A suspected Pakistan-aligned superior persistent menace (APT) group often called Clear Tribe has been linked to an ongoing cyber espionage marketing campaign focusing on Indian and Pakistani Android customers with a backdoor referred to as CapraRAT.
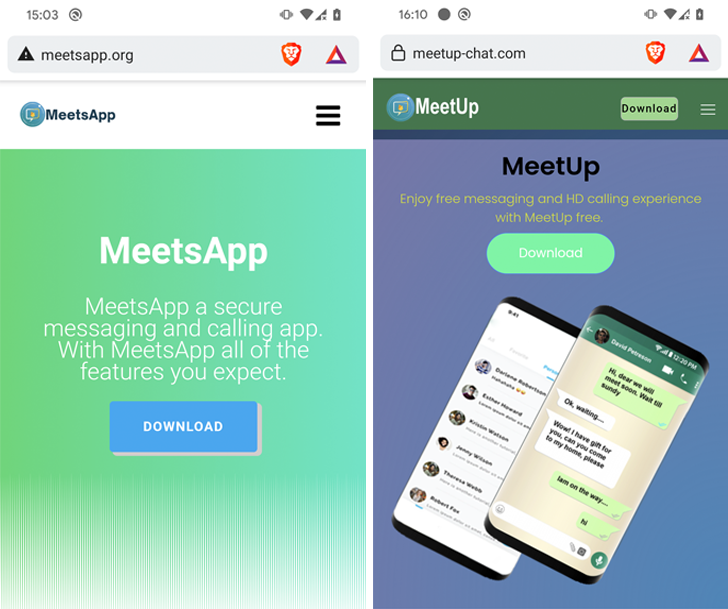
“Clear Tribe distributed the Android CapraRAT backdoor through trojanized safe messaging and calling apps branded as MeetsApp and MeetUp,” ESET stated in a report shared with The Hacker Information.
As many as 150 victims, seemingly with army or political leanings, are estimated to have been focused, with the malware (com.meetup.app) accessible to obtain from faux web sites that masquerade because the official distribution facilities of those apps.
It is being suspected that the targets are lured by a honeytrap romance rip-off whereby the menace actor approaches the victims through one other platform and persuades them to put in the malware-laced apps below the pretext of “safe” messaging and calling.
Nevertheless, the apps, in addition to providing the promised performance, come implanted with CapraRAT, a modified model of the open supply AndroRAT that was first documented by Development Micro in February 2022 and which displays overlaps with a Home windows malware often called CrimsonRAT.
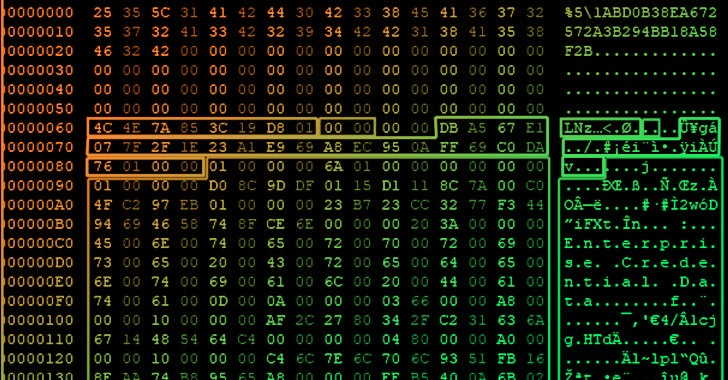
The backdoor is filled with an in depth set of options that permits it to take screenshots and photographs, file telephone calls and surrounding audio, and exfiltrate different delicate info. It may possibly additionally make calls, ship SMS messages, and obtain instructions to obtain information.
That having stated, customers are additionally required to create an account by linking their telephone numbers and finishing an SMS verification step with the intention to entry the app’s functionalities.
Uncover the Newest Malware Evasion Techniques and Prevention Methods
Able to bust the 9 most harmful myths about file-based assaults? Be part of our upcoming webinar and turn out to be a hero within the combat towards affected person zero infections and zero-day safety occasions!
The Slovak cybersecurity firm said the marketing campaign is narrowly focused and that it discovered no proof that signifies the apps had been accessible on the Google Play Retailer.
Clear Tribe, additionally known as APT36, Operation C-Main, and Mythic Leopard, was not too long ago attributed to a different set of assaults focusing on Indian authorities organizations with malicious variations of a two-factor authentication resolution referred to as Kavach.
The findings additionally arrive weeks after cybersecurity agency ThreatMon detailed a spear-phishing marketing campaign by SideCopy actors focusing on Indian authorities entities with an intention to deploy an up to date model of a backdoor often called ReverseRAT.