Six totally different legislation companies have been focused in January and February 2023 as a part of two disparate risk campaigns distributing GootLoader and FakeUpdates (aka SocGholish) malware strains.
GootLoader, lively since late 2020, is a first-stage downloader that is able to delivering a variety of secondary payloads corresponding to Cobalt Strike and ransomware.
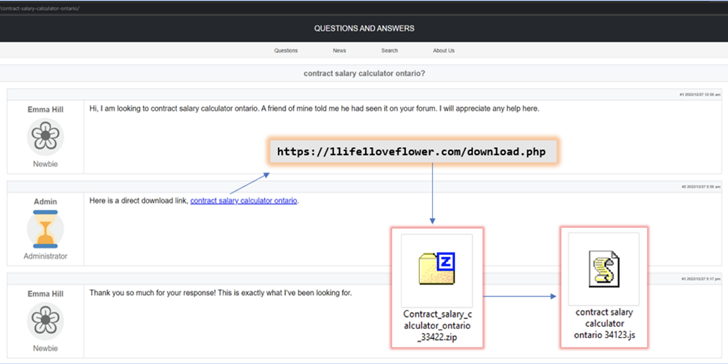
It notably employs SEO (search engine optimisation) poisoning to funnel victims trying to find business-related paperwork towards drive-by obtain websites that drop the JavaScript malware.
Within the marketing campaign detailed by cybersecurity firm eSentire, the risk actors are stated to have compromised legit, however weak, WordPress web sites and added new weblog posts with out the house owners’ data.
“When the pc consumer navigates to one among these malicious net pages and hits the hyperlink to obtain the purported enterprise settlement, they’re unknowingly downloading GootLoader,” eSentire researcher Keegan Keplinger stated in January 2022.
The disclosure from eSentire is the most recent in a wave of assaults which have utilized the Gootkit malware loader to breach targets.
GootLoader is much from the one JavaScript malware focusing on enterprise professionals and legislation agency staff. A separate set of assaults have additionally entailed the usage of SocGholish, which is a downloader able to dropping extra executables.
The an infection chain is additional important for benefiting from an internet site frequented by authorized companies as a watering gap to distribute the malware.
One other standout side of the dual intrusion units within the absence of ransomware deployment, as a substitute favoring hands-on exercise, suggesting that the assaults might have diversified in scope to incorporate espionage operations.
“Previous to 2021, e mail was the first an infection vector utilized by opportunistic risk actors,” Keplinger stated. From 2021 to 2023, browser-based assaults […] have steadily been rising to compete with e mail as the first an infection vector.”
“This has been largely because of GootLoader, SocGholish, SolarMarker, and up to date campaigns leveraging Google Adverts to drift high search outcomes.”