JSON Net Tokens (JWTs) are a preferred technique for coping with on-line authentication, and you’ll implement JWT authentication in any server-side programming language.
For background studying JWTs basically, I like to recommend studying extra about JWTs, finest practices, and securing RESTful APIs with JWTs with these articles on the LogRocket weblog.
This text is aimed toward serving to you get began with implementing JWT authentication in your Go net purposes utilizing the golang-jwt package deal.
The golang-jwt package deal is the preferred package deal for implementing JWTs in Go, owing to its options and ease of use. The golang-jwt package deal supplies performance for producing and validating JWTs.
Conditions
You’ll want to satisfy these primary necessities to get probably the most out of this tutorial.
- Go 1.16 or later put in in your machine (for safety causes)
- Expertise constructing net purposes in Go or another language (non-obligatory)
Desk of Contents
Getting began with the Golang-JWT package deal
After establishing your Go workspace and initializing the Go modules file go.mod, run this command in your terminal within the workspace listing to put in the golang-jwt package deal:
go get github.com/golang-jwt/jwt
When you’ve put in the golang-jwt, create a Go file and import these packages and modules.
import (
"log"
"encoding/json"
"github.com/golang-jwt/jwt"
"web/http"
"time"
)
You’ll use these packages on this tutorial to log errors, arrange a server, and set the token expiration time.
Establishing an online server in Go
Let’s begin with making a easy net server with an endpoint that will likely be secured with a JWT.
func foremost() {
http.HandleFunc("/residence", handlePage)
err := http.ListenAndServe(":8080", nil)
if err != nil {
log.Println("There was an error listening on port :8080", err)
}
}
The principle operate units up the house endpoint with a handler operate handlePage that you just’ll arrange. The handlePage operate will safe the web page utilizing JWTs. The server is about to hear on port :8080, however you should utilize any port of your alternative.
The handlePage handler operate will return the encoded JSON of the Message struct as a response to the consumer if the request is permitted after the request physique is encoded.
sort Message struct {
Standing string `json:"standing"`
Data string `json:"information"`
}
func handlePage(author http.ResponseWriter, request *http.Request) {
author.Header().Set("Content material-Kind", "software/json")
var message Message
err := json.NewDecoder(request.Physique).Decode(&message)
if err != nil {
return
}
err = json.NewEncoder(author).Encode(message)
if err != nil {
return
}
}
The handlePage operate, at this level, isn’t authenticated and making requests to the web page will work freely. You’ll learn to add authentication to your handler capabilities later on this tutorial.
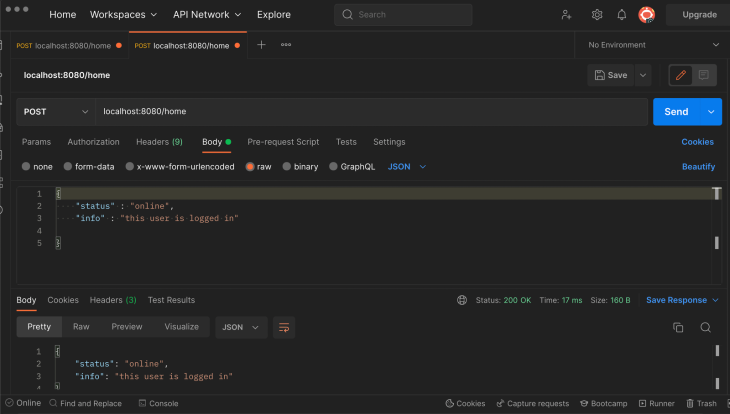
Producing JWTs for authentication utilizing the Golang-JWT package deal
You’ll need a secret key to generate JWT tokens utilizing the golang-jwt package deal. Right here’s an instance personal key for this tutorial; nonetheless, you must use a cryptographically safe string on your secret key and cargo it from an atmosphere variables file (.env).
Try this article to learn to use atmosphere variables in your Go purposes.
var sampleSecretKey = []byte("SecretYouShouldHide")
Kindly observe that whoever has the key key you utilize on your JWTs can authenticate customers of your software. The sampleSecretKey variable holds the personal key on this case.
