Hiya! Pentesters, this text is a couple of brute-forcing software Hydra. Hydra is without doubt one of the favorite instruments of safety researchers and consultants. Being a wonderful software to carry out brute power assaults, it gives varied different choices which may make your assault extra intense and simpler to achieve unauthorised entry to the system remotely. On this article, I’ve mentioned every choice accessible in hydra to make brute power assaults in varied situations.
Desk of Contents
- Introduction to Hydra
- To guess password for a particular username
- Brute forcing Username and Password
- Verbose and Debug Mode
- NULL/Similar as Login or Reverse login Try
- Saving output in disk
- To Resume Brute Drive Assault
- Password producing utilizing varied set of characters
- To assault on a particular port moderately than the default
- Attacking A number of Hosts
- Utilizing Combo Entries
- Concurrent testing on A number of Logins
- HTTP Login Kind Brute Drive
- Service module Utilization data
- Attacking on secured service connection
- Proxy Help
Introduction to Hydra
Hydra – a really quick community logon cracker which helps many various providers. It’s a parallelized login cracker which helps quite a few protocols to assault. New modules are straightforward so as to add, apart from that, it’s versatile and really quick. This software provides researchers and safety consultants the likelihood to indicate how straightforward it could be to achieve unauthorized entry from a distant to a system.
At present this software helps: adam6500, afp, asterisk, cisco, cisco-enable, cvs, firebird, ftp, ftps, http[s]-put up, http[s]-put up-form, http-proxy, http-proxy-urlenum, icq, imap[s], irc, ldap2[s], ldap3[-digestmd5][s], mssql mysql(v4), mysql5, ncp, nntp, oracle, oracle-listener, oracle-sid, pcanywhere, pcnfs, pop3[s], postgres, rdp, radmin2, redis, rexec, rlogin, rpcap, rsh, rtsp, s7-300, sapr3, sip, smb, smtp[s], smtp-enum, snmp, socks5, ssh, sshkey, svn, teamspeak, telnet[s], vmauthd, vnc, xmpp
For many protocols, SSL is supported (e.g., https-get, ftp-SSL, and so on.). If not, all mandatory libraries are discovered throughout compile time, your accessible providers will likely be much less. Sort “hydra” to see what is out there.

To guess Password for particular username
When you’ve got an accurate username however need to login with out understanding the password, so you need to use a listing of passwords and brute power on passwords on the host for ftp service.
hydra -l ignite -P cross.txt 192.168.1.141 ftp
Right here -l choice is for username -P for password lists and host ip deal with for ftp service.
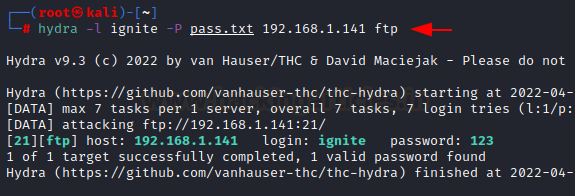
For login ignite password 123 made success.
To guess username for particular password
You could have a legitimate password however no concept what username to make use of. Assume you could have a password for particular ftp login. You’ll be able to brute power the sphere with appropriate username wordlists to seek out the right. You need to use the -L choice to specify person wordlists and the -p choice to specify a particular password.
hydra -L customers.txt -p 123 192.168.1.141 ftp

Right here, our wordlist is customers.txt for which -L choice is used, and password is 123 and for that -p choice is used over ftp.
Brute forcing Username and Password
Now when you don’t have both of username or password, for that you need to use a brute power assault on each the parameters username and password with a wordlist of each and you need to use -P and -U parameters for that.
hydra -L customers.txt -P cross.txt 192.168.1.141 ftp

Customers.txt is wordlist for username and cross.txt is wordlist for password and the assault has displayed legitimate credentials ignite and 123 for the host.
Verbose and Debug Mode
-V choice is used for verbose mode, the place it can present the login+cross mixture for every try. Right here, I’ve two wordlists customers.txt and cross.txt so the brute power assault was making mixtures of every login+password and verbose mode confirmed all of the makes an attempt.

hydra -L customers.txt -P cross.txt 192.168.1.141 ftp -V
Right here the customers.txt has 5 usernames and cross.txt has 7 passwords so the variety of makes an attempt was 5*7= 35 as proven within the screenshot.
Now’s the -d choice used to allow debug mode. It reveals the entire element of the assault with wait time, conwait, socket, PID, RECV
hydra -l ignite -P cross.txt 192.168.1.141 ftp -d

-d choice enabled debug mode which, as proven displayed full element of the assault.

NULL/Similar as Login or Reverse login Try
Hydra has an choice -e which is able to examine 3 extra passwords whereas brute-forcing. [n] for null, [s] for identical i.e., as identical because the username and [r] for reverse i.e., the reverse of username. As proven within the screenshot, whereas brute-forcing the password area, it can first examine with the null choice then the identical choice and after that reverse. After which the checklist which I’ve supplied.
hydra -L customers.txt -P cross.txt 192.168.1.141 ftp -V -e nsr
I’ve enabled verbose mode additionally in order that we will get detailed details about the makes an attempt made whereas brute-forcing.

