Microsoft on Tuesday stated it took steps to disable pretend Microsoft Accomplice Community (MPN) accounts that have been used for creating malicious OAuth functions as a part of a malicious marketing campaign designed to breach organizations’ cloud environments and steal electronic mail.
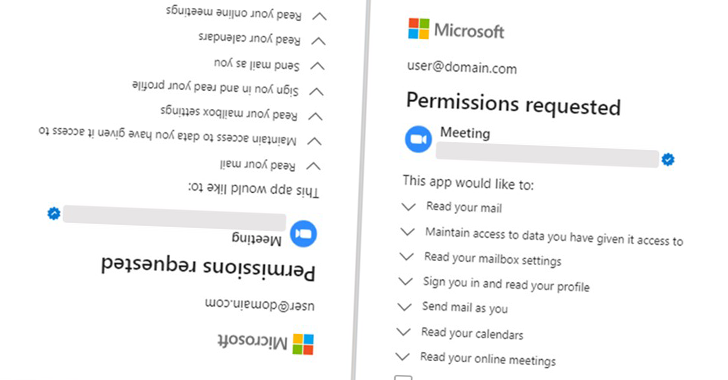
“The functions created by these fraudulent actors have been then utilized in a consent phishing marketing campaign, which tricked customers into granting permissions to the fraudulent apps,” the tech big stated. “This phishing marketing campaign focused a subset of shoppers based totally within the U.Ok. and Eire.”
Consent phishing is a social engineering assault whereby customers are tricked into granting permissions to malicious cloud functions, which may then be weaponized to achieve entry to authentic cloud companies and delicate consumer knowledge.
The Home windows maker stated it grew to become conscious of the marketing campaign on December 15, 2022. It has since alerted affected prospects by way of electronic mail, with the corporate noting that the risk actors abused the consent to exfiltrate mailboxes.
On high of that, Microsoft stated it applied further safety measures to enhance the vetting course of related to the Microsoft Cloud Accomplice Program (previously MPN) and reduce the potential for fraud sooner or later.
The disclosure coincides with a report launched by Proofpoint about how risk actors have efficiently exploited Microsoft’s “verified writer” standing to infiltrate the cloud environments of organizations.
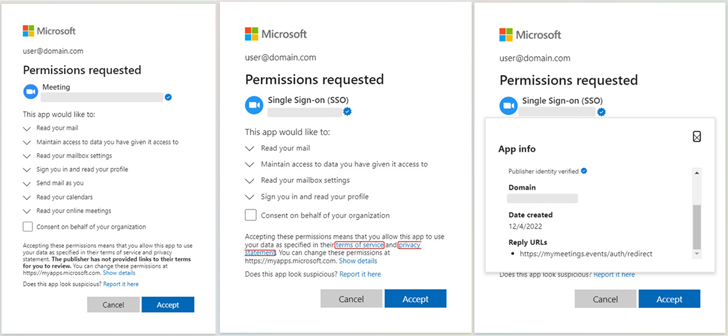
What’s notable in regards to the marketing campaign is that by mimicking standard manufacturers, it was additionally profitable at fooling Microsoft with a purpose to achieve the blue verified badge. “The actor used fraudulent accomplice accounts so as to add a verified writer to OAuth app registrations they created in Azure AD,” the corporate defined.
These assaults, which have been first noticed on December 6, 2022, employed lookalike variations of authentic apps like Zoom to deceive targets into authorizing entry and facilitate knowledge theft. Targets included monetary, advertising, managers, and senior executives.
Proofpoint famous the malicious OAuth apps had “far-reaching delegated permissions” similar to studying emails, adjusting mailbox settings, and getting access to recordsdata and different knowledge linked to the consumer’s account.
It additionally stated that in contrast to a earlier marketing campaign that compromised present Microsoft verified publishers to make the most of OAuth app privileges, the newest assaults are designed to impersonate authentic publishers to grow to be verified and distribute the rogue apps.
Two of the apps in query have been named “Single Signal-on (SSO),” whereas the third app was referred to as “Assembly” in an try and masquerade as video conferencing software program. All three apps, created by three completely different publishers, focused the identical corporations and leveraged the identical attacker-controlled infrastructure.
“The potential affect to organizations contains compromised consumer accounts, knowledge exfiltration, model abuse of impersonated organizations, enterprise electronic mail compromise (BEC) fraud, and mailbox abuse,” the enterprise safety agency stated.
The marketing campaign is claimed to have come to an finish on December 27, 2022, after Proofpoint knowledgeable Microsoft of the assault on December 20 and the apps have been disabled.
The findings reveal the sophistication that has gone into mounting the assault, to not point out bypass Microsoft’s safety protections and misuse the belief customers place in enterprise distributors and repair suppliers.
This isn’t the primary time bogus OAuth apps have been used to focus on Microsoft’s cloud companies. In January 2022, Proofpoint detailed one other risk exercise dubbed OiVaVoii that focused high-level executives to grab management of their accounts.
Then in September 2022, Microsoft revealed that it dismantled an assault that made use of rogue OAuth functions deployed on compromised cloud tenants to finally seize management of Change servers and distribute spam.