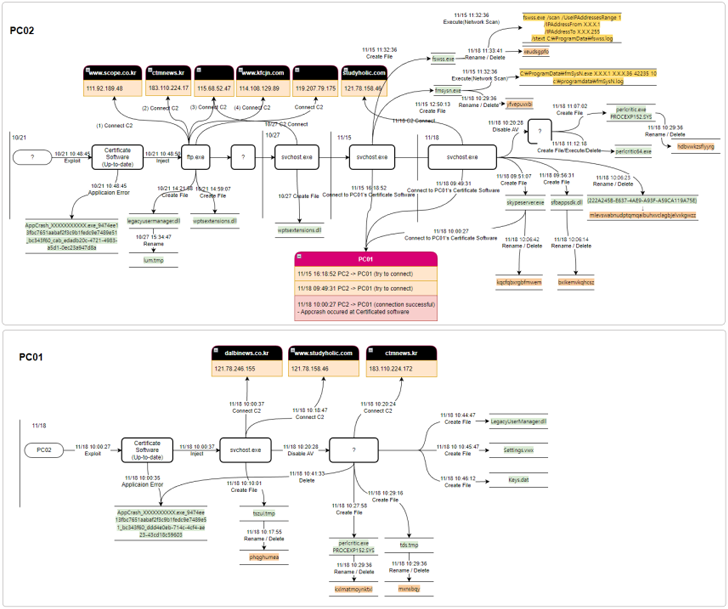
The North Korea-linked Lazarus Group has been noticed weaponizing flaws in an undisclosed software program to breach a monetary enterprise entity in South Korea twice inside a span of a 12 months.
Whereas the primary assault in Could 2022 entailed using a susceptible model of a certificates software program that is extensively utilized by public establishments and universities, the re-infiltration in October 2022 concerned the exploitation of a zero-day in the identical program.
Cybersecurity agency AhnLab Safety Emergency Response Heart (ASEC) mentioned it is refraining from mentioning the software program owing to the truth that “the vulnerability has not been absolutely verified but and a software program patch has not been launched.”
The adversarial collective, after acquiring an preliminary foothold by an unknown technique, abused the zero-day bug to carry out lateral motion, shortly after which the AhnLab V3 anti-malware engine was disabled through a BYOVD assault.
It is value noting right here that the Carry Your Personal Susceptible Driver, aka BYOVD, approach has been repeatedly employed by the Lazarus Group in current months, as documented by each ESET and AhnLab in a collection of reviews late final 12 months.
Amongst different steps to hide its malicious habits embody altering file names earlier than deleting them and modifying timestamps utilizing an anti-forensic approach known as timestomping.
The assault finally paved the best way for a number of backdoor payloads (Keys.dat and Settings.vwx) which are designed to hook up with a distant command-and-control (C2) server and retrieve extra binaries and execute them in a fileless method.
Uncover the Hidden Risks of Third-Social gathering SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to study concerning the varieties of permissions being granted and easy methods to decrease threat.
The event comes per week after ESET shed mild on a brand new implant known as WinorDLL64 that is deployed by the infamous menace actor by way of a malware loader named Wslink.
“The Lazarus group is researching the vulnerabilities of varied different software program and are continuously altering their TTPs by altering the best way they disable safety merchandise and perform anti-forensic methods to intervene or delay detection and evaluation to be able to infiltrate Korean establishments and corporations,” ASEC mentioned.