Saving output in Disk
This software provides you an choice to save lots of the consequence into the disk. Principally for file upkeep, higher readability and future preferences we will save the output of the brute power assault right into a file by utilizing the -o parameter.
hydra -L customers.txt -P cross.txt 192.168.1.141 ftp -o consequence.txt
I attempted to make use of this feature and bought success utilizing the above command the place the output is saved within the consequence.txt file.

hydra -L customers.txt -P cross.txt 192.168.1.141 ftp -o consequence:json
I’ve used this feature to retailer end in json file format additionally, this kind is a singular factor supplied by hydra.

To Resume Brute Drive Assault
It might occur typically, that assault will get halted/paused unintentionally as a consequence of some surprising behaviour by hydra. So, hydra has solved this downside by together with the -R choice with the intention to resume the assault from that place moderately than ranging from the start.
hydra -L customers.txt -P cross.txt 192.168.1.141 ftp hydra -R
First, I began the assault utilizing the primary command, then halted the assault by urgent CTRL + C after which by utilizing the second command I resumed the assault.

Password producing utilizing varied set of characters
To generate passwords utilizing varied set of characters, you need to use -x choice. It’s used as -x min:max:charset the place,
Min: specifies minimal variety of characters in a password.
Max: specifies the utmost variety of characters in password.
Charset: charset can include 1 for numbers, a for lowercase and A for uppercase characters. Some other character which is added is put to the checklist.
Let’s take into account as instance: 1:2:a1%.
The generated passwords will likely be of size 1 to 2 and include lowercase letters, numbers and/or p.c indicators and dots.
hydra -l ignite -x 1:3:1 ftp://192.168.1.141
So, right here minimal size of password is 1 and the max size is 3 which is able to include numbers and for password 123 it confirmed success.

To make you perceive higher I’ve used -V mode and it has displayed leads to element.

To assault a particular port moderately than default
Community admins typically change the default port variety of some providers for safety causes. Within the earlier instructions hydra was making brute power assault on ftp service by simply mentioning the service title moderately than port, however as talked about earlier default port will get modified right now hydra will assist you to with the -s choice. If the service is on a special default port, outline it utilizing the -s choice.
nmap -sV 192.168.1.141 hydra -L customers.txt -P cross.txt 192.168.1.141 ssh -s 2222
So to carry out, first I attempted working a nmap scan on the host. And the screenshot reveals all open ports the place ssh is on the 2222 port. So put up that I attempted executing the hydra command with -s parameter and port quantity.

I’ve brute-forced on ssh service mentioning the port quantity, 2222.
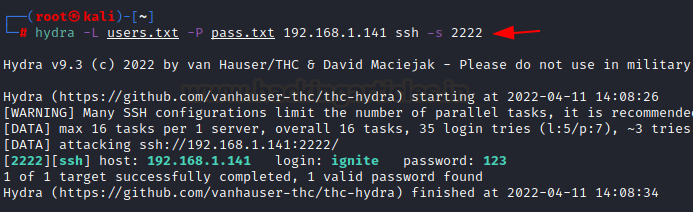
Right here it discovered legitimate entries with person ignite and password 123.
Attacking A number of Hosts
As earlier I carried out a brute power assault utilizing password file cross.txt and username file customers.txt on a single host i.e., 191.168.1.141. But when there are a number of hosts, for that you need to use -M with the assistance of which brute power is going on at a number of hosts.
hydra -L customers.txt -P cross.txt -M hosts.txt ftp
First, I’ve created a brand new file hosts.txt which accommodates all of the hosts. Then the result’s exhibiting 2 legitimate hosts, username and password with success.

Now within the above command, I’ve used the -M choice for a number of hosts so, it is rather time-consuming to show all of the makes an attempt happening whereas the assault, for that medusa, has supplied -F choice such that the assault will exit after the primary discovered login/password pair for any host.
hydra -L customers.txt -P cross.txt -M hosts.txt ftp -F

Utilizing Combo Entries
This software provides you a singular parameter -C for utilizing combo entries. First, you’ll want to create a file which has information within the colon-separated “login:cross” format, after which you need to use -C choice mentioning the file title and carry out a brute power assault as a substitute of utilizing -L/-P choices individually. On this approach, the assault will be quicker and provides you desired end in lesser time.
cat userpass.txt hydra -C userpass.txt 192.168.1.141 ftp
So, I’ve created a userpass.txt file utilizing cat command and entered particulars in “login:cross” format. Then I used -C choice within the hydra command to begin the assault.

Concurrent Testing on A number of Logins
If you wish to take a look at a number of logins concurrently, for that you need to use -t choice by mentioning the quantity and therefore hydra will brute power concurrently.
hydra -L customers.txt -P cross.txt 192.168.1.141 ftp -t 3 -V
As proven within the screenshot, three makes an attempt are made concurrently, three passwords are concurrently checking with person ignite at host 192.168.1.141, as you possibly can observe youngster adjustments 0, 1,2 meaning it’s concurrently making three makes an attempt and printed 3 of them concurrently.

