Quite a lot of phishing campaigns are leveraging the decentralized Interplanetary Filesystem (IPFS) community to host malware, phishing package infrastructure, and facilitate different assaults.
“A number of malware households are at the moment being hosted inside IPFS and retrieved throughout the preliminary phases of malware assaults,” Cisco Talos researcher Edmund Brumaghin stated in an evaluation shared with The Hacker Information.
The analysis mirrors related findings from Trustwave SpiderLabs in July 2022, which discovered greater than 3,000 emails containing IPFS phishing URLs as an assault vector, calling IPFS the brand new “hotbed” for internet hosting phishing websites.
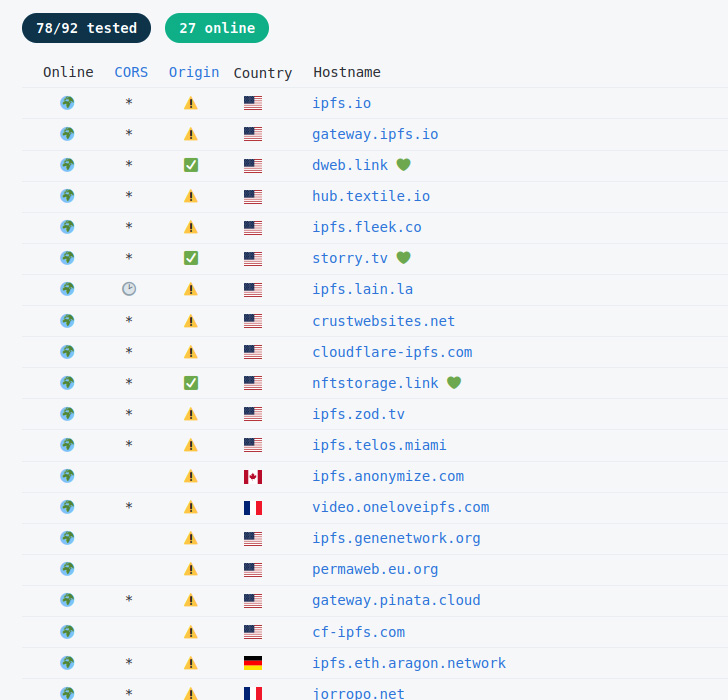
IPFS as a know-how is each resilient to censorship and takedowns, making it a double-edged sword. Underlying it’s a peer-to-peer (P2P) community which replicates content material throughout all taking part nodes in order that even when content material is faraway from one machine, requests for the assets can nonetheless be served by way of different techniques.
This additionally makes it ripe for abuse by dangerous actors trying to host malware that may resist legislation enforcement makes an attempt at disrupting their assault infrastructure, like seen within the case of Emotet final yr.
“IPFS is at the moment being abused by a wide range of menace actors who’re utilizing it to host malicious contents as a part of phishing and malware distribution campaigns,” Brumaghin beforehand advised The Hacker Information in August 2022.
This contains Darkish Utilities, a command-and-control (C2) framework that is marketed as a manner for adversaries to avail distant system entry, DDoS capabilities, and cryptocurrency mining, with the payload binaries offered by the platform hosted in IPFS.
Moreover, IPFS has been put to make use of to serve rogue touchdown pages as a part of phishing campaigns orchestrated to steal credentials and distribute a variety of malware comprising Agent Tesla, reverse shells, information wiper, and an data stealer known as Hannabi Grabber.
In a single malspam supply chain detailed by Talos, an electronic mail purporting to be from a Turkish monetary establishment urged the recipient to open a ZIP file attachment that, when launched, labored as a downloader to retrieve an obfuscated model of Agent Tesla hosted inside the IPFS community.
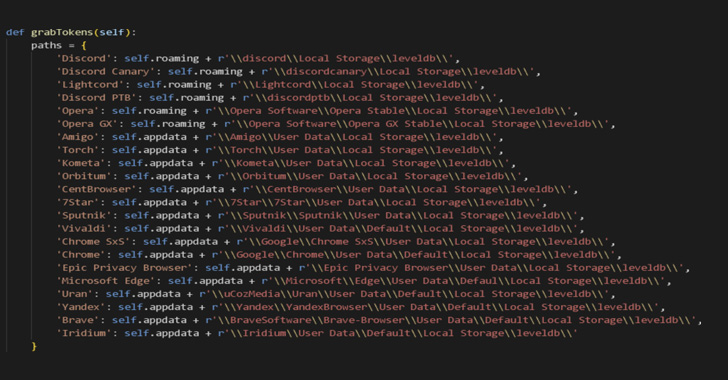
The harmful malware, for its half, takes the type of a batch file that deletes backups and recursively purges all listing contents. Hannabi Grabber is a Python-based malware that gathers delicate data from the contaminated host, comparable to browser information and screenshots, and transmits it by way of a Discord Webhook.
The newest improvement factors to the rising use by attackers of professional choices comparable to Discord, Slack, Telegram, Dropbox, Google Drive, AWS, and several other others to host malicious content material or to direct customers to it, making phishing one of many profitable main preliminary entry vectors.
“We anticipate this exercise to proceed to extend as extra menace actors acknowledge that IPFS can be utilized to facilitate bulletproof internet hosting, is resilient in opposition to content material moderation and legislation enforcement actions, and introduces issues for organizations trying to detect and defend in opposition to assaults which will leverage the IPFS community,” Brumaghin stated.