Right here’s a operate for producing JWT tokens. The operate ought to return a string and an error. If there’s an error producing the JWT, the operate returns an empty string and the error. If there are not any errors, the operate returns the JWT string and the nil sort.
Extra nice articles from LogRocket:
func generateJWT() (string, error) {
}
You may create a brand new token utilizing the New technique of the JWT package deal. The New technique takes in a signing technique (the cryptographic algorithm for the JWT) and returns a JWT token.
token := jwt.New(jwt.SigningMethodEdDSA)
If you wish to modify the JWT, you should utilize the Claims technique of the token.
claims := token.Claims.(jwt.MapClaims) claims["exp"] = time.Now().Add(10 * time.Minute) claims["authorized"] = true claims["user"] = "username"
On this case, you’re setting an expiry time for the JWT, which is ten minutes, utilizing the time module and the username and authorization standing. You’ll have the ability to retrieve the claims when making an attempt to confirm the JWT.
The ultimate a part of producing a JWT is to signal the string utilizing your secret key. You may signal your token string utilizing the SignedString technique of the token. The SignedString technique takes the key key and returns a signed token string.
tokenString, err := token.SignedString(sampleSecretKey)
if err != nil {
return "", err
}
return tokenString, nil
In circumstances the place there are errors signing the token, you may return an empty string and the error.
In contrast to cookies, you don’t must retailer JWT; all you want is your signing key to confirm tokens.
Verifying JWT tokens
The traditional technique of verifying JWTs makes use of middleware (handler capabilities that soak up different handler capabilities for operations). Right here’s use middleware to confirm {that a} request is permitted.
func verifyJWT(endpointHandler func(author http.ResponseWriter, request *http.Request)) http.HandlerFunc {
}
The verifyJWT operate is a middleware that takes within the handler operate for the request you wish to confirm. The handler operate makes use of the token parameter from the request header to confirm the request and reply based mostly on the standing.
return http.HandlerFunc(func(author http.ResponseWriter, request *http.Request) {
})
The verifyJWT operate returns the handler operate handed in as a parameter if the request is permitted.
Step one to verifying JWTs is to examine the token within the request’s header.
if request.Header["Token"] != nil {
}
If there’s a token, you may proceed to confirm the token and confirm claims.
You’ll need to parse the token, and you’ll parse the token utilizing the Parse technique of the jwt package deal. The parse technique takes within the token and a JWT decorator operate and returns an interface and an error.
It’s good to use the identical signing technique you used to signal the token if you generated it to confirm the signature utilizing the Methodology technique of the token. On this case, the signing technique was the ECDSA technique.
token, err := jwt.Parse(request.Header["Token"][0], func(token *jwt.Token) (interface{}, error) {
_, okay := token.Methodology.(*jwt.SigningMethodECDSA)
if !okay {
author.WriteHeader(http.StatusUnauthorized)
_, err := author.Write([]byte("You are Unauthorized!"))
if err != nil {
return nil, err
}
}
return "", nil
})
If the signature verification fails (the operate returns !okay), you may return a StatusUnauthorized header to the consumer.
if err != nil {
author.WriteHeader(http.StatusUnauthorized)
_, err2 := author.Write([]byte("You are Unauthorized attributable to error parsing the JWT"))
if err2 != nil {
return
}
}
Within the code above, there’s an error parsing the token. Due to this fact, the consumer is unauthorized, and you’ll write a message and return an unauthorized standing.
You may validate the token utilizing the Legitimate technique of the token.
if token.Legitimate {
endpointHandler(author, request)
} else {
author.WriteHeader(http.StatusUnauthorized)
_, err := author.Write([]byte("You are Unauthorized attributable to invalid token"))
if err != nil {
return
}
}
If the token is legitimate, you may move within the endpoint handler with the author and request parameters of the handler operate for the middleware operate to return the endpoint.
