Cybersecurity researchers have detailed the workings of a fully-featured malware loader dubbed PureCrypter that is being bought by cyber criminals to ship distant entry trojans (RATs) and data stealers.
“The loader is a .NET executable obfuscated with SmartAssembly and makes use of compression, encryption, and obfuscation to evade antivirus software program merchandise,” Zscaler’s Romain Dumont stated in a brand new report.
A number of the malware households distributed utilizing PureCrypter embrace Agent Tesla, Arkei, AsyncRAT, AZORult, DarkCrystal RAT (DCRat), LokiBot, NanoCore, RedLine Stealer, Remcos, Snake Keylogger, and Warzone RAT.
Bought for a value of $59 by its developer named “PureCoder” for a one-month plan (and $249 for a one-off lifetime buy) since no less than March 2021, PureCrypter is marketed because the “solely crypter out there that makes use of offline and on-line supply approach.”
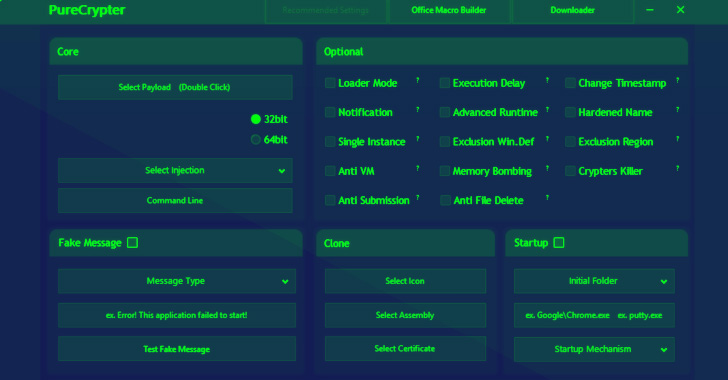
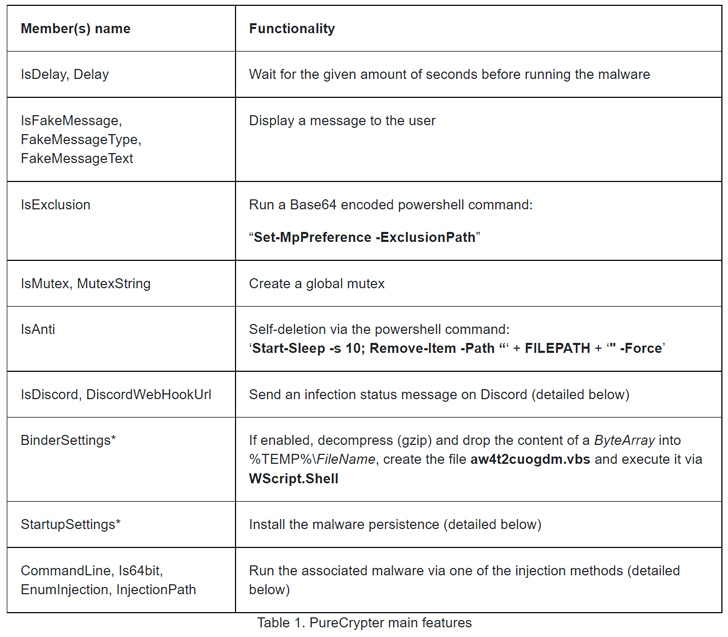
Crypters act because the first layer of protection towards reverse engineering and are sometimes used to pack the malicious payload. PureCrypter additionally options what it says is a sophisticated mechanism to inject the embedded malware into native processes and quite a lot of configurable choices to attain persistence on startup and activate extra choices to fly beneath the radar.
Additionally supplied is a Microsoft Workplace macro builder and a downloader, highlighting the potential preliminary an infection routes that may be employed to propagate the malware.
Curiously, whereas PureCoder makes it some extent to notice that the “software program was created for academic functions solely,” its phrases of service (ToS) forbids consumers from importing the device to malware scanning databases similar to VirusTotal, Jotti, and MetaDefender.
“You aren’t allowed to scan the crypted file, because the crypter itself has a built-in scanner,” the ToS additional states.
In a single pattern analyzed by Zscaler, a disk picture file (.IMG) was discovered to comprise a first-stage downloader that, in flip, retrieves and runs a second-stage module from a distant server, which subsequently injects the ultimate malware payload inside different processes like MSBuild.
PureCryter additionally presents numerous notable options that permits it to take away itself from the compromised machine and report the an infection standing to the creator by way of Discord and Telegram.