New analysis has linked the operations of a politically motivated hacktivist group often known as Moses Workers to a different nascent menace actor named Abraham’s Ax that emerged in November 2022.
That is based mostly on “a number of commonalities throughout the iconography, videography, and leak websites utilized by the teams, suggesting they’re seemingly operated by the identical entity,” Secureworks Counter Menace Unit (CTU) stated in a report shared with The Hacker Information.
Moses Workers, tracked by the cybersecurity agency below the moniker Cobalt Sapling, made its first look on the menace panorama in September 2021 with the purpose of primarily concentrating on Israeli organizations.
The geopolitical group is believed to be sponsored by the Iranian authorities and has since been linked to a string of espionage and sabotage assaults that make use of instruments like StrifeWater RAT and open supply utilities corresponding to DiskCryptor to reap delicate info and lock sufferer information on contaminated hosts.
The crew can be recognized to keep up a leak web site that is used to distribute information stolen from their victims and disseminate their messaging, which incorporates “exposing the crimes of the Zionists in occupied Palestine.”
Now based on Secureworks’ evaluation, “the Abraham’s Ax persona is being utilized in tandem to assault authorities ministries in Saudi Arabia” and that “that is seemingly in response to Saudi Arabia’s management position in bettering relations between Israel and Arab nations.”
For its half, Abraham’s Ax claims to be working on behalf of the Hezbollah Ummah regardless of no proof to again it up. Hezbollah, which implies “Social gathering of Allah” in Arabic, is a Lebanese Shia Islamist political social gathering and militant group that is backed by Iran.
The hanging overlaps within the modus operandi additional elevate the chance that the operators behind Abraham’s Ax are seemingly leveraging the identical customized malware which acts as a cryptographic wiper to encrypt information with out providing a way to get well the info.
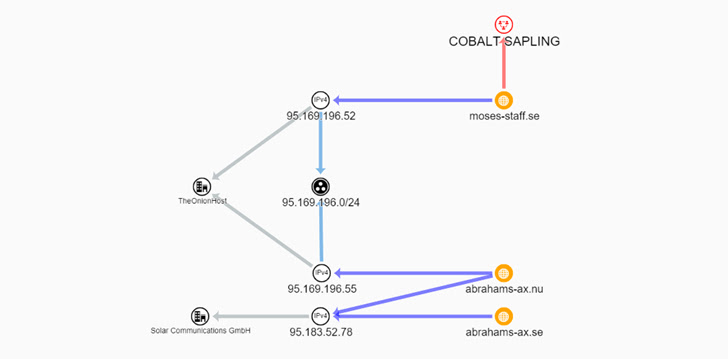
What’s extra, each actors are united of their motivations in that they function with no monetary incentive, with the intrusions taking a extra disruptive tone. The connections between the 2 teams can be evidenced by the very fact the WordPress-based leak websites have been hosted in the identical subnet within the early phases.
“Iran has a historical past of utilizing proxy teams and manufactured personas to focus on regional and worldwide adversaries,” Rafe Pilling, Secureworks principal researcher, stated in a press release.
“During the last couple of years an rising variety of felony and hacktivist group personas have emerged to focus on perceived enemies of Iran whereas offering believable deniability to the Authorities of Iran concerning affiliation or accountability for these assaults. This development is prone to proceed.”