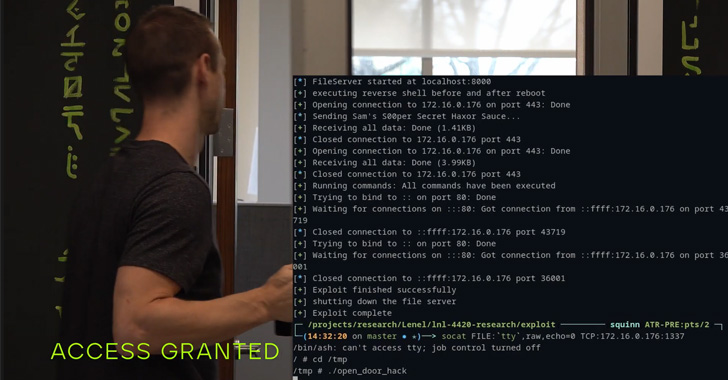
As many as eight zero-day vulnerabilities have been disclosed in Service’s LenelS2 HID Mercury entry management system that is used broadly in healthcare, schooling, transportation, and authorities amenities.
“The vulnerabilities uncovered allowed us to reveal the power to remotely unlock and lock doorways, subvert alarms and undermine logging and notification programs,” Trellix safety researchers Steve Povolny and Sam Quinn mentioned in a report shared with The Hacker Information.
The problems, in a nutshell, may very well be weaponized by a malicious actor to realize full system management, together with the power to control door locks. One of many bugs (CVE-2022-31481) consists of an unauthenticated distant execution flaw that is rated 10 out of 10 for severity on the CVSS scoring system.
Different shortcomings may result in command injection (CVE-2022-31479, CVE-2022-31486), denial-of-service (CVE-2022-31480, CVE-2022-31482), person modification (CVE-2022-31484), and knowledge spoofing (CVE-2022-31485) in addition to obtain arbitrary file write (CVE-2022-31483).
LenelS2 is employed in environments to grant bodily entry to privileged amenities and combine with extra complicated constructing automation deployments. The next HID Mercury entry panels bought by LenelS2 are impacted –
- LNL-X2210
- LNL-X2220
- LNL-X3300
- LNL-X4420
- LNL-4420
- S2-LP-1501
- S2-LP-1502
- S2-LP-2500, and
- S2-LP-4502
Trellix famous that by chaining two of the aforementioned weaknesses, it was capable of acquire root-level privileges on the gadget remotely and unlock and management the doorways, successfully subverting the system monitoring protections.
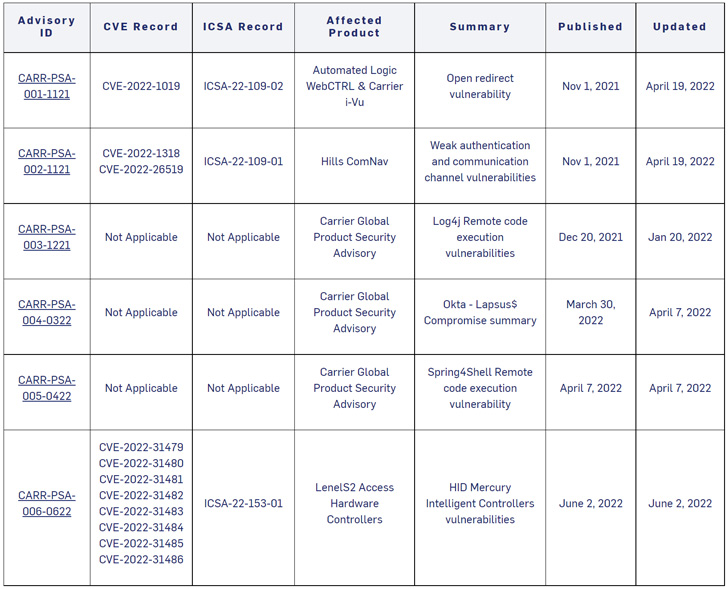
Coinciding with the general public disclosure is an industrial management programs (ICS) advisory from the U.S. Cybersecurity and Infrastructure Safety Company (CISA), urging customers to replace the entry panels to the newest firmware model (CARR-PSA-006-0622).
“Profitable exploitation of those vulnerabilities may permit an attacker entry to the gadget, permitting monitoring of all communications despatched to and from the gadget, modification of onboard relays, altering of configuration recordsdata, gadget instability, and a denial-of-service situation,” the company mentioned in an alert.