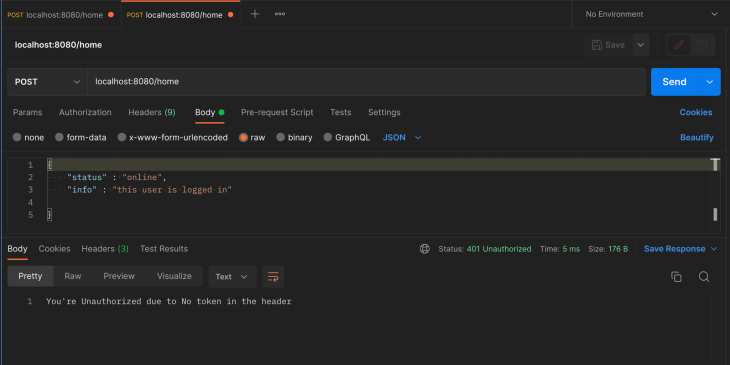
Right here’s the else assertion for a case the place there’s no token within the header of the consumer’s request:
else {
author.WriteHeader(http.StatusUnauthorized)
_, err := author.Write([]byte("You are Unauthorized attributable to No token within the header"))
if err != nil {
return
}
}
Because you’re utilizing middleware, the handler operate in your route declaration would be the verifyJWT middleware with the handler operate for the route because the argument.
http.HandleFunc("/residence", verifyJWT(handlePage))
When you’ve added your verification operate to the route, the endpoint is authenticated.
On the consumer facet, the consumer has to offer an issued token. Right here’s a operate that makes use of the generateJWT operate so as to add tokens in requests.
func authPage(author http.ResponseWriter, ) {
token, err := generateJWT()
if err != nil {
return
}
consumer := &http.Consumer{}
request, _ := http.NewRequest("POST", "<http://localhost:8080/>", nil)
request.Header.Set("Token", token)
_, _ = consumer.Do(request)
}
Within the authPage operate, the token variable holds the token from the generateJWT operate. Utilizing a reference to the Consumer sort of the http package deal, you may create a brand new consumer and make a request to the endpoint. The request variable is the request occasion and — utilizing the Set technique of the header technique of the request occasion — you may set the token within the request header as proven above.
You can even select to set the token as a cookie and retrieve it for verification each time a consumer makes a request to the authenticated endpoint.
While you’re producing a JWT, you may select to embed info within the token. Within the generateJWT operate, you added the username variable to the claims map.
Right here’s how one can extract the claims, utilizing the username claims for instance. You should use middleware or add the performance to your verification operate when verifying the token signature.
func extractClaims(_ http.ResponseWriter, request *http.Request) (string, error) {
if request.Header["Token"] != nil {
tokenString := request.Header["Token"][0]
token, err := jwt.Parse(tokenString, func(token *jwt.Token) (interface{}, error) {
if _, okay := token.Methodology.(*jwt.SigningMethodECDSA); !okay {
return nil, fmt.Errorf("there's an error with the signing technique")
}
return sampleSecretKey, nil
})
if err != nil {
return "Error Parsing Token: ", err
}
}
Within the extractClaims capabilities, the method is identical because the verifyJWT operate; you retrieved the token from the header, parsed the token, and verified the signature.
claims, okay := token.Claims.(jwt.MapClaims)
if okay && token.Legitimate {
username := claims["username"].(string)
return username, nil
}
}
return "unable to extract claims", nil
On validating the token, you may retrieve the claims utilizing the Claims technique and use the claims map to retrieve the info within the JWT, as proven above.
Conclusion
This tutorial taught you use JWT authentication to authenticate your API and net web page endpoints in Go along with JSON Net Tokens by utilizing the golang-jwt package deal. Yow will discover the whole code on this tutorial as a Github Gist.
Bear in mind to make use of atmosphere variables on your secret keys and don’t disguise delicate knowledge in JWTs. There are lots of JWT tutorials on the LogRocket weblog that you may try to get began within the language or framework you’re interested by utilizing!