobs, which has was a full-on AWS structure from begin to end. I began down the rabbit-hole of safe automation and now I’m digging my means out.
Defining Abstraction in Cybersecurity
Whereas looking for definitions of abstraction many variations offered themselves however I believe this definition is the closest to the idea I’m attempting to convey after I use the phrase abstraction:
Abstraction (from the Latin abs, that means away from and trahere , that means to attract) is the method of taking away or eradicating traits from one thing as a way to cut back it to a set of important traits.
Sure, there are different definitions, however the level I’m attempting to make to simplify administration of your safety sources is in keeping with that definition. If you wish to use one other definition for another objective, be at liberty, however that isn’t what I imply after I’m speaking about utilizing the principal of abstraction to easily your safety administration.
We wish to cut back and extract all of the frequent properties into the highest-level, easiest coverage, after which lengthen that coverage as wanted, solely including complexity and addition phrases and code the place they’re completely required. We’ll strive to do this within the upcoming insurance policies to stop the sorts of privilege escalation I wrote about on AWS in the previous few posts.
The least phrases to explain a thought — appropriately — are finest. Or to paraphrase Mark Twain — if I had extra time, I might write a shorter weblog submit.
Extra posts on Abstraction:
Observe for updates.
Teri Radichel
When you appreciated this story ~ clap, observe, tip, purchase me a espresso, or rent me
Medium: Teri Radichel
Electronic mail Checklist: Teri Radichel
Twitter: @teriradichel
Twitter (firm): @2ndSightLab
Mastodon: @teriradichel@infosec.change
Put up: @teriradichel
Fb: 2nd Sight Lab
Slideshare: Shows by Teri Radichel
Speakerdeck: Shows by Teri Radichel
Books: Teri Radichel on Amazon
Recognition: SANS Distinction Makers Award, AWS Hero, IANS College
Certifications: SANS
Training: BA Enterprise, Grasp of Sofware Engineering, Grasp of Infosec
How I received into safety: Lady in tech
Purchase me a espresso: Teri Radichel
Firm (Penetration Exams, Assessments, Coaching): 2nd Sight Lab
Request providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2023
All of the posts on this sequence:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts