The proportion of open supply codebases with vulnerabilities has continued to stay degree over the previous two years, however the variety of functions with high-risk vulnerabilities has dropped to its lowest degree in 4 years.
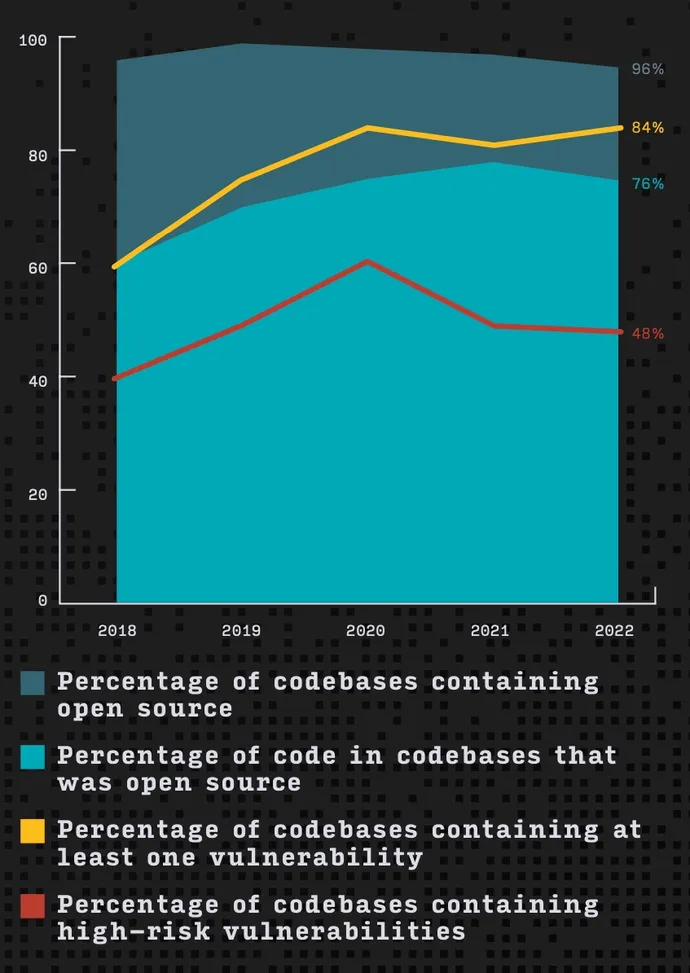
That is based on the “2023 Open Supply Safety and Danger Evaluation” (OSSRA) report, printed by Synopsys on Feb. 22. The annual research, based mostly on audits of greater than 1,700 functions, discovered that just about each software program program (96%) included some form of open supply software program element, with the typical codebase consisting of 76% open supply code. Whereas the variety of codebases with no less than one vulnerability remained principally steady over the previous three years at barely greater than 80% — 84% in 2022 — the variety of functions with high-risk vulnerabilities has dropped to about half (48%) of all functions examined, from a peak of about 60% in 2020.
General, the info exhibits some vivid spots within the battle towards weak dependencies, of which the typical utility has 595, however there isn’t any broad pattern towards larger utility safety, says Mike McGuire, a senior software program options supervisor at Synopsys Software program Integrity Group.
“Organizations are struggling to maintain up with the dimensions of open supply utilization,” he says. “Should you take these nearly 600 parts per utility on common, and multiply that by the variety of vulnerabilities which can be disclosed on an annual foundation, then you’ll be able to actually, actually begin to drown within the work.”
Open supply parts, and the dependencies on which widespread utility frameworks rely, proceed to pose safety issues for software program makers and utility builders. The ubiquity of some parts — resembling Log4j within the Java ecosystem — continues to trigger safety points for a lot of functions based mostly on open supply frameworks.
Outdated Dependencies Are Frequent
Purposes that embody quite a lot of parts — and by extension, these parts’ dependencies — can have deep dependency timber that make it laborious to search out each vulnerability. Almost all functions (91%), for instance, included no less than one open supply element that has no growth prior to now two years, a possible signal that the mission is not being maintained and, due to this fact, represents a safety threat.
Almost one in eight functions additionally had greater than 10 completely different variations of a particular codebase, with every doubtless imported from a special element and that element’s dependencies.
Failing to get rid of these older codebases represents a threat, Synopsys acknowledged within the OSSRA report.
“Open supply was in almost every little thing we examined this 12 months; it made up nearly all of the codebases throughout industries, and it contained troublingly excessive numbers of recognized vulnerabilities that organizations had did not patch, leaving them weak to use,” the report acknowledged. “It’s essential to know that whereas open supply itself doesn’t pose any inherent degree of threat, failing to handle it does.”
Whether or not extra dependencies means extra vulnerabilities remains to be a relationship underneath investigation. JavaScript frameworks, for instance, are inclined to have the best variety of dependencies, however JavaScript functions are usually much less weak than Java and .NET functions, based on a report launched by software-security agency Veracode in January.
Do not Fall Behind With Open Supply Dependencies
The influence of open supply code on safety varies by business, based on the OSSRA report. Some industries have elevated their open supply utilization, whereas others have consolidated their portfolio. Relying on their degree of maturity, the influence on safety will be completely different.
Schooling know-how corporations, for instance, have adopted open supply parts to drive new options and functions required by faculties in the course of the push for on-line instructing in the course of the pandemic. In that business, open supply software program accounted for greater than 80% of codebases in 2022, up from a couple of third in 2018. Different sectors additionally noticed dramatic, if not so stark, will increase in utilization. The aerospace, aviation, automotive, transportation, and logistics sector, for instance, additionally almost doubled its utilization of open supply parts over 5 years.
The numerous improve in adoption has led to many corporations shedding visibility into what’s making up their software program and what wants patching, McGuire says.
“Extra organizations are utilizing extra open supply parts, however they simply do not have the applications in place to trace these [patches] down,” he says. “When you get underwater with these updates — it is identical to every other technical debt or debt usually, proper? — it is actually powerful to claw your method again.”
Different industries have diminished their utilization of open supply software program, doubtless by consolidating on fewer tasks as dependencies, based on the report. Each the Web and software program infrastructure sector, and the telecommunications and wi-fi sector, have diminished the contribution of open supply software program to their codebases to underneath 60%. Each industries additionally noticed fewer high-severity vulnerabilities.


