The Zerobot DDoS botnet has acquired substantial updates that develop on its means to focus on extra internet-connected gadgets and scale its community.
Microsoft Menace Intelligence Middle (MSTIC) is monitoring the continued menace underneath the moniker DEV-1061, its designation for unknown, rising, or creating exercise clusters.
Zerobot, first documented by Fortinet FortiGuard Labs earlier this month, is a Go-based malware that propagates via vulnerabilities in net purposes and IoT gadgets like firewalls, routers, and cameras.
“The newest distribution of Zerobot consists of extra capabilities, resembling exploiting vulnerabilities in Apache and Apache Spark (CVE-2021-42013 and CVE-2022-33891 respectively), and new DDoS assault capabilities,” Microsoft researchers stated.
Additionally known as ZeroStresser by its operators, the malware is obtainable as a DDoS-for-hire service to different legal actors, with the botnet marketed on social media by its operators.
Microsoft stated that one area with connections to Zerobot – zerostresser[.]com – was among the many 48 domains that have been seized by the U.S. Federal Bureau of Investigation (FBI) this month for providing DDoS assault options to paying clients.
The newest model of Zerobot noticed by Microsoft not solely targets unpatched and improperly secured gadgets, but additionally makes an attempt to brute-force over SSH and Telnet on ports 23 and 2323 for spreading to different hosts.
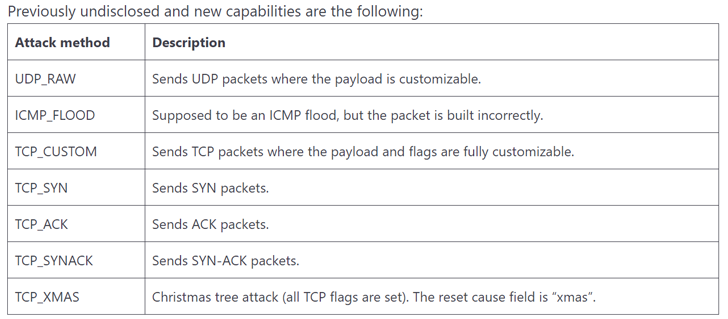
The record of newly added identified flaws exploited by Zerobot 1.1 is as follows –
- CVE-2017-17105 (CVSS rating: 9.8) – A command injection vulnerability in Zivif PR115-204-P-RS
- CVE-2019-10655 (CVSS rating: 9.8) – An unauthenticated distant code execution vulnerability in Grandstream GAC2500, GXP2200, GVC3202, GXV3275, and GXV3240
- CVE-2020-25223 (CVSS rating: 9.8) – A distant code execution vulnerability within the WebAdmin of Sophos SG UTM
- CVE-2021-42013 (CVSS rating: 9.8) – A distant code execution vulnerability in Apache HTTP Server
- CVE-2022-31137 (CVSS rating: 9.8) – A distant code execution vulnerability in Roxy-WI
- CVE-2022-33891 (CVSS rating: 8.8) – An unauthenticated command injection vulnerability in Apache Spark
- ZSL-2022-5717 (CVSS rating: N/A) – A distant root command injection vulnerability in MiniDVBLinux
Upon profitable an infection, the assaults chain proceeds to obtain a binary named “zero” for a selected CPU structure that permits it to self-propagate to extra vulnerable programs uncovered on-line.
Moreover, Zerobot is claimed to proliferate by scanning and compromising gadgets with identified vulnerabilities that aren’t included within the malware executable, resembling CVE-2022-30023, a command injection vulnerability in Tenda GPON AC1200 routers.
Zerobot 1.1 additional incorporates seven new DDoS assault strategies by making use of protocols resembling UDP, ICMP, and TCP, indicating “steady evolution and speedy addition of recent capabilities.”
“The shift towards malware as a service within the cyber financial system has industrialized assaults and has made it simpler for attackers to buy and use malware, set up and keep entry to compromised networks, and make the most of ready-made instruments to carry out their assaults,” the tech large stated.