Many in our business are weighing the advantages that software program payments of supplies (SBOMs) may presumably convey to software program high quality and safety. I believe SBOMs are wanted to grasp and assess danger in software program as a result of they need to present visibility into the software program building course of for a given software program system. At some degree, SBOMs exist already for sure merchandise and software program techniques; nonetheless, their software for evaluating high quality and safety as stipulated in Government Order 14028, Enhancing the Nation’s Cybersecurity and up to date federal steerage by the US Workplace of Administration and Price range, the Nationwide Institute of Requirements and Expertise, and the Cybersecurity Infrastructure and Safety Company is pretty new and unproven at scale.
The Royce Invoice That By no means Handed
Round 2013, SBOM laws H.R.5793 – Cyber Provide Chain Administration and Transparency Act (often known as the Royce Invoice) was launched however by no means gained the momentum it wanted to cross as a mandate, invoice, or requirement. The business didn’t then have the urge for food for transparency to handle software program provide chain danger.
The problems this laws would have addressed are outlined within the Congressional File – Extensions of Remarks. These points have now been exacerbated given the overwhelming quantity of complexity and rising dimension in trendy software program improvement, and the growing fee of assaults towards open supply software program. With the growing consumption fee of open supply software program in trendy software program improvement, customers should concentrate on the technical debt in open supply software program tasks that has accrued over time to raised handle software program danger. The thought of extra software program complexity, bigger software program techniques, and mounting technical debt doesn’t bode effectively for the federal authorities’s want for software program integrity and trustworthiness by the software program provide chain.
The truth that the Royce Invoice did not cross could be seen as a missed alternative to handle the rising threats and danger in software program safety on the time. Nearly a decade later, the business remains to be struggling to determine the best way to implement SBOMs and strike the suitable steadiness to make them helpful and never a goal for adversaries to use. This raises main concern in business about whether or not SBOMs are prepared for prime time given the skepticism relating to the present necessities outlined in federal steerage.
SBOM Should Inform About Unknown Threat
One of many challenges for SBOMs is advancing and understanding how dangerous software program is set. I exploit the time period “dangerous” as a result of all software program has vulnerabilities, and the SBOM should be capable of differentiate or present context to the extent of danger related to a software program element, whether or not in isolation or as soon as it has been carried out and built-in right into a software program system. To easily say you’ll be able to’t use this software program element as a result of it has CVEs (frequent vulnerabilities and exposures) related to it turns into moot as a result of all software program can have vulnerabilities. SBOMs should be capable of succinctly qualify which CVEs are essentially the most harmful and exploitable given the context the software program might be carried out and used — the element operate (logging, encryption, entry management, authorization), the atmosphere, and whether or not it may be hardened to scale back a given assault floor. The way in which wherein software program elements are built-in right into a system issues as a result of software program elements could be carried out poorly or incorrectly, exposing vulnerabilities in software program techniques.
Utilizing CVEs to determine a safety baseline for open supply software program consumption make sense; nonetheless, tallying a bunch of CVEs to find out what software program is much less dangerous or riskier solely focuses on the “identified knowns” (as proven within the determine beneath) and does little or no to assist organizations perceive what weaknesses are lurking which will expose vulnerabilities and affect the general hygiene of that software program element (over a time frame). Moreover, the present state of observe relating to SBOMs would not encourage software program provide chainers to grasp the defect proneness or assault proneness charges related to software program. That is essential as a result of some software program elements are extremely focused and require vital patching resulting from inherent technical debt, low code high quality, and safety points that expose vulnerabilities. Extra patching means builders and engineering groups are spending much less time on creating and delivering new options and performance to prospects.
Defect proneness refers back to the chance {that a} software program element might be faulty after a software program product is launched. There are numerous socio-technical components that contribute to defect proneness similar to low code high quality and design flaws. Assault proneness refers back to the fee at which software program elements could be efficiently exploited, or the chance that software program elements will include exploitable weaknesses — bug, defect, or flaw — or vulnerabilities.
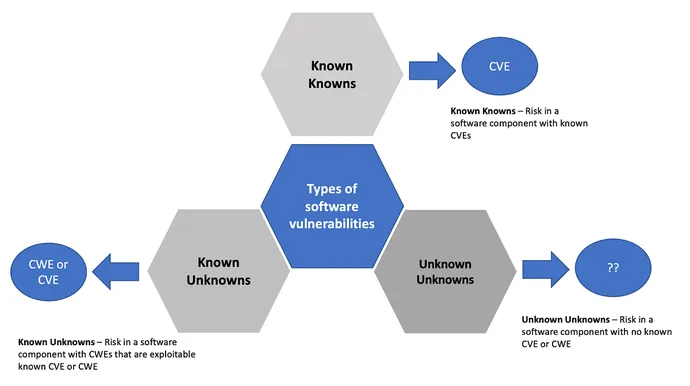
SBOM options should give organizations visibility into potential danger for a given software program element as proven within the determine above, serving to organizations make knowledgeable choices about which software program elements to make use of and which software program elements to keep away from. As an illustration, recommendation within the Nationwide Safety Company (NSA) Cybersecurity Info Sheet encourages builders to keep away from utilizing software program developed in C and C++ as a result of these programming languages weren’t supposed to implement good reminiscence administration checks. It will likely be attention-grabbing to see how this recommendation will have an effect on the software program provide chain, primarily for embedded security crucial techniques, and whether or not suppliers will flip to programming languages which are reminiscence secure, similar to Rust and Go.
Go Deeper to Information SBOM
SBOMs are usually not going away, so it is crucial all of us collaborate and accomplice to enhance software program safety. This will require growing instruments and requirements that may enrich SBOMs and supply deeper evaluation and perception in regards to the traits of software program that assist inform about software program danger. It will assist organizations successfully consider and attest to software program integrity, in addition to different software program assurance properties. Finally, it is essential for software program provide chainers to grasp not simply the chance related to a given software program element however the potential upkeep related to utilizing that software program element over a time frame, given the challenges in business to remediate vulnerabilities in software program in a well timed style. Using defect and assault proneness charges may present actionable intelligence that helps decrease the consumption of dangerous software program with poor hygiene, and information software program provide chainers in constructing software program techniques which are extra resilient to cyberattacks.
In principle, software program elements with excessive defect and assault proneness charges needs to be averted to assist stimulate and encourage the usage of alternate options with higher hygiene. In my view, SBOMs do not enhance code high quality and safety instantly, however they will make software program provide chainers extra conscious of danger of their software program building course of. Enhancing code high quality and safety for open supply software program requires a tradition shift provided that having many eyes doesn’t make all bugs shallow.


