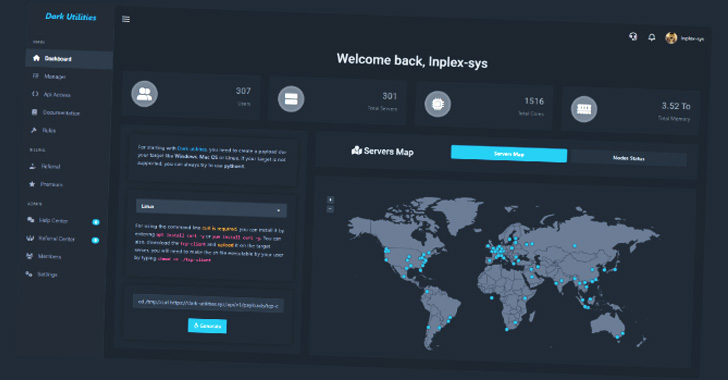
A nascent service referred to as Darkish Utilities has already attracted 3,000 customers for its means to offer command-and-control (C2) companies with the objective of commandeering compromised methods.
“It’s marketed as a way to allow distant entry, command execution, distributed denial-of-service (DDoS) assaults and cryptocurrency mining operations on contaminated methods,” Cisco Talos stated in a report shared with The Hacker Information.
Darkish Utilities, which emerged in early 2022, is marketed as a “C2-as-a-Service” (C2aaS), providing entry to infrastructure hosted on the clearnet in addition to the TOR community and related payloads with help for Home windows, Linux, and Python-based implementations for a mere €9.99.
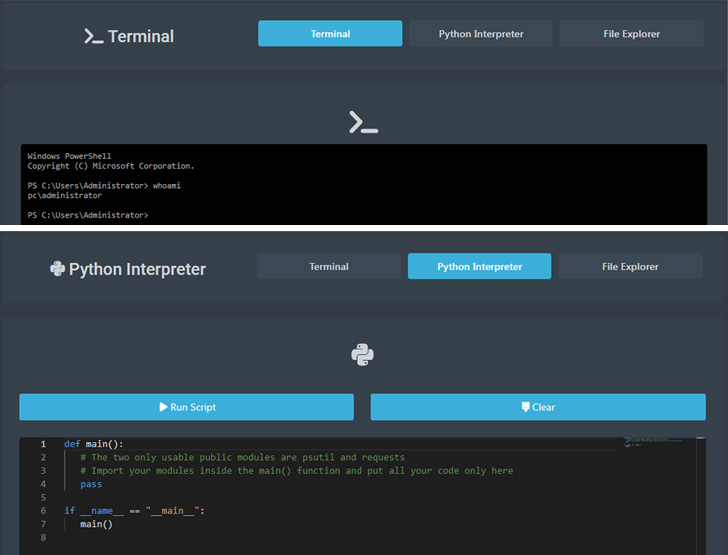
Authenticated customers on the platform are introduced with a dashboard that makes it doable to generate new payloads tailor-made to a particular working system that may then be deployed and executed on sufferer hosts.
Moreover, customers are supplied an administrative panel to run instructions on the machines below their management upon establishing an lively C2 channel, successfully granting the attacker full entry to the methods.
The thought is to allow risk actors to focus on a number of architectures with out requiring vital growth efforts. Additionally prolonged to its prospects are technical help and help via Discord and Telegram.
“Given the comparatively low price in comparison with the quantity of performance the platform presents, it’s probably engaging to adversaries trying to compromise methods with out requiring them to create their very own C2 implementation inside their malware payloads,” the researchers famous.
So as to add gas to the fireplace, the malware artifacts are hosted inside the decentralized InterPlanetary File System (IPFS) resolution, making them resilient to content material moderation or regulation enforcement intervention in a way just like “bulletproof internet hosting.”
“IPFS is at the moment being abused by a wide range of risk actors who’re utilizing it to host malicious contents as a part of phishing and malware distribution campaigns,” Talos researcher Edmund Brumaghin instructed The Hacker Information.
“[The IPFS gateway] allows computer systems on the web to entry contents hosted inside the IPFS community with out the requirement for a shopper software program set up, just like how Tor2Web gateways present that performance for content material hosted inside the Tor community.”
Darkish Utilities is believed to be the handiwork of a risk actor who goes by the moniker Inplex-sys within the cybercriminal underground house, with Talos figuring out some kind of a “collaborative relationship” between Inplex-sys and one of many operators of a botnet service referred to as Good Bot.
“Platforms like Darkish Utilities decrease the barrier to entry for cybercriminals coming into the risk panorama by enabling them to shortly launch assaults focusing on a wide range of working methods,” the researchers stated.
“In addition they provide a number of strategies that can be utilized to additional monetize entry gained to methods in company environments and will result in additional deployment of malware within the setting as soon as preliminary entry has been obtained.”