A “harmful piece of performance” has been found in Microsoft 365 suite that may very well be probably abused by a malicious actor to ransom information saved on SharePoint and OneDrive and launch assaults on cloud infrastructure.
The cloud ransomware assault makes it doable to launch file-encrypting malware to “encrypt information saved on SharePoint and OneDrive in a approach that makes them unrecoverable with out devoted backups or a decryption key from the attacker,” Proofpoint stated in a report printed as we speak.
The an infection sequence may be carried out utilizing a mixture of Microsoft APIs, command-line interface (CLI) scripts, and PowerShell scripts, the enterprise safety agency added.
The assault, at its core, hinges on a Microsoft 365 function known as AutoSave that creates copies of older file variations as and when customers make edits to a file saved on OneDrive or SharePoint On-line.
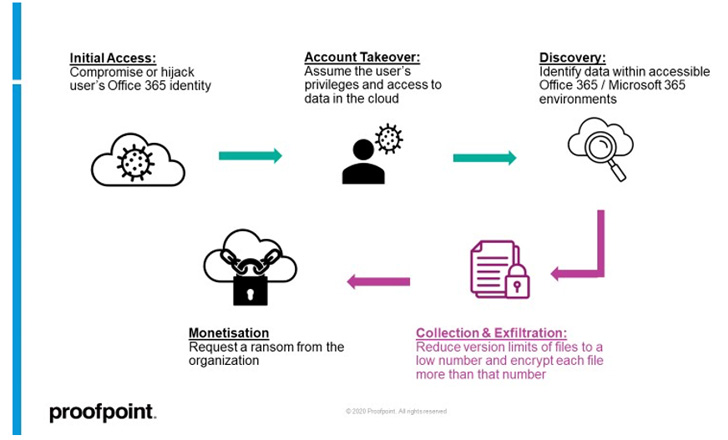
It commences with gaining unauthorized entry to a goal person’s SharePoint On-line or OneDrive account, adopted by abusing the entry to exfiltrate and encrypt information. The three most typical avenues to acquire the preliminary foothold contain immediately breaching the account by way of phishing or brute-force assaults, tricking a person into authorizing a rogue third-party OAuth utility, or taking on the online session of a logged-in person.
However the place this assault stands other than conventional endpoint ransomware exercise is that the encryption section requires locking every file on SharePoint On-line or OneDrive greater than the permitted versioning restrict.
Microsoft elaborates the versioning conduct in its documentation as follows –
Some organizations enable limitless variations of information and others apply limitations. You would possibly uncover, after checking within the newest model of a file, that an outdated model is lacking. In case your most up-to-date model is 101.0 and also you discover that there is no such thing as a longer a model 1.0, it implies that the administrator configured the library to permit solely 100 main variations of a file. The addition of the one hundred and first model causes the primary model to be deleted. Solely variations 2.0 by means of 101.0 stay. Equally, if a 102nd model is added, solely variations 3.0 by means of 102.0 stay.
By leveraging the entry to the account, an attacker can both create too many variations of a file or alternatively scale back the model restrict of a doc library to a decrease akin to “1” after which proceed to encrypt every file twice.
“Now all unique (pre-attacker) variations of the information are misplaced, leaving solely the encrypted variations of every file within the cloud account,” the researchers defined. “At this level, the attacker can ask for a ransom from the group.”
Microsoft, in response to the findings, identified that older variations of information may be probably recovered and restored for a further 14 days with the help of Microsoft Help, a course of that Proofpoint discovered to be unsuccessful.
Now we have reached out to the tech big for additional remark, and we are going to replace the story if we hear again.
To mitigate such assaults, it is advisable to implement a robust password coverage, mandate multi-factor authentication (MFA), stop large-scale knowledge downloads to unmanaged units, and keep periodic exterior backups of cloud information with delicate knowledge.
“Information saved in a hybrid state on each endpoint and cloud akin to by means of cloud sync folders will scale back the influence of this novel danger because the attacker won’t have entry to the native/endpoint information,” the researchers stated. “To carry out a full ransom movement, the attacker must compromise the endpoint and the cloud account to entry the endpoint and cloud-stored information.”