When Russia invaded Ukraine on Feb. 24, 2022, a lot dialogue ensued about how the conflict could be each cyber and kinetic. A yr later, the consensus appears to be that whereas there was plenty of cyberattack exercise, it wasn’t as harmful as many had feared. That was partly attributable to numerous governments and safety corporations serving to to establish and block assaults.
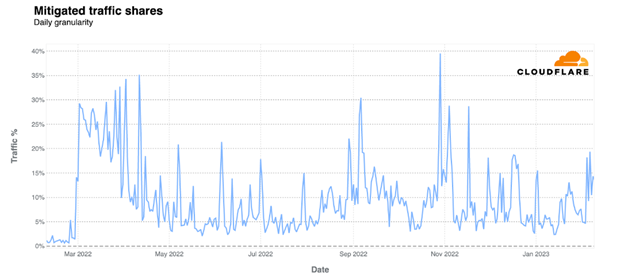
Between February 2022 and February 2023, a median of 10% of all on-line visitors to Ukraine was mitigations of potential assaults, Cloudflare mentioned in its evaluation of the Russian invasion’s impression on theUkrainian Web. Cloudflare protected Ukrainian Internet purposes by filtering and monitoring HTTP visitors to dam malicious assaults, together with distributed denial-of-service (DDoS) assaults.
On Oct. 29, DDoS assault visitors constituted 39% of complete visitors to Cloudflare’s Ukrainian clients.
The corporate shared a graph displaying the each day share of software layer visitors to Ukraine that Cloudflare mitigated as potential assaults utilizing its Internet software firewall (WAF). In early March, 30% of all visitors was mitigated. After a reasonably quiet summer season, assault exercise ticked again up in early September, throughout the Ukrainian counteroffensive in east and south Ukraine.
Extra particularly, 14% of complete visitors from Ukraine was mitigated as potential assaults, whereas 10% of complete visitors to Ukraine was mitigated as potential assaults prior to now 12 months.
Mitigated application-layer threats blocked by Cloudflare’s WAF have been 105% larger on Monday, Feb. 28, 2022 — 4 days after the invasion — in contrast with the Monday earlier than, Feb. 21, 2022. By March 8, that determine was 1,300%.
What Got here Out of ‘Shields Up’
In anticipation of Russian cyberattacks in opposition to Ukrainian targets and in opposition to organizations in nations allied with Ukraine, the US Cybersecurity and Infrastructure Safety Company (CISA) urged organizations to share info that would assist mitigate threats. “Each group — massive and small — have to be ready to reply to disruptive cyber incidents,” CISA mentioned.
Whereas sharing menace intelligence indubitably helped, the character of the assaults have been additionally much less subtle or harmful than feared.
Cisco Talos researchers have been monitoring vital infrastructure clients to establish threats and remediate assaults. Whereas there have been plenty of issues about harmful malware, what Talos is seeing — and blocking — plenty of is credentials harvesting, says Nick Biasini, Cisco Talos’ head of outreach. Attackers are usually not resorting to extremely subtle ways however relatively are using mundane and recognizable strategies to attempt to achieve entry to networks and accounts, he says.
Influence on Essential Infrastructure
Cloudflare’s evaluation of Ukraine’s Web visitors exhibits peaks and drops in utilization corresponding with navy exercise. For instance, the town of Chernihiv had a major drop in visitors the primary week of the conflict and residual visitors by mid-March, with visitors selecting up after the Russian retreat in early April, Cloudflare famous. Within the fall, Russian navy models began focusing on Ukrainian vital infrastructure, inflicting widespread energy outages and Web blackouts. A few of these strikes precipitated as a lot as a 50% lower in Web visitors, based on Cloudflare’s evaluation. The disruptions typically lasted solely a day or two, “additional emphasizing the continuing impression of the battle on Ukraine’s infrastructure,” Cloudflare famous.
“All through the remainder of the yr and into 2023, Ukraine has continued to face intermittent Web disruptions,” Cloudflare additionally wrote.
Ripple Results Across the World
Safety leaders in East Asia are fastidiously watching how the conflict between Russia and Ukraine unfolds, as plenty of the geopolitical tensions and rhetoric are much like the long-simmering state of affairs between China and Taiwan. Organizations are “questioning what sort of disruptive assaults to anticipate” and the way the conflict in Ukraine may have an effect on the Taiwan state of affairs, says Mihoko Matsubara, chief cybersecurity strategist at NTT. There has already been some exercise, though it has been of the “cyber nuisance” selection, relatively than destruction, Matsubara says. East Asian corporations are already seeing DDoS assaults, defacements, and disinformation campaigns, she says.
Matsubara was cautious not to downplay the seriousness of the assaults, as they’re nonetheless disruptive to organizations. NTT has additionally seen some wiper assaults used to disrupt humanitarian help efforts, which can be a harbinger of actions to return.
Dangerous Actors Get Political
Cybercriminals have been expressing their very own opinions — and political allegiances — in regards to the conflict. For instance, Coalition’s newest “Cyber Menace Index” report dug into assaults in opposition to databases uncovered to the Web. Coalition noticed a complete 264,408 IP addresses operating MongoDB cases in 2022, and 68,423 of them — or 26% — have been compromised. Coalition discovered a handful of compromised MongoDB servers the place the attackers renamed the databases to SLAVA_UKRAINI, or “Glory to Ukraine!”
“Menace actor exercise is usually formed by fluctuations in financial circumstances,” famous the workforce from Kroll’s Cyber Threat observe within the newest “Menace Panorama” report. “Because of the continued market volatility throughout the globe and the continuing conflict on Ukraine, it’s possible that the unstable circumstances wherein attackers thrive will persist in 2023.”