HTTP Login Kind Brute Drive
The hydra type can be utilized to hold out a brute power assault on easy web-based login varieties that requires username and password variables both by GET or POST request. For testing I used dvwa (rattling weak net utility) which has login web page. This web page makes use of POST technique as I’m sending some information.

hydra -l admin -P cross.txt 192.168.1.150 http-post-form “/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed”
Right here I’ve given the username admin and supplied file for passwords and used http-post-form module to carry out brute power assault on 192.168.1.150 host.

So, for password: password it gave success and bypassed the login web page. Now I had carried out brute power on username and password area talked about having safety stage as “low”. And by utilizing cookie editor plugin I discovered the cookie PHPSESSID and used its worth within the command.
hydra 192.168.1.150 -l admin -P ‘cross.txt’ http-get-form “/dvwa/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:F=Username and/or password incorrect.:H=Cookie:PHPSESSID=13f2650bddf7a9ef68858ceea03c5d; safety=low”

I had seen web page supply and from that I discovered that web page makes use of GET technique, and so http-GET-form module as talked about in above command.

As within the screenshot, the command is efficiently executed, and I bought the right username and password.

Service module Utilization data
As mentioned earlier within the introduction all of the supported providers by hydra, if you wish to examine as soon as simply sort hydra -h and you’re going to get checklist of providers supported by hydra. So, to get the detailed details about the utilization hydra gives -U choice.
hydra http-get-form -U

Right here http-get-form is without doubt one of the providers supported by hydra and -U choice helped to get detailed data.
Attacking on secured service connection
Whereas performing an assault on ftp connection, you simply point out the service title together with acceptable choices, but when the host has ftp port open and ftp is secured, so when you use
hydra -l ignite -P cross.txt ftp://192.168.1.141
This command won’t execute correctly and therefore 0 legitimate passwords had been discovered. So with a view to carry out an assault on a secured ftp connection, then run this command.
hydra -l ignite -P cross.txt ftps://192.168.1.141

And this command labored effectively and confirmed 1 legitimate password discovered.
That is one technique to assault secured ftp, hydra gives yet another technique to assault secured service.
hydra -l ignite -P cross.txt 192.168.1.141 ftp hydra -l ignite -P cross.txt 192.168.1.141 ftps

The primary didn’t work because the host 192.168.1.141 has secured ftp, however the second, labored and confirmed us a legitimate password discovered. On this approach, you possibly can carry out a brute power assaults on hosts which have secured providers open.
Proxy Help
Now let’s focus on how hydra assaults on hosts having proxy enabled. I first tried to identical command with -l -p parameters on host 192.168.1.141 on ftp service and located that no password was discovered. Therefore, I began an nmap scan for the host and located checklist of providers and ports open. So, at port 1080 a proxy “socks5” was set with none authentication.

Unauthenticated Proxy
Hydra gives two alternative ways for proxy assist. I’ve tried each the methods. Use screenshots for higher understanding. Let’s focus on the primary approach
Surroundings Variable
To allow proxy I used this command
export HYDRA_PROXY=socks5://192.168.1.141:1080

After which used the next command and bought 1 legitimate password
hydra -l ignite -P cross.txt 192.168.1.141 ftp
Proxychains
I’ve opened the /and so on/proxychains4.conf and added the proxy particulars with host and port. After which with the assistance of proxychains brute power is carried out
cat /and so on/proxychains4.conf
proxychains hydra -l ignite -P cross.txt 192.168.1.141 ftp

Authenticated Proxy
I bought the specified password 123 for the host. Within the above assault, there was not any authentication enabled. Now I attempted on a proxy that has authentication enabled.
Proxychains
I attempted to brute power the goal utilizing proxychains however it was denied as a result of authentication was enabled on the proxy.
proxychains hydra -l ignite -p cross.txt 192.168.1.141 ftp

So, I added the username and password in /and so on/proxychains4.conf file
cat /and so on/proxychains4.conf
Simply observe the screenshot for higher understanding. Then with the assistance of proxychains, I began attacking utilizing the beneath command
proxychains hydra -l ignite -P cross.txt 192.168.1.141 ftp
Therefore, after execution of this command, a legitimate password was discovered for the host having proxy enabled.

Surroundings Variable
export HYDRA_PROXY=socks5://raj:[email protected]:1080
Right here “raj” is the username, “1234” is password for the proxy and “192.168.1.141” is the host and “1080” is the port on which the proxy is enabled. After that, I used the command
hydra -l ignite -P cross.txt 192.168.1.141 ftp
And for this, it confirmed a legitimate password for the host 192.168.1.141

Notice: For organising the proxy I took reference from https://www.hackingarticles.in/penetration-testing-lab-setup-microsocks/
Writer: Divya Adwani is a researcher and technical author who may be very a lot eager to study and enthusiastic to study moral hacking Contact right here

