After the U.S. Cybersecurity and Infrastructure Safety Company (CISA) launched a decryptor for affected victims to get better from ESXiArgs ransomware assaults, the menace actors have bounced again with an up to date model that encrypts extra information.
The emergence of the brand new variant was reported by a system administrator on a web based discussion board, the place one other participant acknowledged that recordsdata bigger than 128MB could have 50% of their information encrypted, making the restoration course of more difficult.
One other notable change is the removing of the Bitcoin deal with from the ransom word, with the attackers now urging victims to contact them on Tox to acquire the pockets info.
The menace actors “realized that researchers have been monitoring their funds, and so they might have even identified earlier than they launched the ransomware that the encryption course of within the authentic variant was comparatively simple to avoid,” Censys mentioned in a write-up.
“In different phrases: they’re watching.”
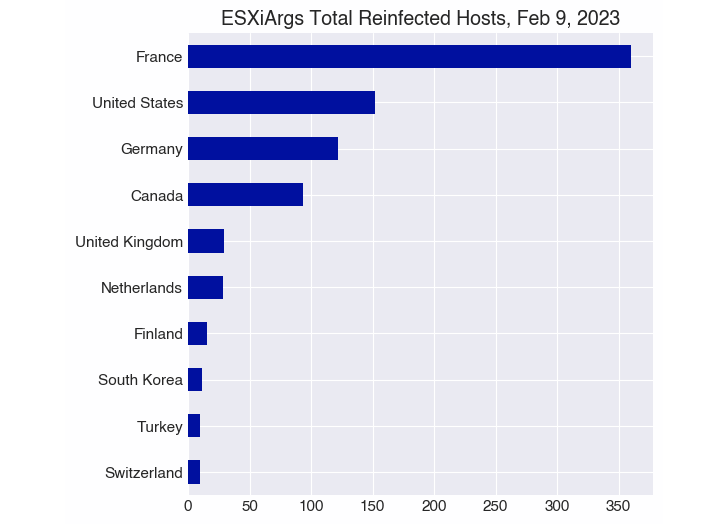
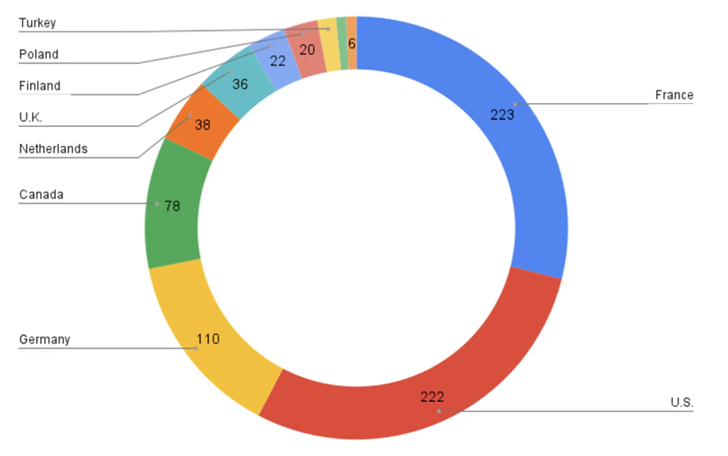
Statistics shared by the crowdsourced platform Ransomwhere reveal that as many as 1,252 servers have been contaminated by the brand new model of ESXiArgs as of February 9, 2023, of which 1,168 are reinfections.
For the reason that begin of the ransomware outbreak in early February, over 3,800 distinctive hosts have been compromised. A majority of the infections are situated in France, the U.S., Germany, Canada, the U.Okay., the Netherlands, Finland, Turkey, Poland, and Taiwan.
ESXiArgs, like Cheerscrypt and PrideLocker, is predicated on the Babuk locker, which had its supply code leaked in September 2021. However an important facet that differentiates it from different ransomware households is the absence of a knowledge leak web site, indicating that it isn’t operating on a ransomware-as-a-service (RaaS) mannequin.
“Ransoms are set at simply over two bitcoins (US $47,000), and victims are given three days to pay,” cybersecurity firm Intel471 mentioned.
Whereas it was initially suspected that the intrusions concerned the abuse of a two-year-old, now-patched OpenSLP bug in VMware ESXi (CVE-2021-21974), compromises have been reported in units which have the community discovery protocol disabled.
VMware has since mentioned that it has discovered no proof to counsel {that a} zero-day vulnerability in its software program is getting used to propagate the ransomware.
This means that the menace actors behind the exercise could also be leveraging a number of identified vulnerabilities in ESXi to their benefit, making it crucial that customers transfer rapidly to replace to the newest model. The assaults have but to be attributed to a identified menace actor or group.
“Based mostly on the ransom word, the marketing campaign is linked to a sole menace actor or group,” Arctic Wolf identified. “Extra established ransomware teams sometimes conduct OSINT on potential victims earlier than conducting an intrusion and set the ransom cost based mostly on perceived worth.”
Cybersecurity firm Rapid7 mentioned it discovered 18,581 internet-facing ESXi servers which might be susceptible to CVE-2021-21974, including it additional noticed RansomExx2 actors opportunistically concentrating on inclined ESXi servers.
“Whereas the greenback influence of this specific breach could appear low, cyber attackers proceed to plague organizations by way of demise by a thousand cuts,” Tony Lauro, director of safety know-how and technique at Akamai, mentioned.
“The ESXiArgs ransomware is a first-rate instance of why system directors have to implement patches rapidly after they’re launched, in addition to the lengths that attackers will go to as a way to make their assaults profitable. Nonetheless, patching is only one line of protection to depend on.”