Though there’s a better consciousness of cybersecurity threats than ever earlier than, it’s changing into more and more tough for IT departments to get their safety budgets accredited. Safety budgets appear to shrink every year and IT execs are always being requested to do extra with much less. Even so, the state of affairs is probably not hopeless. There are some issues that IT execs can do to enhance the probabilities of getting their safety budgets accredited.
Presenting the Drawback in a Compelling Means
If you wish to get your proposed safety funds accredited, you’ll need to current safety issues in a compelling approach. Whereas those that are in command of the group’s funds are probably conscious of the necessity for good safety, they’ve most likely additionally seen sufficient examples of “a safety answer in the hunt for an issue” to make them skeptical of safety spending requests. If you wish to persuade those that management the cash, then you’ll need to persuade them of three issues:
- You are attempting to guard towards an actual subject that presents a reputable risk to the group’s wellbeing.
- Your proposed answer will probably be efficient and that it is not only a “new toy for the IT division to play with”
- Your funds request is each lifelike and justified.
Use Information to Your Benefit
Among the best methods to persuade those that are in cost that there’s a credible cyber risk towards the group is to offer them with quantifiable metrics. Do not resort to gathering statistics from the Web. Your group’s monetary workers might be good sufficient to know that almost all of these statistics are manufactured by safety corporations who’re making an attempt to promote a services or products. As a substitute, collect your personal metrics from inside your group through the use of instruments which can be freely obtainable for obtain.
Specops for instance, gives a free Password Auditor that may generate reviews demonstrating the effectiveness of your group’s password coverage and current password safety vulnerabilities. This free software may also show you how to to determine different vulnerabilities, similar to accounts which can be utilizing passwords which can be identified to have been leaked or passwords that don’t adhere to compliance requirements or trade greatest practices.
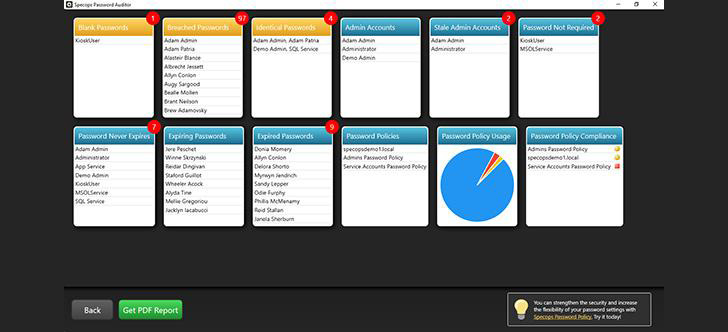 |
| Instance of Specops Password Auditor ends in an Lively Listing atmosphere |
In fact, that is simply one of many many free safety instruments which can be obtainable for obtain. In any case, you will need to use metrics from inside your personal group to exhibit the truth that the safety drawback that you’re making an attempt to resolve is actual.
Spotlight What a Answer Would Do
When you exhibit the issue to those that are in command of the group’s funds, don’t make the error of leaving them guessing as to how you’re planning on fixing the issue. Be ready to obviously clarify what instruments you’re planning on utilizing, and the way these instruments will remedy the issue that you’ve got demonstrated.
It is a good suggestion to make use of visuals to exhibit the practicality of your proposed answer. Make sure you clarify how the issue is solved in non-technical language and improve your argument with examples which can be particular to your group.
Estimated Time of Implementation and Seeing Outcomes
We’ve got most likely all heard horror tales of IT initiatives which have gone off the rails. Organizations generally spend hundreds of thousands of {dollars} and make investments years of planning into IT initiatives that by no means finally materialize. That being the case, you will need to set everybody’s thoughts relaxed by displaying them precisely how lengthy it would take to get your proposed answer up and working after which how a lot extra time will probably be wanted in an effort to obtain the specified consequence.
When you find yourself making these projections, watch out to be lifelike and to not make guarantees based mostly on a very bold implementation schedule. You also needs to be ready to elucidate the way you arrived at your projection. Remember upcoming initiatives, company-wide targets, and monetary yr beliefs when factoring in timing.
Display the Estimated Financial savings
Though safety is after all a priority for many organizations, those that are in command of a corporation’s funds usually wish to see some form of return on funding. As such, you will need to think about how your proposed answer may save the corporate cash. Just a few concepts may embody:
- Saving the IT division time, thereby lowering the variety of extra time hours labored
- Avoiding a regulatory penalty that might value the group some huge cash
- Bringing down insurance coverage premiums as a result of information is being higher protected
In fact, these are simply concepts. Each state of affairs is totally different, and you’ll need to think about how your safety undertaking can produce a return on funding given your personal distinctive circumstances. It is very important embody a cost-saving aspect for readability sake, even whether it is citing the common value of an information breach in your trade.
Present You have Achieved Your Homework with a Pricing Comparability
As you pitch your proposed answer, stakeholders are virtually sure to ask whether or not there is perhaps a inexpensive product that will accomplish your targets. As such, it is essential to spend a while researching the options provided by competing distributors. Right here are some things that you have to be ready to exhibit:
- The whole value for implementing every potential answer (this will likely embody licensing, labor, assist, and {hardware} prices)
- Why you’re proposing a selected answer even when it isn’t the least costly
- In case your answer is the least costly, then be ready to elucidate what you is perhaps giving up through the use of the most affordable vendor.
- What every vendor gives relative to the others
A Few Fast Suggestions
As you make your budgetary pitch, remember the fact that these to whom you’re presenting probably have a restricted understanding of IT ideas. Keep away from utilizing pointless technical jargon and be ready to obviously clarify key ideas, however with out sounding condescending within the course of.
It is also good to anticipate any questions that could be requested of you and have solutions to these questions able to go. That is very true if there’s a specific query that makes you a bit of bit uncomfortable.
Current your data clearly, confidently, and in a concise method (I.e., make it fast!) so you may make your case with out losing time.


