A stealthy Unified Extensible Firmware Interface (UEFI) bootkit referred to as BlackLotus has develop into the primary publicly recognized malware able to bypassing Safe Boot defenses, making it a potent menace within the cyber panorama.
“This bootkit can run even on absolutely up-to-date Home windows 11 techniques with UEFI Safe Boot enabled,” Slovak cybersecurity firm ESET mentioned in a report shared with The Hacker Information.
UEFI bootkits are deployed within the system firmware and permit full management over the working system (OS) boot course of, thereby making it doable to disable OS-level safety mechanisms and deploy arbitrary payloads throughout startup with excessive privileges.
Provided on the market at $5,000 (and $200 per new subsequent model), the highly effective and protracted toolkit is programmed in Meeting and C and is 80 kilobytes in dimension. It additionally options geofencing capabilities to keep away from infecting computer systems in Armenia, Belarus, Kazakhstan, Moldova, Romania, Russia, and Ukraine.
Particulars about BlackLotus first emerged in October 2022, with Kaspersky safety researcher Sergey Lozhkin describing it as a complicated crimeware resolution.
“This represents a little bit of a ‘leap’ ahead, by way of ease of use, scalability, accessibility, and most significantly, the potential for way more affect within the types of persistence, evasion, and/or destruction,” Eclypsium’s Scott Scheferman famous.
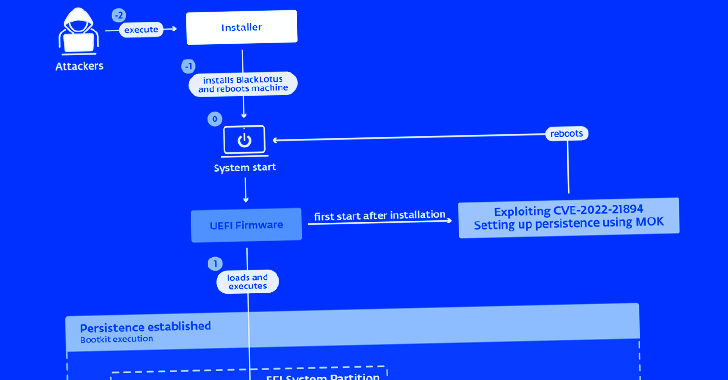
BlackLotus, in a nutshell, exploits a safety flaw tracked as CVE-2022-21894 (aka Baton Drop) to get round UEFI Safe Boot protections and arrange persistence. The vulnerability was addressed by Microsoft as a part of its January 2022 Patch Tuesday replace.
A profitable exploitation of the vulnerability, based on ESET, permits arbitrary code execution throughout early boot phases, allowing a menace actor to hold out malicious actions on a system with UEFI Safe Boot enabled with out having bodily entry to it.
“That is the primary publicly recognized, in-the-wild abuse of this vulnerability,” ESET researcher Martin Smolár mentioned. “Its exploitation continues to be doable because the affected, validly signed binaries have nonetheless not been added to the UEFI revocation record.”
“BlackLotus takes benefit of this, bringing its personal copies of reputable – however susceptible – binaries to the system with a purpose to exploit the vulnerability,” successfully paving the best way for Convey Your Personal Susceptible Driver (BYOVD) assaults.
Moreover being geared up to show off safety mechanisms like BitLocker, Hypervisor-protected Code Integrity (HVCI), and Home windows Defender, it is also engineered to drop a kernel driver and an HTTP downloader that communicates with a command-and-control (C2) server to retrieve further user-mode or kernel-mode malware.
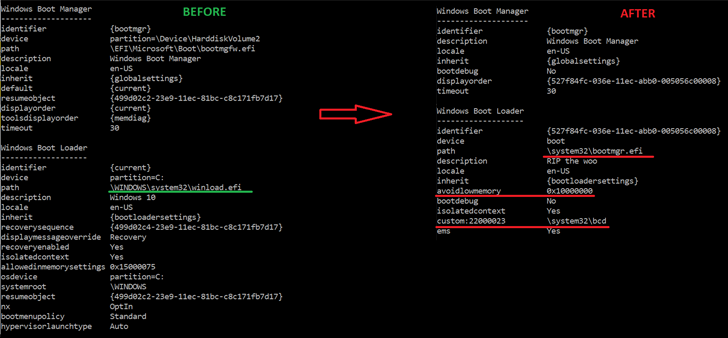
The precise modus operandi used to deploy the bootkit is unknown as but, however it begins with an installer element that is liable for writing the information to the EFI system partition, disabling HVCI and BitLocker, after which rebooting the host.
The restart is adopted by the weaponization of CVE-2022-21894 to attain persistence and set up the bootkit, after which it’s mechanically executed on each system begin to deploy the kernel driver.
Whereas the motive force is tasked with launching the user-mode HTTP downloader and operating next-stage kernel-mode payloads, the latter is able to executing instructions acquired from the C2 server over HTTPS.
This consists of downloading and executing a kernel driver, DLL, or an everyday executable; fetching bootkit updates, and even uninstalling the bootkit from the contaminated system.
“Many vital vulnerabilities affecting safety of UEFI techniques have been found in the previous couple of years,” Smolár mentioned. “Sadly, due the complexity of the entire UEFI ecosystem and associated supply-chain issues, many of those vulnerabilities have left many techniques susceptible even a very long time after the vulnerabilities have been fastened – or a minimum of after we have been advised they have been fastened.”
“It was only a matter of time earlier than somebody would benefit from these failures and create a UEFI bootkit able to working on techniques with UEFI Safe Boot enabled.”